
Corben Leo
@hacking.bsky.social
Can see why there haven’t been any sticky Twitter competitors
July 2, 2023 at 4:25 AM
Can see why there haven’t been any sticky Twitter competitors
Super insane. Kinda scary, curious about the ramifications of violent games that look so realistic
April 25, 2023 at 10:05 AM
Super insane. Kinda scary, curious about the ramifications of violent games that look so realistic
It’d be an interesting read! Why not?
Bootstrapped businesses can’t play the same game that venture-backed businesses play
Bootstrapped businesses can’t play the same game that venture-backed businesses play
April 9, 2023 at 7:36 PM
It’d be an interesting read! Why not?
Bootstrapped businesses can’t play the same game that venture-backed businesses play
Bootstrapped businesses can’t play the same game that venture-backed businesses play
TLDR;
- In a bug bounty program (telecommunications company)
- Scanned their IPV4 Ranges
- Found a webserver that said "███ Cable System"
- Directory brute-force found /admin/accounts/
- The endpoint set a valid admin JSESSIONID
https://bsky.app/profile/hacking.bsky.social/post/3jsunjzfyl22o
- In a bug bounty program (telecommunications company)
- Scanned their IPV4 Ranges
- Found a webserver that said "███ Cable System"
- Directory brute-force found /admin/accounts/
- The endpoint set a valid admin JSESSIONID
https://bsky.app/profile/hacking.bsky.social/post/3jsunjzfyl22o
In 2010, WikiLeaks released a classified document.
A list of infrastructure critical to U.S national security.
The government listed a Trans-Atlantic cable.
3 years ago,
19-year-old me gained ADMIN access to that cable (and another; shared codebase).
Here's how I did it:
A list of infrastructure critical to U.S national security.
The government listed a Trans-Atlantic cable.
3 years ago,
19-year-old me gained ADMIN access to that cable (and another; shared codebase).
Here's how I did it:

April 8, 2023 at 3:39 PM
TLDR;
- In a bug bounty program (telecommunications company)
- Scanned their IPV4 Ranges
- Found a webserver that said "███ Cable System"
- Directory brute-force found /admin/accounts/
- The endpoint set a valid admin JSESSIONID
https://bsky.app/profile/hacking.bsky.social/post/3jsunjzfyl22o
- In a bug bounty program (telecommunications company)
- Scanned their IPV4 Ranges
- Found a webserver that said "███ Cable System"
- Directory brute-force found /admin/accounts/
- The endpoint set a valid admin JSESSIONID
https://bsky.app/profile/hacking.bsky.social/post/3jsunjzfyl22o
10/ I reported it immediately and started pinging their program manager.
It was the best response I've ever gotten.
And will ever get
It was the best response I've ever gotten.
And will ever get

April 8, 2023 at 3:38 PM
10/ I reported it immediately and started pinging their program manager.
It was the best response I've ever gotten.
And will ever get
It was the best response I've ever gotten.
And will ever get
9/ I clicked through the menus to see if I was actually authenticated.
I was. FULLY. AUTHENTICATED.
On that same IP range,
They had ANOTHER system for ANOTHER cable.
I tried the same attack.
IT WORKED!
I had admin access to TWO. Different. Cables.
I was in disbelief.
So,
I was. FULLY. AUTHENTICATED.
On that same IP range,
They had ANOTHER system for ANOTHER cable.
I tried the same attack.
IT WORKED!
I had admin access to TWO. Different. Cables.
I was in disbelief.
So,
April 8, 2023 at 3:37 PM
9/ I clicked through the menus to see if I was actually authenticated.
I was. FULLY. AUTHENTICATED.
On that same IP range,
They had ANOTHER system for ANOTHER cable.
I tried the same attack.
IT WORKED!
I had admin access to TWO. Different. Cables.
I was in disbelief.
So,
I was. FULLY. AUTHENTICATED.
On that same IP range,
They had ANOTHER system for ANOTHER cable.
I tried the same attack.
IT WORKED!
I had admin access to TWO. Different. Cables.
I was in disbelief.
