DarwinOps provides
- An advanced injection vulnerability scanner
- A redteam scenario to exploit them
#redteam
blog.balliskit.com/macos-dylib-...

DarwinOps provides
- An advanced injection vulnerability scanner
- A redteam scenario to exploit them
#redteam
blog.balliskit.com/macos-dylib-...

"Offline Extraction of Symantec Account Connectivity Credentials (ACCs)"
Following my previous post on the subject, here is how to extract ACCs purely offline.
👉 itm4n.github.io/offline-extr...
#redteam #pentesting
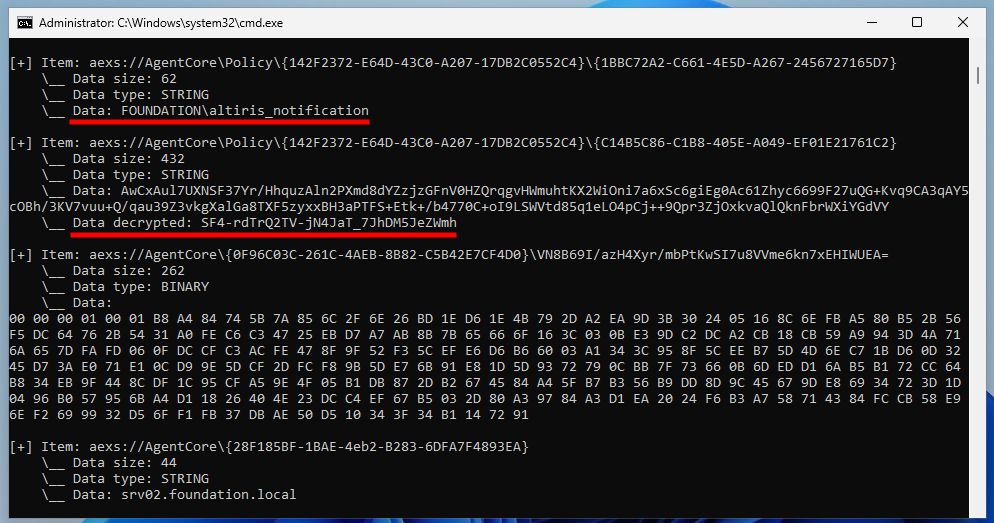
"Offline Extraction of Symantec Account Connectivity Credentials (ACCs)"
Following my previous post on the subject, here is how to extract ACCs purely offline.
👉 itm4n.github.io/offline-extr...
#redteam #pentesting
falconforce.nl/dawshund-fra...
#blueteaming #redteaming
falconforce.nl/dawshund-fra...
#blueteaming #redteaming

- Blog: ibm.com/think/news/f...
- PoC: github.com/xforcered/Fo...

- Blog: ibm.com/think/news/f...
- PoC: github.com/xforcered/Fo...
catalyst.prodaft.com/public/repor...
catalyst.prodaft.com/public/repor...
The campaign took place in November & December of last year and used an exploit similar to a zero-day exploited by Russian hackers in Ukraine.
research.checkpoint.com/2025/blind-e...

The campaign took place in November & December of last year and used an exploit similar to a zero-day exploited by Russian hackers in Ukraine.
research.checkpoint.com/2025/blind-e...
Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;)
github.com/decoder-it/K...
Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;)
github.com/decoder-it/K...
New Microsoft Defender for Endpoint telemetry provides new opportunities for threat detection!
🔗
academy.bluraven.io/blog/beaconi...
#ThreatHunting #DetectionEngineering #MDE

New Microsoft Defender for Endpoint telemetry provides new opportunities for threat detection!
🔗
academy.bluraven.io/blog/beaconi...
#ThreatHunting #DetectionEngineering #MDE



