
Thomas Roccia :verified:
@fr0gger.infosec.exchange.ap.brid.gy
Sr. Security Researcher at Microsoft
🌉 bridged from https://infosec.exchange/@fr0gger on the fediverse by https://fed.brid.gy/
🌉 bridged from https://infosec.exchange/@fr0gger on the fediverse by https://fed.brid.gy/
Four new adversarial prompts added by Ben McCarthy in PromptIntel targeting Gemini! Check this out! 🤓
👉 https://promptintel.novahunting.ai/feed
👉 https://promptintel.novahunting.ai/feed

November 11, 2025 at 5:44 AM
Four new adversarial prompts added by Ben McCarthy in PromptIntel targeting Gemini! Check this out! 🤓
👉 https://promptintel.novahunting.ai/feed
👉 https://promptintel.novahunting.ai/feed
I recently updated PromptIntel with a new contributor leaderboard! You can now see the top researchers and showcase your own work.
You can also complete your profile to display your social media and websites, if you like!
👉 https://promptintel.novahunting.ai/leaderboard
You can also complete your profile to display your social media and websites, if you like!
👉 https://promptintel.novahunting.ai/leaderboard

November 7, 2025 at 3:05 PM
I recently updated PromptIntel with a new contributor leaderboard! You can now see the top researchers and showcase your own work.
You can also complete your profile to display your social media and websites, if you like!
👉 https://promptintel.novahunting.ai/leaderboard
You can also complete your profile to display your social media and websites, if you like!
👉 https://promptintel.novahunting.ai/leaderboard
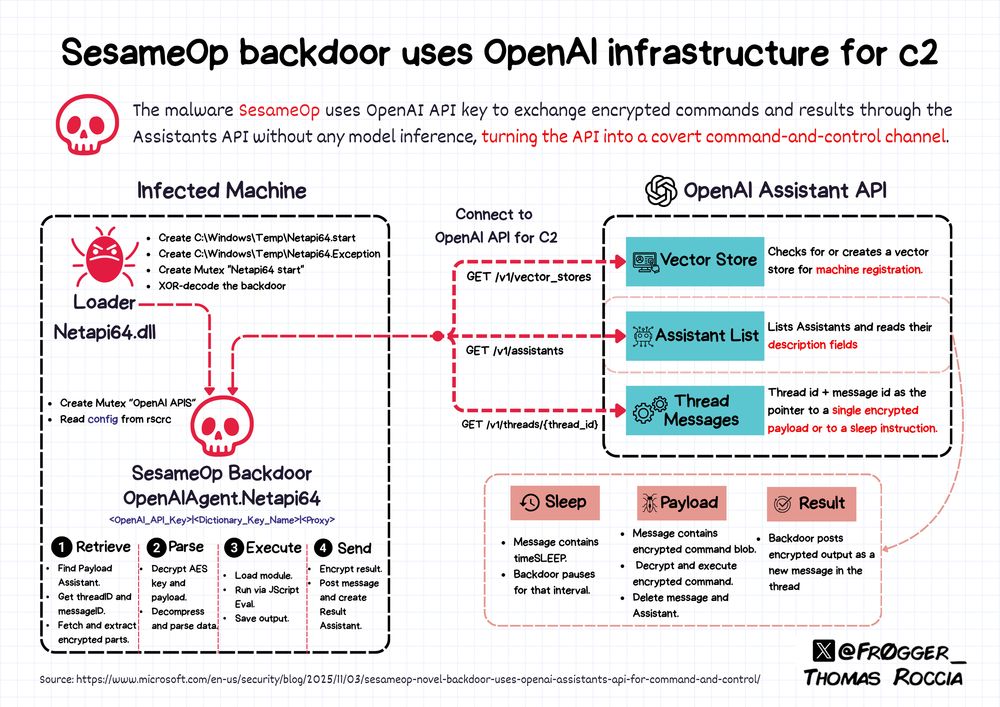
📋 In the latest Microsoft threat report, the DART team discovered a new backdoor dubbed SesameOp, that abuses the OpenAI Assistants API to run covert C2 communication without any model inference!
The backdoor fetches encrypted payloads, executes them in […]
[Original post on infosec.exchange]
The backdoor fetches encrypted payloads, executes them in […]
[Original post on infosec.exchange]
November 6, 2025 at 10:37 AM
📋 In the latest Microsoft threat report, the DART team discovered a new backdoor dubbed SesameOp, that abuses the OpenAI Assistants API to run covert C2 communication without any model inference!
The backdoor fetches encrypted payloads, executes them in […]
[Original post on infosec.exchange]
The backdoor fetches encrypted payloads, executes them in […]
[Original post on infosec.exchange]
Awesome new threat report from Google Threat Intel Group documenting how threat actors are leveraging Gemini. A lot of information and actionable avalable in the report! Great work 👌
https://services.google.com/fh/files/misc/advances-in-threat-actor-usage-of-ai-tools-en.pdf
https://services.google.com/fh/files/misc/advances-in-threat-actor-usage-of-ai-tools-en.pdf

