Dirk-jan
@dirkjanm.io
Hacker at outsidersecurity.nl. Researches Entra ID, AD and occasionally Windows security. I write open source security tools and do blogs/talks to educate others on these topics. Blog: dirkjanm.io
Reposted by Dirk-jan
Note: Work related
I do Active Directory stuff for a living. Security research to be more specific. One of my favorite niche AD topics is AdminSDHolder. It's even my vanity domain.
I wrote a 159 pg book about AdminSDHolder. I'm kinda proud of it.
specterops.io/resources/ad...
I do Active Directory stuff for a living. Security research to be more specific. One of my favorite niche AD topics is AdminSDHolder. It's even my vanity domain.
I wrote a 159 pg book about AdminSDHolder. I'm kinda proud of it.
specterops.io/resources/ad...

AdminSDHolder Misconceptions & Misconfigurations - SpecterOps
AdminSDHolder is an object and associated process in Active Directory Domain Services (AD DS) that helps protect specific sensitive and highly privileged accounts from being manipulated. This topic is...
specterops.io
October 31, 2025 at 7:47 PM
Note: Work related
I do Active Directory stuff for a living. Security research to be more specific. One of my favorite niche AD topics is AdminSDHolder. It's even my vanity domain.
I wrote a 159 pg book about AdminSDHolder. I'm kinda proud of it.
specterops.io/resources/ad...
I do Active Directory stuff for a living. Security research to be more specific. One of my favorite niche AD topics is AdminSDHolder. It's even my vanity domain.
I wrote a 159 pg book about AdminSDHolder. I'm kinda proud of it.
specterops.io/resources/ad...
Seems Microsoft is doing some app and permission cleanups and tenant restrictions lately. RIP Microsoft Planner FOCI client.

October 27, 2025 at 1:59 PM
Seems Microsoft is doing some app and permission cleanups and tenant restrictions lately. RIP Microsoft Planner FOCI client.
Reposted by Dirk-jan
Dirk-jan Mollema found one of the most severe vulnerabilities ever discovered in Microsoft Entra ID.
One that could have compromised every tenant in the cloud.
In this episode, we unpack the story, the stress, and the mindset behind responsible disclosure. 🔥
One that could have compromised every tenant in the cloud.
In this episode, we unpack the story, the stress, and the mindset behind responsible disclosure. 🔥

October 24, 2025 at 1:24 PM
Dirk-jan Mollema found one of the most severe vulnerabilities ever discovered in Microsoft Entra ID.
One that could have compromised every tenant in the cloud.
In this episode, we unpack the story, the stress, and the mindset behind responsible disclosure. 🔥
One that could have compromised every tenant in the cloud.
In this episode, we unpack the story, the stress, and the mindset behind responsible disclosure. 🔥
I've been researching the Microsoft cloud for almost 7 years now. A few months ago that research resulted in the most impactful vulnerability I will probably ever find: a token validation flaw allowing me to get Global Admin in any Entra ID tenant. Blog: dirkjanm.io/obtaining-gl...
One Token to rule them all - obtaining Global Admin in every Entra ID tenant via Actor tokens
While preparing for my Black Hat and DEF CON talks in July of this year, I found the most impactful Entra ID vulnerability that I will probably ever find. One that could have allowed me to compromise ...
dirkjanm.io
September 17, 2025 at 1:20 PM
I've been researching the Microsoft cloud for almost 7 years now. A few months ago that research resulted in the most impactful vulnerability I will probably ever find: a token validation flaw allowing me to get Global Admin in any Entra ID tenant. Blog: dirkjanm.io/obtaining-gl...
📢 New date for my "Offensive Entra ID security" course: December 8-11th 2025. This will be the last event this year. The previous events sold out quite fast so don't wait too long if you want to attend! 😀 events.outsidersecurity.nl/entra-25-12/

Training: Offensive Entra ID (Azure AD) and Hybrid AD security
Dec. 8th – 11th, 2025
events.outsidersecurity.nl
September 1, 2025 at 1:37 PM
📢 New date for my "Offensive Entra ID security" course: December 8-11th 2025. This will be the last event this year. The previous events sold out quite fast so don't wait too long if you want to attend! 😀 events.outsidersecurity.nl/entra-25-12/
It seems there now is a BOF implementation of ADSyncDecrypt to dump Entra ID connect creds 👀
github.com/Paradoxis/AD...
github.com/Paradoxis/AD...

