
🔗 expel.com
Here's the approach we've developed to identify and stop Shai Hulud activity: expel.com/blog/the-sec...

Here's the approach we've developed to identify and stop Shai Hulud activity: expel.com/blog/the-sec...
Full threat intel recap here: expel.com/blog/expel-q...

Full threat intel recap here: expel.com/blog/expel-q...


The trend is moving in the right direction but there's still more work to do since 45.1% aren't being blocked.
The trend is moving in the right direction but there's still more work to do since 45.1% aren't being blocked.
• Credentials → cloud services
• Malware → endpoints
• Misconfigurations → cloud infrastructure
Each surface is distinct. One defensive strategy doesn't cover all three. You need different plans for each.
• Credentials → cloud services
• Malware → endpoints
• Misconfigurations → cloud infrastructure
Each surface is distinct. One defensive strategy doesn't cover all three. You need different plans for each.
• Manufacturing: highest total incident volume (overtook financial services)
• Healthcare: disproportionately hit by non-targeted malware
• Pharma & chemical: highest proportion of identity attacks in top 10

• Manufacturing: highest total incident volume (overtook financial services)
• Healthcare: disproportionately hit by non-targeted malware
• Pharma & chemical: highest proportion of identity attacks in top 10
Biggest increase: secret key exposure, up 7.8 percentage points from Q2 to 26.8% of cloud incidents. Keys exposed through hardcoded credentials or supply chain attacks like Shai Hulud.

Biggest increase: secret key exposure, up 7.8 percentage points from Q2 to 26.8% of cloud incidents. Keys exposed through hardcoded credentials or supply chain attacks like Shai Hulud.
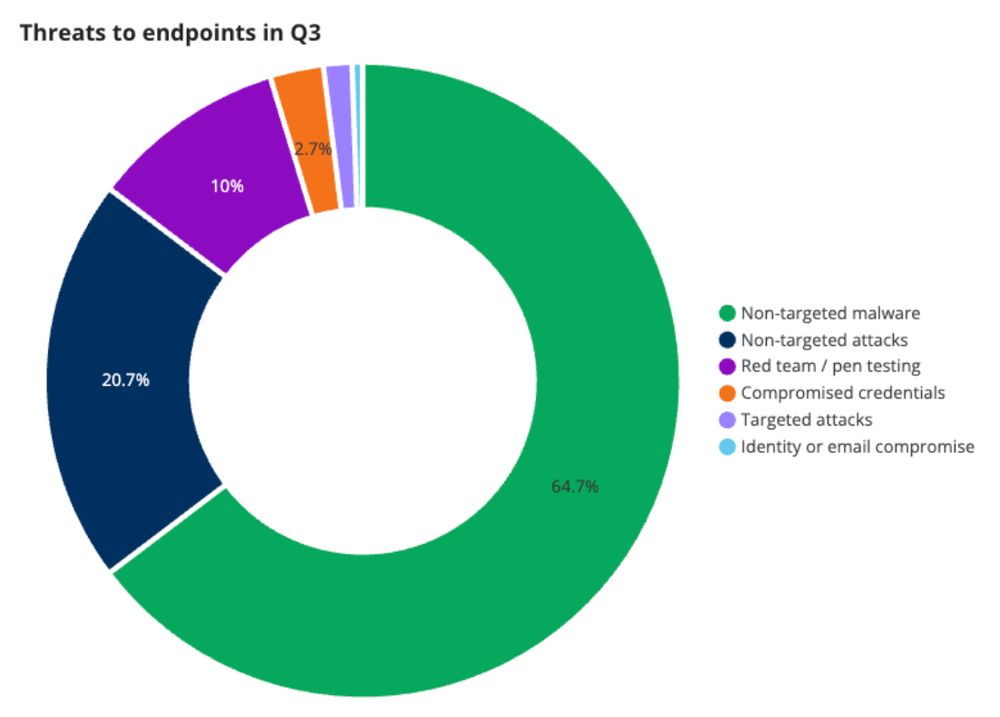
Non-targeted malware dominates at 64.7% of endpoint incidents. This swung back up from 50.2% in Q2.
Attackers are still using traditional tactics—malware, compromising public-facing systems—to get onto devices.
Non-targeted malware dominates at 64.7% of endpoint incidents. This swung back up from 50.2% in Q2.
Attackers are still using traditional tactics—malware, compromising public-facing systems—to get onto devices.
Modern identity controls (MFA, conditional access, monitoring) are working when implemented properly.

Modern identity controls (MFA, conditional access, monitoring) are working when implemented properly.
Overview of the campaign, IOCs, and file hashes: expel.com/blog/certifi...

Overview of the campaign, IOCs, and file hashes: expel.com/blog/certifi...

