@fidgetingbits.bsky.social
Reposted
I had so much fun designing and executing this attack, from hardware to software! Huge thanks to @thezdi.bsky.social for introducing such devices and attack vectors into the contest!

January 23, 2025 at 7:51 PM
I had so much fun designing and executing this attack, from hardware to software! Huge thanks to @thezdi.bsky.social for introducing such devices and attack vectors into the contest!
Reposted
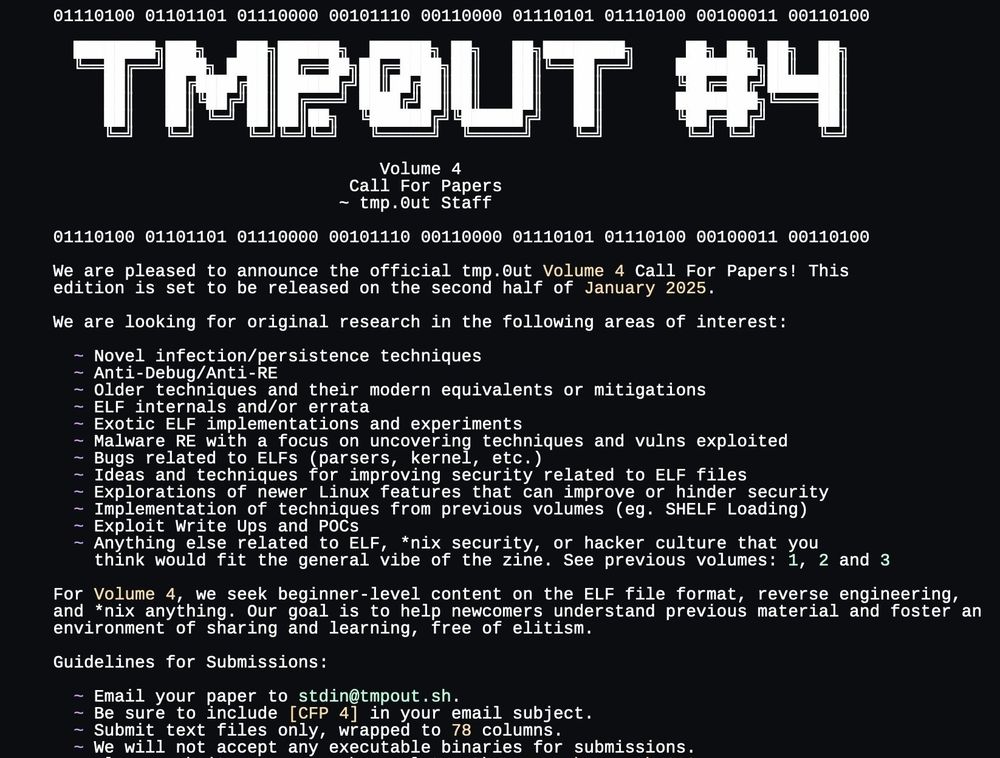
We are extending our call for papers to January 1, 2025!
We are now targeting an end of January release.
If you have any Linux/ELF related research, projects, or papers, we would love to publish them!
Huge thank you to everyone who has already submitted!
tmpout.sh/blog/vol4-cf...
We are now targeting an end of January release.
If you have any Linux/ELF related research, projects, or papers, we would love to publish them!
Huge thank you to everyone who has already submitted!
tmpout.sh/blog/vol4-cf...
December 16, 2024 at 9:36 PM
We are extending our call for papers to January 1, 2025!
We are now targeting an end of January release.
If you have any Linux/ELF related research, projects, or papers, we would love to publish them!
Huge thank you to everyone who has already submitted!
tmpout.sh/blog/vol4-cf...
We are now targeting an end of January release.
If you have any Linux/ELF related research, projects, or papers, we would love to publish them!
Huge thank you to everyone who has already submitted!
tmpout.sh/blog/vol4-cf...
Reposted
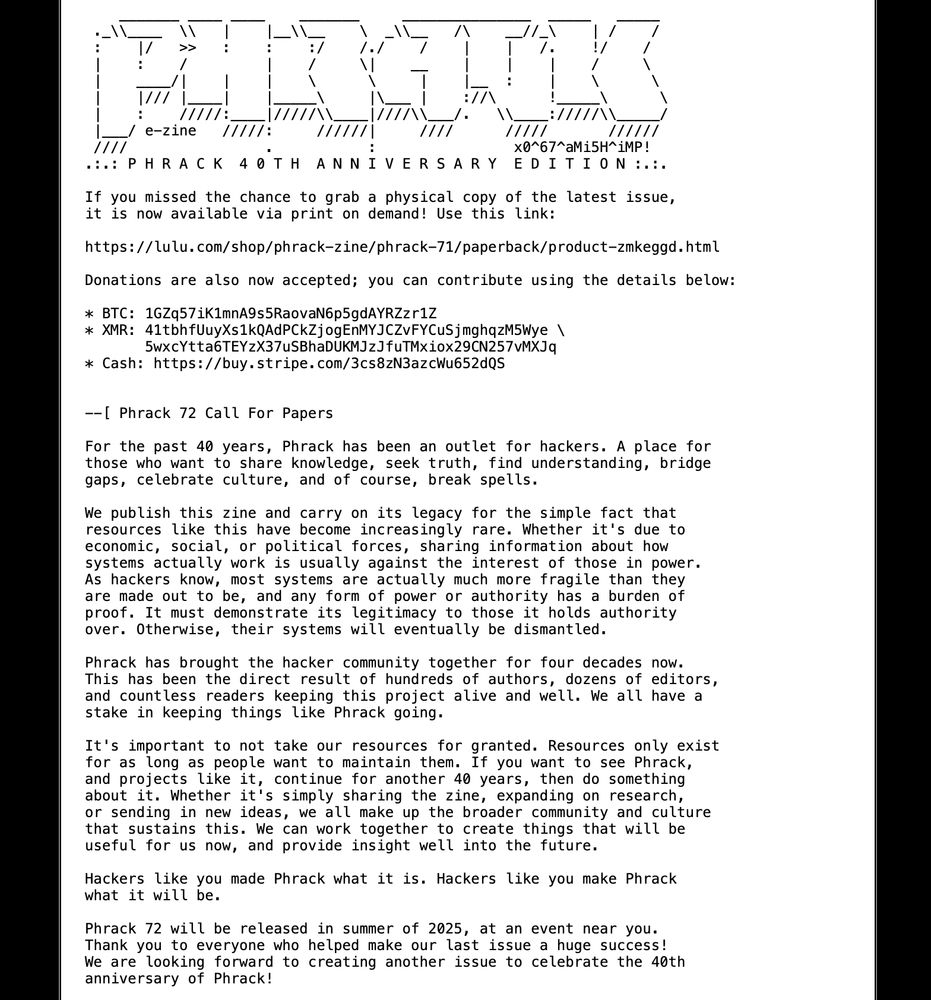
We updated our CFP for Phrack 72! The deadline is now April 1st 2025. Check the site for specifics on how to contribute, as well as some inspiration! We also posted a link to purchase physical copies of Phrack 71, and a donation link too. Enjoy!
phrack.org
phrack.org
December 16, 2024 at 10:56 PM
We updated our CFP for Phrack 72! The deadline is now April 1st 2025. Check the site for specifics on how to contribute, as well as some inspiration! We also posted a link to purchase physical copies of Phrack 71, and a donation link too. Enjoy!
phrack.org
phrack.org
Reposted
LIEF 0.16.0 is out featuring new (extended) capabilities like Dyld Shared Cache support, Assembler/disassembler, ...
lief.re/blog/2024-12...
lief.re/blog/2024-12...