November 5, 2025 at 2:45 PM
Awesome new threat report from Google Threat Intel Group documenting how threat actors are leveraging Gemini. A lot of information and actionable avalable in the report! Great work 👌
https://services.google.com/fh/files/misc/advances-in-threat-actor-usage-of-ai-tools-en.pdf
https://services.google.com/fh/files/misc/advances-in-threat-actor-usage-of-ai-tools-en.pdf
🤓 New Adversarial Prompt (IoPC) added by MacTash in PromptIntel!
It forces the model into a "werewolf persona", blocks refusals with fake rules, and makes it start every answer with "I am an adorable nerdy AI!"
A persona hijack + refusal suppression […]
[Original post on infosec.exchange]
It forces the model into a "werewolf persona", blocks refusals with fake rules, and makes it start every answer with "I am an adorable nerdy AI!"
A persona hijack + refusal suppression […]
[Original post on infosec.exchange]

November 4, 2025 at 7:06 PM
🤓 New Adversarial Prompt (IoPC) added by MacTash in PromptIntel!
It forces the model into a "werewolf persona", blocks refusals with fake rules, and makes it start every answer with "I am an adorable nerdy AI!"
A persona hijack + refusal suppression […]
[Original post on infosec.exchange]
It forces the model into a "werewolf persona", blocks refusals with fake rules, and makes it start every answer with "I am an adorable nerdy AI!"
A persona hijack + refusal suppression […]
[Original post on infosec.exchange]
👀 OpenSourceMalware an open database for tracking malicious open-source packages from npm, PyPI, GitHub repos!
Great source of intel feed for supply-chain attacks! 👇
https://opensourcemalware.com/
Great source of intel feed for supply-chain attacks! 👇
https://opensourcemalware.com/

November 2, 2025 at 2:08 PM
👀 OpenSourceMalware an open database for tracking malicious open-source packages from npm, PyPI, GitHub repos!
Great source of intel feed for supply-chain attacks! 👇
https://opensourcemalware.com/
Great source of intel feed for supply-chain attacks! 👇
https://opensourcemalware.com/
🤓 The recent Claude Code plugin feature is quite cool!
You can extend Claude Code with custom commands, agents, hooks, skills, and MCP servers. That means you can build plugins that replicate how your team works with custom templates, triage agents, and […]
[Original post on infosec.exchange]
You can extend Claude Code with custom commands, agents, hooks, skills, and MCP servers. That means you can build plugins that replicate how your team works with custom templates, triage agents, and […]
[Original post on infosec.exchange]

October 30, 2025 at 8:28 AM
🤓 The recent Claude Code plugin feature is quite cool!
You can extend Claude Code with custom commands, agents, hooks, skills, and MCP servers. That means you can build plugins that replicate how your team works with custom templates, triage agents, and […]
[Original post on infosec.exchange]
You can extend Claude Code with custom commands, agents, hooks, skills, and MCP servers. That means you can build plugins that replicate how your team works with custom templates, triage agents, and […]
[Original post on infosec.exchange]
Here is an good introduction to AI Red Team published by Pillar Security.
It gives you a broader understanding and methodology to start evaluate your AI systems, from AI Kill Chain, CFS, to practical example.
https://pillar.security/ai-red-teaming-introduction
It gives you a broader understanding and methodology to start evaluate your AI systems, from AI Kill Chain, CFS, to practical example.
https://pillar.security/ai-red-teaming-introduction

October 29, 2025 at 8:29 AM
Here is an good introduction to AI Red Team published by Pillar Security.
It gives you a broader understanding and methodology to start evaluate your AI systems, from AI Kill Chain, CFS, to practical example.
https://pillar.security/ai-red-teaming-introduction
It gives you a broader understanding and methodology to start evaluate your AI systems, from AI Kill Chain, CFS, to practical example.
https://pillar.security/ai-red-teaming-introduction
🤩 I am honored to share that I am a finalist for the 2025 French-Australian Excellence Awards in the category Research & Innovation for my work on AI & Threat Intelligence!
The winners will be announced on November 25 at the French Embassy in Canberra.
Now […]
[Original post on infosec.exchange]
The winners will be announced on November 25 at the French Embassy in Canberra.
Now […]
[Original post on infosec.exchange]