So,
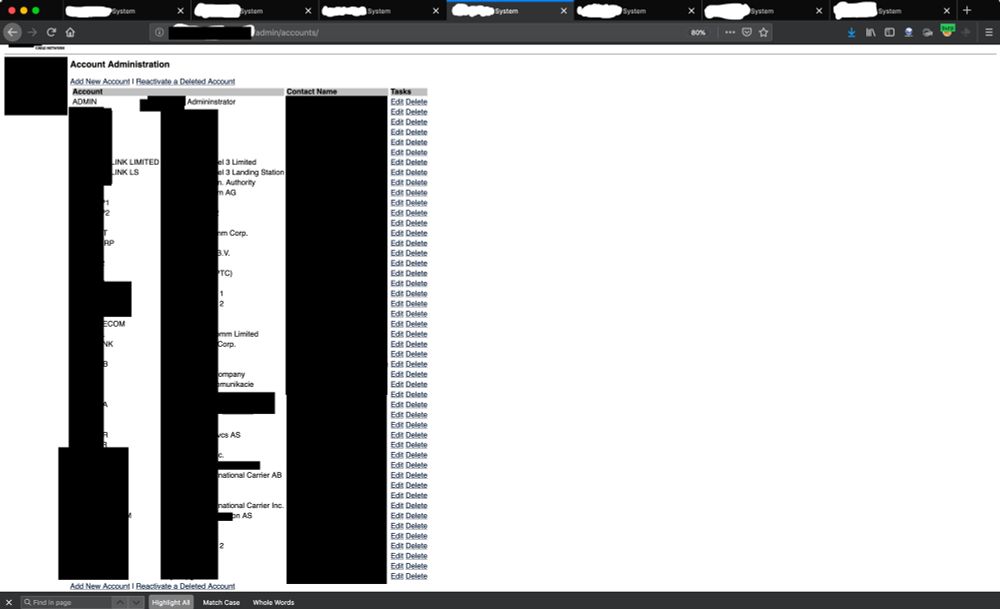
8/ Redirected to the home page.
Second visit:
> HTTP/1.1 200 OK
> --- snip ---
> <title>Account Administration</title>
HOLY **** IT WORKED.
This is a HIGHLY redacted version of what I saw:
So,
Second visit:
> HTTP/1.1 200 OK
> --- snip ---
> <title>Account Administration</title>
HOLY **** IT WORKED.
This is a HIGHLY redacted version of what I saw:
So,
April 8, 2023 at 3:37 PM
8/ Redirected to the home page.
Second visit:
> HTTP/1.1 200 OK
> --- snip ---
> <title>Account Administration</title>
HOLY **** IT WORKED.
This is a HIGHLY redacted version of what I saw:
So,
Second visit:
> HTTP/1.1 200 OK
> --- snip ---
> <title>Account Administration</title>
HOLY **** IT WORKED.
This is a HIGHLY redacted version of what I saw:
So,
7/ It's probably worthless. Right?
I was intrigued enough.
So I decided to visit the endpoint in my browser.
Twice.
1st - To set the JSESSIONID cookie in my browser.
2nd - To see if the cookie was valid & used for authentication.
1st visit: http://<IP>/admin/accounts/ and
I was intrigued enough.
So I decided to visit the endpoint in my browser.
Twice.
1st - To set the JSESSIONID cookie in my browser.
2nd - To see if the cookie was valid & used for authentication.
1st visit: http://<IP>/admin/accounts/ and
April 8, 2023 at 3:36 PM
7/ It's probably worthless. Right?
I was intrigued enough.
So I decided to visit the endpoint in my browser.
Twice.
1st - To set the JSESSIONID cookie in my browser.
2nd - To see if the cookie was valid & used for authentication.
1st visit: http://<IP>/admin/accounts/ and
I was intrigued enough.
So I decided to visit the endpoint in my browser.
Twice.
1st - To set the JSESSIONID cookie in my browser.
2nd - To see if the cookie was valid & used for authentication.
1st visit: http://<IP>/admin/accounts/ and
6/ Let's see if there are more directories down /admin/
Directory-Bruteforcing found /accounts/.
This redirected to the login page.
I was about to brute-force JSP files when I realized something unique in the response.
A header.
> Set-Cookie: JSESSIONID=<id>;
That's weird.
Directory-Bruteforcing found /accounts/.
This redirected to the login page.
I was about to brute-force JSP files when I realized something unique in the response.
A header.
> Set-Cookie: JSESSIONID=<id>;
That's weird.
April 8, 2023 at 3:36 PM
6/ Let's see if there are more directories down /admin/
Directory-Bruteforcing found /accounts/.
This redirected to the login page.
I was about to brute-force JSP files when I realized something unique in the response.
A header.
> Set-Cookie: JSESSIONID=<id>;
That's weird.
Directory-Bruteforcing found /accounts/.
This redirected to the login page.
I was about to brute-force JSP files when I realized something unique in the response.
A header.
> Set-Cookie: JSESSIONID=<id>;
That's weird.
5/ The directory /admin/
Remember, it's running Apache Tomcat.
I built a wordlist for .jsp files using BigQuery. (Learned from @assetnote's commonspeak)
Bruteforcing found a few JSP files, but they all redirected to the login page.