December 10, 2024 at 11:24 AM
LIEF 0.16.0 is out featuring new (extended) capabilities like Dyld Shared Cache support, Assembler/disassembler, ...
lief.re/blog/2024-12...
lief.re/blog/2024-12...
Reposted
Rapid7 has disclosed the vulns from our exploit chain targeting the Lorex 2K Indoor Wi-Fi Security Camera, which we entered at this year's Pwn2Own Ireland. A 2 phase exploit, built upon 5 vulns - phase 1 is an auth bypass, whilst phase 2 is RCE. Disclosure, analysis and exploit here: t.co/J9VDwMDRsI
https://www.rapid7.com/blog/post/2024/12/03/lorex-2k-indoor-wi-fi-security-camera-multiple-vulnerabilities-fixed/
t.co
December 4, 2024 at 9:32 AM
Rapid7 has disclosed the vulns from our exploit chain targeting the Lorex 2K Indoor Wi-Fi Security Camera, which we entered at this year's Pwn2Own Ireland. A 2 phase exploit, built upon 5 vulns - phase 1 is an auth bypass, whilst phase 2 is RCE. Disclosure, analysis and exploit here: t.co/J9VDwMDRsI
Reposted
for anyone interested in linux kernel or android security research, i'm experimenting with a custom feed here bsky.app/profile/did:...
December 3, 2024 at 7:45 PM
for anyone interested in linux kernel or android security research, i'm experimenting with a custom feed here bsky.app/profile/did:...
Reposted
Novel approach to exploit a limited OOB on Ubuntu at Pwn2Own Vancouver 2024
Slides from a talk by Pumpkin Chang about exploiting a stack out-of-bounds write bug in the traffic control subsystem.
u1f383.github.io/slides/talks...
Slides from a talk by Pumpkin Chang about exploiting a stack out-of-bounds write bug in the traffic control subsystem.
u1f383.github.io/slides/talks...