GitHub - Paradoxis/ADSyncDump-BOF: The ADSyncDump BOF is a port of Dirkjan Mollema's adconnectdump.py / ADSyncDecrypt into a Beacon Object File (BOF) with zero dependencies.
The ADSyncDump BOF is a port of Dirkjan Mollema's adconnectdump.py / ADSyncDecrypt into a Beacon Object File (BOF) with zero dependencies. - Paradoxis/ADSyncDump-BOF
github.com
August 26, 2025 at 4:16 PM
It seems there now is a BOF implementation of ADSyncDecrypt to dump Entra ID connect creds 👀
github.com/Paradoxis/AD...
github.com/Paradoxis/AD...
If you didn't find my Black Hat / Def Con slides yet, they are available on dirkjanm.io/talks . Also includes the demo videos where I use actor tokens from on-prem to access SharePoint online and get Global Admin.
Presentations and external blogs
Dirk-jan’s personal blog, mostly containing research on topics I find interesting, such as (Azure) Active Directory internals, protocols and vulnerabilities.
dirkjanm.io
August 20, 2025 at 1:46 PM
If you didn't find my Black Hat / Def Con slides yet, they are available on dirkjanm.io/talks . Also includes the demo videos where I use actor tokens from on-prem to access SharePoint online and get Global Admin.
Reposted by Dirk-jan
🎉 Exciting news: The Office 365 Exchange Online SP privilege escalation we documented in "I SPy" is no longer possible! We've updated the post to reflect this. Thanks to Eli Guy for the tip on this one:
securitylabs.datadoghq.com/articles/i-s...
securitylabs.datadoghq.com/articles/i-s...

I SPy: Escalating to Entra ID's Global Admin with a first-party app | Datadog Security Labs
Backdooring Microsoft's applications is far from over. Adding service principal credentials to these apps to escalate privileges and obfuscate activities has been seen in nation-state attacks, and led...
securitylabs.datadoghq.com
August 14, 2025 at 5:06 PM
🎉 Exciting news: The Office 365 Exchange Online SP privilege escalation we documented in "I SPy" is no longer possible! We've updated the post to reflect this. Thanks to Eli Guy for the tip on this one:
securitylabs.datadoghq.com/articles/i-s...
securitylabs.datadoghq.com/articles/i-s...
The ADSyncCertDump tool is now part of the adconnectdump tools and can be used to extract SP credentials from Entra ID connect hosts. I will cover that during my BH/DC talks today and Friday! Tool is heavily based on Shwmae by @ethicalchaos.bsky.social
Link: github.com/dirkjanm/adc...
Link: github.com/dirkjanm/adc...
August 6, 2025 at 3:24 PM
The ADSyncCertDump tool is now part of the adconnectdump tools and can be used to extract SP credentials from Entra ID connect hosts. I will cover that during my BH/DC talks today and Friday! Tool is heavily based on Shwmae by @ethicalchaos.bsky.social
Link: github.com/dirkjanm/adc...
Link: github.com/dirkjanm/adc...
It's been almost a year since my last blog... So, here is a new one: Extending AD CS attack surface to the cloud with Intune certificates.
Also includes ESC1 over Intune (in some cases).
dirkjanm.io/extending-ad...
Oh, and a new tool for SCEP: github.com/dirkjanm/sce...
Also includes ESC1 over Intune (in some cases).
dirkjanm.io/extending-ad...
Oh, and a new tool for SCEP: github.com/dirkjanm/sce...
Extending AD CS attack surface to the cloud with Intune certificates
Active Directory Certificate Services (AD CS) attack surface is pretty well explored in Active Directory itself, with *checks notes* already 16 “ESC” attacks being publicly described. Hybrid attack pa...
dirkjanm.io
July 30, 2025 at 3:46 PM
It's been almost a year since my last blog... So, here is a new one: Extending AD CS attack surface to the cloud with Intune certificates.
Also includes ESC1 over Intune (in some cases).
dirkjanm.io/extending-ad...
Oh, and a new tool for SCEP: github.com/dirkjanm/sce...
Also includes ESC1 over Intune (in some cases).
dirkjanm.io/extending-ad...
Oh, and a new tool for SCEP: github.com/dirkjanm/sce...
For those like me who prefer to stay in the terminal and want to call REST APIs like the Microsoft Graph without complicated commands or copy/pasting tokens: roadtx now has a graphrequest command to perform simple requests against these APIs and parse the JSON.