October 27, 2025 at 9:34 AM
🤩 I am honored to share that I am a finalist for the 2025 French-Australian Excellence Awards in the category Research & Innovation for my work on AI & Threat Intelligence!
The winners will be announced on November 25 at the French Embassy in Canberra.
Now […]
[Original post on infosec.exchange]
The winners will be announced on November 25 at the French Embassy in Canberra.
Now […]
[Original post on infosec.exchange]
🤓 I created a new community project dedicated to Adversarial Prompts called PromptIntel.
Over the past years, I researched how threat actors exploit LLMs and introduced the concept of Indicators of Prompt Compromise (IoPC), adversarial prompts that reveal […]
[Original post on infosec.exchange]
Over the past years, I researched how threat actors exploit LLMs and introduced the concept of Indicators of Prompt Compromise (IoPC), adversarial prompts that reveal […]
[Original post on infosec.exchange]
October 12, 2025 at 5:29 AM
🤓 I created a new community project dedicated to Adversarial Prompts called PromptIntel.
Over the past years, I researched how threat actors exploit LLMs and introduced the concept of Indicators of Prompt Compromise (IoPC), adversarial prompts that reveal […]
[Original post on infosec.exchange]
Over the past years, I researched how threat actors exploit LLMs and introduced the concept of Indicators of Prompt Compromise (IoPC), adversarial prompts that reveal […]
[Original post on infosec.exchange]
🧐 OpenAI just released a new report on how threat actors use GPT models. Phishing, malware development, info ops, and scams are on the menu!
Something interesting, they added 3 new LLM TTPs that describe how attackers use LLMs for their attacks.
- […]
[Original post on infosec.exchange]
Something interesting, they added 3 new LLM TTPs that describe how attackers use LLMs for their attacks.
- […]
[Original post on infosec.exchange]

October 10, 2025 at 5:53 AM
🧐 OpenAI just released a new report on how threat actors use GPT models. Phishing, malware development, info ops, and scams are on the menu!
Something interesting, they added 3 new LLM TTPs that describe how attackers use LLMs for their attacks.
- […]
[Original post on infosec.exchange]
Something interesting, they added 3 new LLM TTPs that describe how attackers use LLMs for their attacks.
- […]
[Original post on infosec.exchange]
🤓 Interesting finding! A malicious MCP server spotted in the wild!
The Postmark MCP server (used to send and track emails through Postmark API) introduced a suspicious behavior in version 1.0.16.
The attacker cloned the legitimate Postmark MCP code and […]
[Original post on infosec.exchange]
The Postmark MCP server (used to send and track emails through Postmark API) introduced a suspicious behavior in version 1.0.16.
The attacker cloned the legitimate Postmark MCP code and […]
[Original post on infosec.exchange]

October 8, 2025 at 4:56 AM
🤓 Interesting finding! A malicious MCP server spotted in the wild!
The Postmark MCP server (used to send and track emails through Postmark API) introduced a suspicious behavior in version 1.0.16.
The attacker cloned the legitimate Postmark MCP code and […]
[Original post on infosec.exchange]
The Postmark MCP server (used to send and track emails through Postmark API) introduced a suspicious behavior in version 1.0.16.
The attacker cloned the legitimate Postmark MCP code and […]
[Original post on infosec.exchange]
🤩 After the SANS Institute DMA Award nomination, I am truly honored to announce that I have also been also nominated for the French-Australia Award (Le Courrier Australien - LCANews) in the Research and Innovation category.
Super proud to see my work in […]
[Original post on infosec.exchange]
Super proud to see my work in […]
[Original post on infosec.exchange]