November 27, 2024 at 6:51 PM
Novel approach to exploit a limited OOB on Ubuntu at Pwn2Own Vancouver 2024
Slides from a talk by Pumpkin Chang about exploiting a stack out-of-bounds write bug in the traffic control subsystem.
u1f383.github.io/slides/talks...
Slides from a talk by Pumpkin Chang about exploiting a stack out-of-bounds write bug in the traffic control subsystem.
u1f383.github.io/slides/talks...
Reposted
Ready for the Advent of Radare?
❄️🗓️ > radare.org/advent
Starting tomorrow, December 1st we will release every day a new article with general knowledge, tricks, scripts and challenges to solve with radare2 covering topics from #aor24 #reverseengineering
❄️🗓️ > radare.org/advent
Starting tomorrow, December 1st we will release every day a new article with general knowledge, tricks, scripts and challenges to solve with radare2 covering topics from #aor24 #reverseengineering

November 30, 2024 at 4:29 PM
Ready for the Advent of Radare?
❄️🗓️ > radare.org/advent
Starting tomorrow, December 1st we will release every day a new article with general knowledge, tricks, scripts and challenges to solve with radare2 covering topics from #aor24 #reverseengineering
❄️🗓️ > radare.org/advent
Starting tomorrow, December 1st we will release every day a new article with general knowledge, tricks, scripts and challenges to solve with radare2 covering topics from #aor24 #reverseengineering
Reposted
Haven't made a RE//verse bluesky account yet, but heads up for folks that in 5m the next round of conference tickets goes live!
shop.binary.ninja/products/re-...
shop.binary.ninja/products/re-...

RE//verse Admission
A conference for the reverse engineering universe...
shop.binary.ninja
December 1, 2024 at 9:55 PM
Haven't made a RE//verse bluesky account yet, but heads up for folks that in 5m the next round of conference tickets goes live!
shop.binary.ninja/products/re-...
shop.binary.ninja/products/re-...
Reposted
for anyone out there who wants to download vmware "now that its free", but doesnt want to go through the fucking cirque de soleil trapeze act of auth and redirects and entitlements, someone on masto linked me to this - where you can just fetch ... everything, without need for their bullshit!
CDS Repository - /var/www/public/stage/session-120/cds/vmw-desktop
softwareupdate.vmware.com
December 1, 2024 at 9:53 PM
for anyone out there who wants to download vmware "now that its free", but doesnt want to go through the fucking cirque de soleil trapeze act of auth and redirects and entitlements, someone on masto linked me to this - where you can just fetch ... everything, without need for their bullshit!
Reposted
Wislist for Linux from the mold linker's POV
lore.kernel.org/lkml/CACKH baPUaoQQhL0 [email protected]/#t
lore.kernel.org/lkml/CACKH baPUaoQQhL0 [email protected]/#t
lore.kernel.org
November 29, 2024 at 1:17 AM
Wislist for Linux from the mold linker's POV
lore.kernel.org/lkml/CACKH baPUaoQQhL0 [email protected]/#t
lore.kernel.org/lkml/CACKH baPUaoQQhL0 [email protected]/#t
Reposted
Earlier this year, I used a 1day to exploit the kernelCTF VRP LTS instance. I then used the same bug to write a universal exploit that worked against up-to-date mainstream distros for approximately 2 months.
osec.io/blog/2024-11...
osec.io/blog/2024-11...

November 28, 2024 at 12:54 PM
Earlier this year, I used a 1day to exploit the kernelCTF VRP LTS instance. I then used the same bug to write a universal exploit that worked against up-to-date mainstream distros for approximately 2 months.
osec.io/blog/2024-11...
osec.io/blog/2024-11...
Reposted
Firefox, Thunderbird, Tor Browser RCE: www.welivesecurity.c...