July 25, 2025 at 2:05 PM
For those like me who prefer to stay in the terminal and want to call REST APIs like the Microsoft Graph without complicated commands or copy/pasting tokens: roadtx now has a graphrequest command to perform simple requests against these APIs and parse the JSON.
Reposted by Dirk-jan
Teammate Leonid discovered a leaked credential that allowed anyone unauthorized access to all Microsoft tenants of orgs that use Synology's "Active Backup for Microsoft 365" (ABM), including sensitive data like Teams channel messages. 🤓
#synology #disclosure #modzero
modzero.com/en/blog/when...
#synology #disclosure #modzero
modzero.com/en/blog/when...
When Backups Open Backdoors: Accessing Sensitive Cloud Data via
modzero.com
June 29, 2025 at 8:01 AM
Teammate Leonid discovered a leaked credential that allowed anyone unauthorized access to all Microsoft tenants of orgs that use Synology's "Active Backup for Microsoft 365" (ABM), including sensitive data like Teams channel messages. 🤓
#synology #disclosure #modzero
modzero.com/en/blog/when...
#synology #disclosure #modzero
modzero.com/en/blog/when...
Got word from MSRC that the product team reevaluated their initial duplicate/not-a-vuln decision and will actually be fixing this validation flaw in EAM 😂
Last two weeks I talked about BYO Identity Providers in Entra ID and backdoors to External Auth Methods to bypass MFA. Only possible because MSFT doesn't implement the mandatory OIDC security measures. Slides with optional dark mode on: dirkjanm.io/talks/
Presentations and external blogs
Dirk-jan’s personal blog, mostly containing research on topics I find interesting, such as (Azure) Active Directory internals, protocols and vulnerabilities.
dirkjanm.io
July 3, 2025 at 8:46 AM
Got word from MSRC that the product team reevaluated their initial duplicate/not-a-vuln decision and will actually be fixing this validation flaw in EAM 😂
Reposted by Dirk-jan
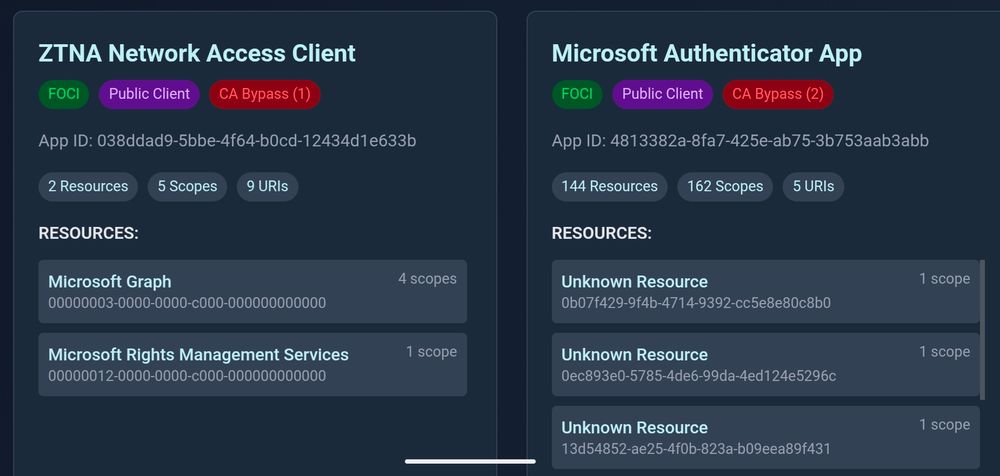
One of the results of the joined research with @dirkjanm.io is entrascopes.com
Basically the yellow pages for Microsoft first party apps.
#TROOPERS25
Basically the yellow pages for Microsoft first party apps.
#TROOPERS25
June 26, 2025 at 9:48 AM
One of the results of the joined research with @dirkjanm.io is entrascopes.com
Basically the yellow pages for Microsoft first party apps.
#TROOPERS25
Basically the yellow pages for Microsoft first party apps.
#TROOPERS25
Last two weeks I talked about BYO Identity Providers in Entra ID and backdoors to External Auth Methods to bypass MFA. Only possible because MSFT doesn't implement the mandatory OIDC security measures. Slides with optional dark mode on: dirkjanm.io/talks/
Presentations and external blogs
Dirk-jan’s personal blog, mostly containing research on topics I find interesting, such as (Azure) Active Directory internals, protocols and vulnerabilities.
dirkjanm.io
June 24, 2025 at 7:12 AM
Last two weeks I talked about BYO Identity Providers in Entra ID and backdoors to External Auth Methods to bypass MFA. Only possible because MSFT doesn't implement the mandatory OIDC security measures. Slides with optional dark mode on: dirkjanm.io/talks/
Reposted by Dirk-jan
Rerunning my test scenarios for the #TROOPERS25 presentation...
June 22, 2025 at 4:58 PM
Rerunning my test scenarios for the #TROOPERS25 presentation...
Received the news today that my talk "Advanced Active Directory to Entra ID lateral movement techniques" was also accepted for @defcon.bsky.social 🎉 hope to see everyone there!
June 10, 2025 at 12:28 PM
Received the news today that my talk "Advanced Active Directory to Entra ID lateral movement techniques" was also accepted for @defcon.bsky.social 🎉 hope to see everyone there!
Since we now can use Entra ID connect sync with a service principal, I thought I'd look into the new security measures. On hosts without a TPM, we can dump the cert+key. On hosts with TPM (second picture) we can use the key to create an auth assertion for roadtx to req tokens.