Gah. Well,
Remember, it's running Apache Tomcat.
I built a wordlist for .jsp files using BigQuery. (Learned from @assetnote's commonspeak)
Bruteforcing found a few JSP files, but they all redirected to the login page.
Gah. Well,
April 8, 2023 at 3:35 PM
5/ The directory /admin/
Remember, it's running Apache Tomcat.
I built a wordlist for .jsp files using BigQuery. (Learned from @assetnote's commonspeak)
Bruteforcing found a few JSP files, but they all redirected to the login page.
Gah. Well,
Remember, it's running Apache Tomcat.
I built a wordlist for .jsp files using BigQuery. (Learned from @assetnote's commonspeak)
Bruteforcing found a few JSP files, but they all redirected to the login page.
Gah. Well,
4/ "login.jsp"
Ok! It was a Tomcat webserver
I didn't have credentials. Obviously.
I started with directory brute-forcing.
Used @joohoi's ffuf & filtered by the number of response words on the 404 page.
It found several directories.
One that stuck out was
Ok! It was a Tomcat webserver
I didn't have credentials. Obviously.
I started with directory brute-forcing.
Used @joohoi's ffuf & filtered by the number of response words on the 404 page.
It found several directories.
One that stuck out was
April 8, 2023 at 3:35 PM
4/ "login.jsp"
Ok! It was a Tomcat webserver
I didn't have credentials. Obviously.
I started with directory brute-forcing.
Used @joohoi's ffuf & filtered by the number of response words on the 404 page.
It found several directories.
One that stuck out was
Ok! It was a Tomcat webserver
I didn't have credentials. Obviously.
I started with directory brute-forcing.
Used @joohoi's ffuf & filtered by the number of response words on the 404 page.
It found several directories.
One that stuck out was
3/ "███ Cable System" (I have to redact this)
So, I visited the server in my browser.
The home page said
> "Welcome to the ███ Management System"
No way. This isn't really online is it?
Underneath was a link:
"Log in to ███"
Clicked it and it brought me to
So, I visited the server in my browser.
The home page said
> "Welcome to the ███ Management System"
No way. This isn't really online is it?
Underneath was a link:
"Log in to ███"
Clicked it and it brought me to
April 8, 2023 at 3:35 PM
3/ "███ Cable System" (I have to redact this)
So, I visited the server in my browser.
The home page said
> "Welcome to the ███ Management System"
No way. This isn't really online is it?
Underneath was a link:
"Log in to ███"
Clicked it and it brought me to
So, I visited the server in my browser.
The home page said
> "Welcome to the ███ Management System"
No way. This isn't really online is it?
Underneath was a link:
"Log in to ███"
Clicked it and it brought me to
2/ I searched the company's name on bgp.he\.net
Saved their IP ranges.
I ran masscan, probed for HTTP(s) servers, and grabbed the HTTP titles.
Looked something like:
$ masscan -p 80,443 -iL ranges -oL out.txt
$ cat out.txt | httpx -title
One title stuck out:
Saved their IP ranges.
I ran masscan, probed for HTTP(s) servers, and grabbed the HTTP titles.
Looked something like:
$ masscan -p 80,443 -iL ranges -oL out.txt
$ cat out.txt | httpx -title
One title stuck out:
April 8, 2023 at 3:34 PM
2/ I searched the company's name on bgp.he\.net
Saved their IP ranges.
I ran masscan, probed for HTTP(s) servers, and grabbed the HTTP titles.
Looked something like:
$ masscan -p 80,443 -iL ranges -oL out.txt
$ cat out.txt | httpx -title
One title stuck out:
Saved their IP ranges.
I ran masscan, probed for HTTP(s) servers, and grabbed the HTTP titles.
Looked something like:
$ masscan -p 80,443 -iL ranges -oL out.txt
$ cat out.txt | httpx -title
One title stuck out:
1/ It began with a bug bounty program.
Of a telecommunications company (that I can't name publicly).
As some of you may know, I love recon.
I had already done subdomain enumeration.
The next step was to scan their IP ranges.
So,
Of a telecommunications company (that I can't name publicly).
As some of you may know, I love recon.
I had already done subdomain enumeration.
The next step was to scan their IP ranges.
So,
April 8, 2023 at 3:34 PM
1/ It began with a bug bounty program.
Of a telecommunications company (that I can't name publicly).
As some of you may know, I love recon.
I had already done subdomain enumeration.
The next step was to scan their IP ranges.
So,
Of a telecommunications company (that I can't name publicly).
As some of you may know, I love recon.
I had already done subdomain enumeration.
The next step was to scan their IP ranges.
So,