RomCom exploits Firefox and Windows zero days in the wild
ESET Research details the analysis of a previously unknown vulnerability in Mozilla products exploited in the wild and another previously unknown Microsoft Windows vulnerability, combined in a zero-click exploit.
www.welivesecurity.com
November 27, 2024 at 5:31 AM
Firefox, Thunderbird, Tor Browser RCE: www.welivesecurity.c...
Reposted
Something something hackers but with bad opsec :)

November 23, 2024 at 7:29 PM
Something something hackers but with bad opsec :)
Reposted
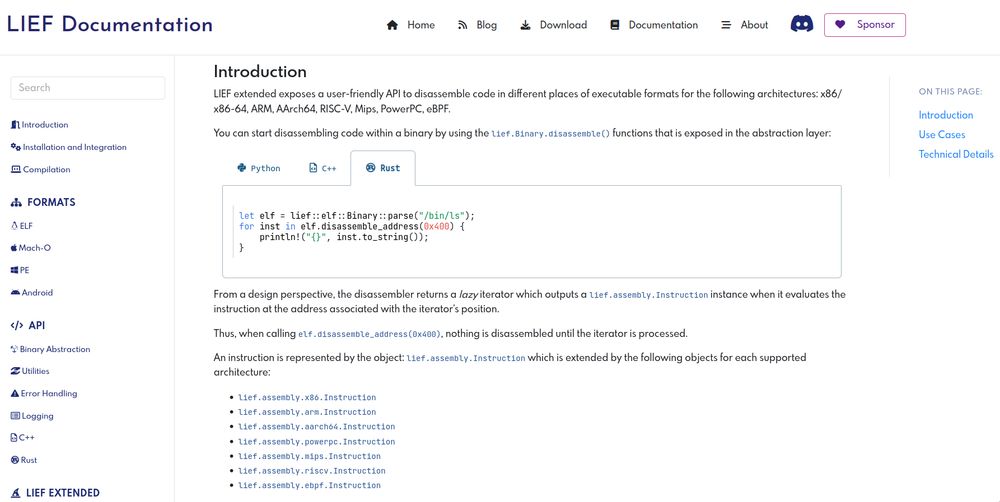
So for my first post on Bluesky, I'm happy to share that LIEF (extended) is now providing an API to disassemble code (backed by the LLVM MC layer).
This disassembler is integrated with other functionalities
like dyldsc or DWARF info.
You can checkout lief.re/doc/latest/e... for the details.
This disassembler is integrated with other functionalities
like dyldsc or DWARF info.
You can checkout lief.re/doc/latest/e... for the details.
November 23, 2024 at 9:33 AM
So for my first post on Bluesky, I'm happy to share that LIEF (extended) is now providing an API to disassemble code (backed by the LLVM MC layer).
This disassembler is integrated with other functionalities
like dyldsc or DWARF info.
You can checkout lief.re/doc/latest/e... for the details.
This disassembler is integrated with other functionalities
like dyldsc or DWARF info.
You can checkout lief.re/doc/latest/e... for the details.
Reposted
XBOW bypasses a MIME-type filter, abusing an OTP icon preview feature in 2FAuth to exploit an SSRF and discover CVE 2024-52598. Affected users should apply the patch and read about all the details in our latest blog post: xbow.com/blog/xbow-2f...

November 22, 2024 at 11:45 PM
XBOW bypasses a MIME-type filter, abusing an OTP icon preview feature in 2FAuth to exploit an SSRF and discover CVE 2024-52598. Affected users should apply the patch and read about all the details in our latest blog post: xbow.com/blog/xbow-2f...
Reposted
@volexity.com’s latest blog post describes in detail how a Russian APT used a new attack technique, the “Nearest Neighbor Attack”, to leverage Wi-Fi networks in close proximity to the intended target while the attacker was halfway around the world.
Read more here: www.volexity.com/blog/2024/11...
Read more here: www.volexity.com/blog/2024/11...

The Nearest Neighbor Attack: How A Russian APT Weaponized Nearby Wi-Fi Networks for Covert Access
In early February 2022, notably just ahead of the Russian invasion of Ukraine, Volexity made a discovery that led to one of the most fascinating and complex incident investigations Volexity had ever w...
www.volexity.com
November 22, 2024 at 2:58 PM
@volexity.com’s latest blog post describes in detail how a Russian APT used a new attack technique, the “Nearest Neighbor Attack”, to leverage Wi-Fi networks in close proximity to the intended target while the attacker was halfway around the world.
Read more here: www.volexity.com/blog/2024/11...
Read more here: www.volexity.com/blog/2024/11...
Reposted
Heh, got the poc for @qualys.bsky.social #needrestart CVE-2024-48990 in a couple of hours 😄