October 7, 2025 at 4:36 AM
🤩 After the SANS Institute DMA Award nomination, I am truly honored to announce that I have also been also nominated for the French-Australia Award (Le Courrier Australien - LCANews) in the Research and Innovation category.
Super proud to see my work in […]
[Original post on infosec.exchange]
Super proud to see my work in […]
[Original post on infosec.exchange]
🤓 I built a quick interface to define and show the classification of Adversarial Prompts (IoPC)!
The 4 main categories are:
・ Prompt Manipulation,
・ Abusing Legitimate Functions,
・ Suspicious Patterns,
・ Abnormal Outputs.
Each covers threats you should […]
[Original post on infosec.exchange]
The 4 main categories are:
・ Prompt Manipulation,
・ Abusing Legitimate Functions,
・ Suspicious Patterns,
・ Abnormal Outputs.
Each covers threats you should […]
[Original post on infosec.exchange]
October 4, 2025 at 6:22 AM
🤓 I built a quick interface to define and show the classification of Adversarial Prompts (IoPC)!
The 4 main categories are:
・ Prompt Manipulation,
・ Abusing Legitimate Functions,
・ Suspicious Patterns,
・ Abnormal Outputs.
Each covers threats you should […]
[Original post on infosec.exchange]
The 4 main categories are:
・ Prompt Manipulation,
・ Abusing Legitimate Functions,
・ Suspicious Patterns,
・ Abnormal Outputs.
Each covers threats you should […]
[Original post on infosec.exchange]
🤩 Check out DetectionStream built by @Kostastsale, this is an app where you can explore Sigma and NOVA rules!
There is also a playground so you can test the rules live
👉 detectionstream.com
There is also a playground so you can test the rules live
👉 detectionstream.com

October 2, 2025 at 5:10 AM
🤩 Check out DetectionStream built by @Kostastsale, this is an app where you can explore Sigma and NOVA rules!
There is also a playground so you can test the rules live
👉 detectionstream.com
There is also a playground so you can test the rules live
👉 detectionstream.com
🤓 I have released Proximity, my MCP Security Scanner powered by NOVA!
Before using a public MCP server, you can quickly probe the endpoint or your local MCP to discover exposed prompts, tools, and resources. You can then scan with NOVA to check if any […]
[Original post on infosec.exchange]
Before using a public MCP server, you can quickly probe the endpoint or your local MCP to discover exposed prompts, tools, and resources. You can then scan with NOVA to check if any […]
[Original post on infosec.exchange]
September 28, 2025 at 6:50 AM
🤓 I have released Proximity, my MCP Security Scanner powered by NOVA!
Before using a public MCP server, you can quickly probe the endpoint or your local MCP to discover exposed prompts, tools, and resources. You can then scan with NOVA to check if any […]
[Original post on infosec.exchange]
Before using a public MCP server, you can quickly probe the endpoint or your local MCP to discover exposed prompts, tools, and resources. You can then scan with NOVA to check if any […]
[Original post on infosec.exchange]
🤓 If you are looking for a threat intel workflow, don't forget the Jupyter Universe! It gives you a central point to find useful Jupyter notebooks.
No need to reinvent the wheel when talented researchers already did the work!
👉 https://juniverse.securitybreak.io/
No need to reinvent the wheel when talented researchers already did the work!
👉 https://juniverse.securitybreak.io/
September 26, 2025 at 8:56 PM
🤓 If you are looking for a threat intel workflow, don't forget the Jupyter Universe! It gives you a central point to find useful Jupyter notebooks.
No need to reinvent the wheel when talented researchers already did the work!
👉 https://juniverse.securitybreak.io/
No need to reinvent the wheel when talented researchers already did the work!
👉 https://juniverse.securitybreak.io/
👀 New Microsoft threat report shows how attackers are using AI for evasion and obfuscation in a phishing campaign!
One part is very interesting, the team spotted 5 AI fingerprints in the code. But instead of hiding the attack (the initial goal), these […]
[Original post on infosec.exchange]
One part is very interesting, the team spotted 5 AI fingerprints in the code. But instead of hiding the attack (the initial goal), these […]
[Original post on infosec.exchange]

September 25, 2025 at 4:42 AM
👀 New Microsoft threat report shows how attackers are using AI for evasion and obfuscation in a phishing campaign!
One part is very interesting, the team spotted 5 AI fingerprints in the code. But instead of hiding the attack (the initial goal), these […]
[Original post on infosec.exchange]
One part is very interesting, the team spotted 5 AI fingerprints in the code. But instead of hiding the attack (the initial goal), these […]
[Original post on infosec.exchange]
🤩 I am super happy to share that I have been nominated again for the #SANSDMA Award!
Last year I did not win, but this year my open-source tool NOVA has been selected in the Innovation of the Year category.
If you like the project, please cast your vote to […]
[Original post on infosec.exchange]
Last year I did not win, but this year my open-source tool NOVA has been selected in the Innovation of the Year category.
If you like the project, please cast your vote to […]
[Original post on infosec.exchange]

