
Views are strictly my own
securitylabs.datadoghq.com/articles/bey...

securitylabs.datadoghq.com/articles/bey...
fwdcloudsec.org/conference/n...
@sethsec.bsky.social
@siigil.bsky.social
@gregfoss.com
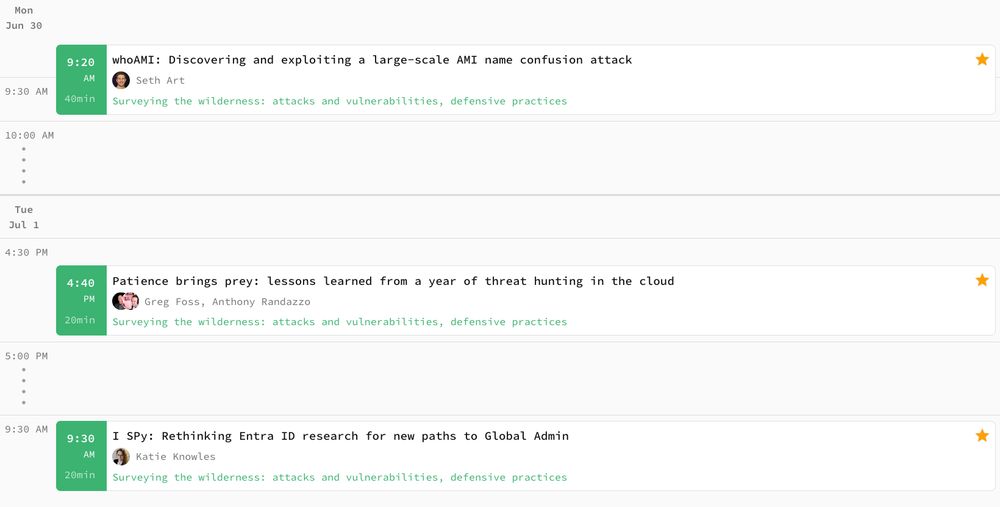
fwdcloudsec.org/conference/n...
@sethsec.bsky.social
@siigil.bsky.social
@gregfoss.com
bit.ly/datadog-detect
Our lineup is incredible with experts in the field of detection, response and threat intelligence.

bit.ly/datadog-detect
Our lineup is incredible with experts in the field of detection, response and threat intelligence.
Don’t miss other @securitylabs.datadoghq.com talks from @siigil.bsky.social on EntraID escalation and @sethsec.bsky.social on AMI name confusion as well!

Don’t miss other @securitylabs.datadoghq.com talks from @siigil.bsky.social on EntraID escalation and @sethsec.bsky.social on AMI name confusion as well!
www.datadoghq.com/event/rsa202...

www.datadoghq.com/event/rsa202...
Datadog has unique visibility into threat actor activity targeting cloud environments and this report highlights our key findings from Q4 2024.
securitylabs.datadoghq.com/articles/202...

Datadog has unique visibility into threat actor activity targeting cloud environments and this report highlights our key findings from Q4 2024.
securitylabs.datadoghq.com/articles/202...
This includes several cyber committees, like CISA's advisory panel and the Cyber Safety Review Board, which was investigating Salt Typhoon.
That review is "dead," person familiar says.
www.documentcloud.org/documents/25...

This includes several cyber committees, like CISA's advisory panel and the Cyber Safety Review Board, which was investigating Salt Typhoon.
That review is "dead," person familiar says.
www.documentcloud.org/documents/25...
securitylabs.datadoghq.com/articles/tal...
This post describes an attacker that we've observed in the wild, including a malicious AWS account ID used to create a backdoor IAM role.
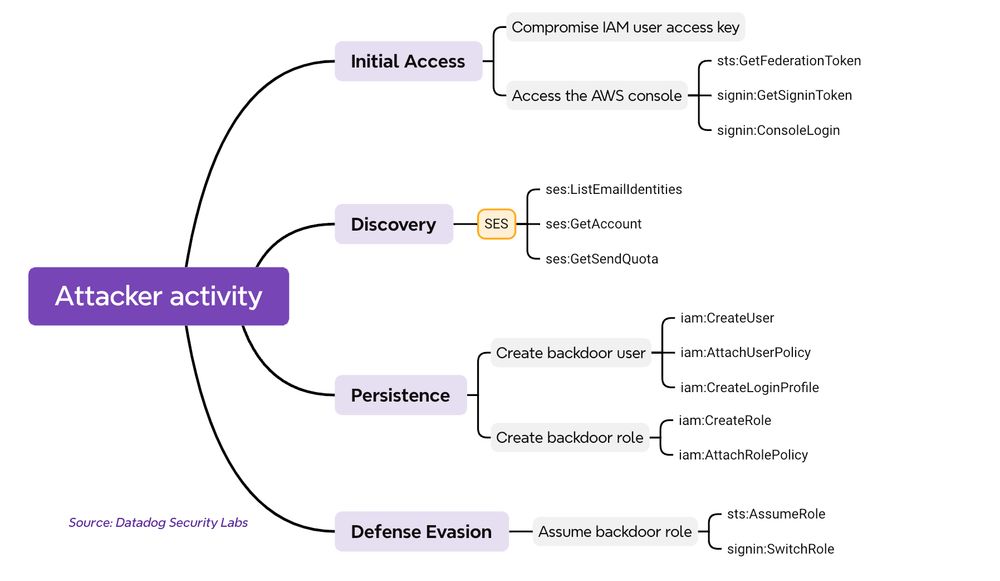
securitylabs.datadoghq.com/articles/tal...
This post describes an attacker that we've observed in the wild, including a malicious AWS account ID used to create a backdoor IAM role.
securitylabs.datadoghq.com/articles/int...

securitylabs.datadoghq.com/articles/int...
securitylabs.datadoghq.com/articles/goo...
by @christophetd.fr

securitylabs.datadoghq.com/articles/goo...
by @christophetd.fr
There's also talks going back to 2016 in case you really want to watch a lot of container security videos!
There's also talks going back to 2016 in case you really want to watch a lot of container security videos!
go.bsky.app/8XpcFm5
go.bsky.app/8XpcFm5