November 22, 2024 at 2:17 PM
Heh, got the poc for @qualys.bsky.social #needrestart CVE-2024-48990 in a couple of hours 😄
Reposted
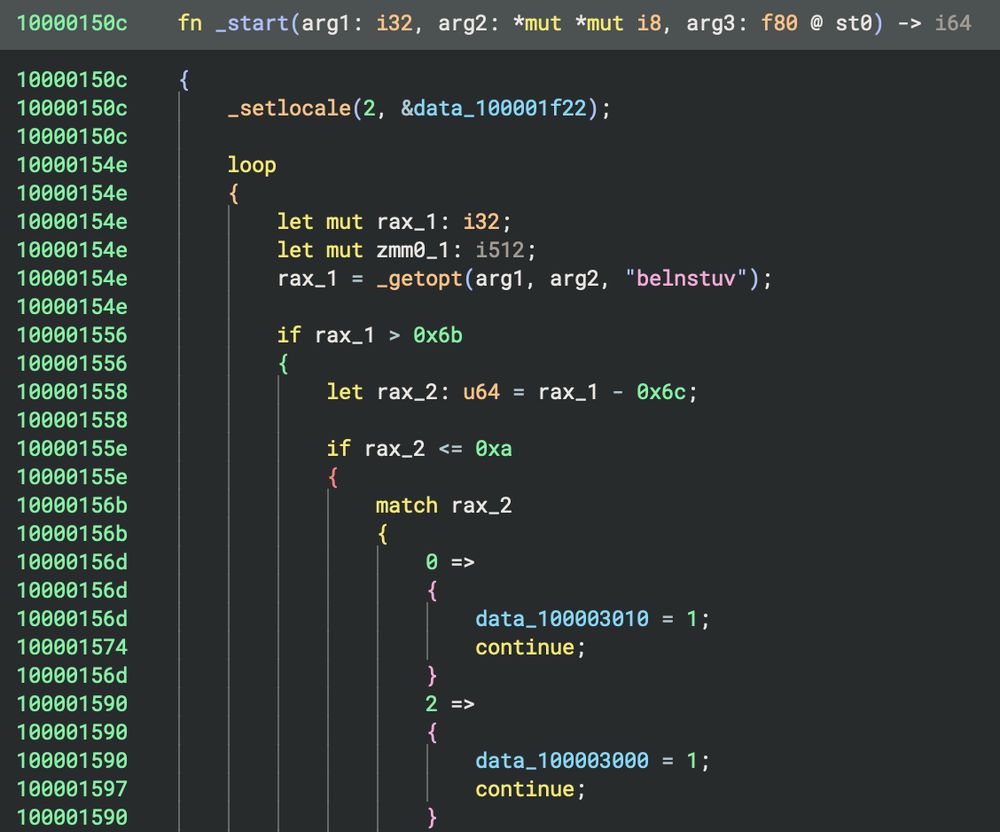
Don't Panic! The answer: version 4.2 of Binary Ninja, is now available. Check out the release blog post which shows:
- New PseudoC/Python/Rust decompilation
- DLYD Shared Cache Support
- WARP Signature System
And many other impactful features.
https://binary.ninja/2024/11/20/4.2-frogstar.html
- New PseudoC/Python/Rust decompilation
- DLYD Shared Cache Support
- WARP Signature System
And many other impactful features.
https://binary.ninja/2024/11/20/4.2-frogstar.html

November 20, 2024 at 9:36 PM
Don't Panic! The answer: version 4.2 of Binary Ninja, is now available. Check out the release blog post which shows:
- New PseudoC/Python/Rust decompilation
- DLYD Shared Cache Support
- WARP Signature System
And many other impactful features.
https://binary.ninja/2024/11/20/4.2-frogstar.html
- New PseudoC/Python/Rust decompilation
- DLYD Shared Cache Support
- WARP Signature System
And many other impactful features.
https://binary.ninja/2024/11/20/4.2-frogstar.html
Reposted
November 19, 2024 at 9:07 AM
Reposted
XBOW found a critical auth bypass (CVE-2024-50334) in Scoold, a widely-used open-source Q&A site, fully autonomously! @nicowaisman.bsky.social and I wrote up a post walking through the methodology it used – IMO it's a super cool bug and fascinating trace xbow.com/blog/xbow-sc...

XBOW – How XBOW found a Scoold authentication bypass
As we shift our focus from benchmarks to real world applications, we will be sharing some of the most interesting vulnerabilities XBOW has found in real-world, open-source targets. The first of these ...
xbow.com
November 14, 2024 at 4:10 PM
XBOW found a critical auth bypass (CVE-2024-50334) in Scoold, a widely-used open-source Q&A site, fully autonomously! @nicowaisman.bsky.social and I wrote up a post walking through the methodology it used – IMO it's a super cool bug and fascinating trace xbow.com/blog/xbow-sc...