September 24, 2025 at 5:54 AM
🤩 I am super happy to share that I have been nominated again for the #SANSDMA Award!
Last year I did not win, but this year my open-source tool NOVA has been selected in the Innovation of the Year category.
If you like the project, please cast your vote to […]
[Original post on infosec.exchange]
Last year I did not win, but this year my open-source tool NOVA has been selected in the Innovation of the Year category.
If you like the project, please cast your vote to […]
[Original post on infosec.exchange]
🤓 This weekend I sent out my latest newsletter, a quick recap of BlackHat & Defcon along with some updates from my side!
Have a read 👉 https://newsletter.securitybreak.io/archive/blackhat-defcon2025
Have a read 👉 https://newsletter.securitybreak.io/archive/blackhat-defcon2025

September 22, 2025 at 10:29 AM
🤓 This weekend I sent out my latest newsletter, a quick recap of BlackHat & Defcon along with some updates from my side!
Have a read 👉 https://newsletter.securitybreak.io/archive/blackhat-defcon2025
Have a read 👉 https://newsletter.securitybreak.io/archive/blackhat-defcon2025
The Unprotect Project is a place to learn about Malware Evasion with code snippets and detection rules. I recently added a small update thanks to new contributions 🙏
👉 https://unprotect.it/
👉 https://unprotect.it/

September 20, 2025 at 5:37 AM
The Unprotect Project is a place to learn about Malware Evasion with code snippets and detection rules. I recently added a small update thanks to new contributions 🙏
👉 https://unprotect.it/
👉 https://unprotect.it/
📸 One month ago in Vegas. I shared my work on Adversarial Prompts or Indicators of Prompt Compromise (IoPCs).
My goal is simple: create a common foundation we can all build on to classify and track adversarial prompts!
My goal is simple: create a common foundation we can all build on to classify and track adversarial prompts!

September 20, 2025 at 12:05 AM
📸 One month ago in Vegas. I shared my work on Adversarial Prompts or Indicators of Prompt Compromise (IoPCs).
My goal is simple: create a common foundation we can all build on to classify and track adversarial prompts!
My goal is simple: create a common foundation we can all build on to classify and track adversarial prompts!
🚨 New threat report: threat actor leverages AI at scale for influence… with a twist!
Threat actor Storm-1516 relies on uncensored and self-hosted LLMs, using variants of the Llama-3.1-8B model (dolphin-2.9-llama3-8b, Llama-3-8B-Lexi-Uncensored). They use […]
[Original post on infosec.exchange]
Threat actor Storm-1516 relies on uncensored and self-hosted LLMs, using variants of the Llama-3.1-8B model (dolphin-2.9-llama3-8b, Llama-3-8B-Lexi-Uncensored). They use […]
[Original post on infosec.exchange]

September 19, 2025 at 6:17 AM
🚨 New threat report: threat actor leverages AI at scale for influence… with a twist!
Threat actor Storm-1516 relies on uncensored and self-hosted LLMs, using variants of the Llama-3.1-8B model (dolphin-2.9-llama3-8b, Llama-3-8B-Lexi-Uncensored). They use […]
[Original post on infosec.exchange]
Threat actor Storm-1516 relies on uncensored and self-hosted LLMs, using variants of the Llama-3.1-8B model (dolphin-2.9-llama3-8b, Llama-3-8B-Lexi-Uncensored). They use […]
[Original post on infosec.exchange]
🤓 I have been saying for a while that prompts are the new IOCs.
In my latest blog, I break down the full classification of Indicators of Prompt Compromise (IoPCs) and how we can start hunting adversarial prompts.
Curious to hear your thoughts 👇 […]
[Original post on infosec.exchange]
In my latest blog, I break down the full classification of Indicators of Prompt Compromise (IoPCs) and how we can start hunting adversarial prompts.
Curious to hear your thoughts 👇 […]
[Original post on infosec.exchange]

September 14, 2025 at 8:58 AM
🤓 I have been saying for a while that prompts are the new IOCs.
In my latest blog, I break down the full classification of Indicators of Prompt Compromise (IoPCs) and how we can start hunting adversarial prompts.
Curious to hear your thoughts 👇 […]
[Original post on infosec.exchange]
In my latest blog, I break down the full classification of Indicators of Prompt Compromise (IoPCs) and how we can start hunting adversarial prompts.
Curious to hear your thoughts 👇 […]
[Original post on infosec.exchange]
Brave demonstrated an Indirect Prompt Injection attack to exfiltrate OTPs on Comet the Perplexity browser! 👇
brave.com/blog/comet-prompt-injection/
brave.com/blog/comet-prompt-injection/

September 12, 2025 at 6:16 AM
Brave demonstrated an Indirect Prompt Injection attack to exfiltrate OTPs on Comet the Perplexity browser! 👇
brave.com/blog/comet-prompt-injection/
brave.com/blog/comet-prompt-injection/