May 30, 2025 at 9:37 AM
Since we now can use Entra ID connect sync with a service principal, I thought I'd look into the new security measures. On hosts without a TPM, we can dump the cert+key. On hosts with TPM (second picture) we can use the key to create an auth assertion for roadtx to req tokens.
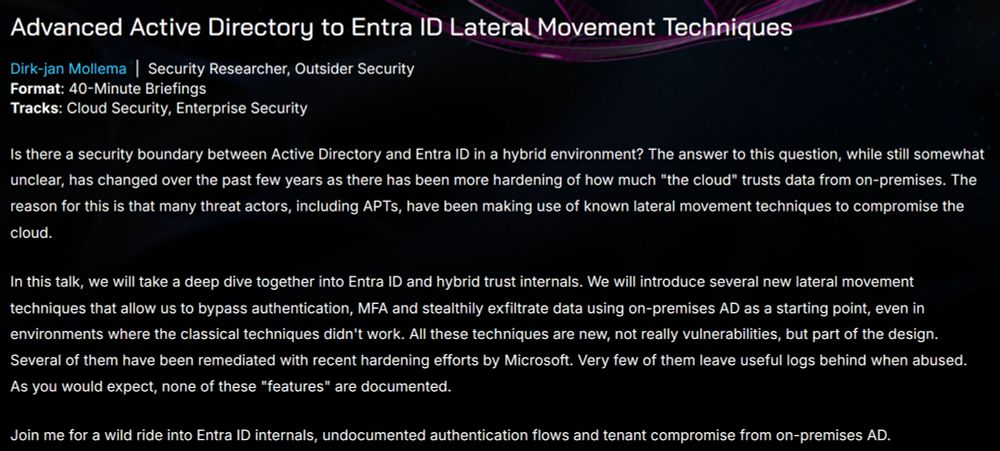
I'll be returning to #BHUSA @blackhatevents.bsky.social this summer for a brand talk about moving laterally from AD to Entra ID. I don't think I've ever been this excited about a talk, with lots of cool stuff to share 🎢 😄.
May 16, 2025 at 8:00 AM
I'll be returning to #BHUSA @blackhatevents.bsky.social this summer for a brand talk about moving laterally from AD to Entra ID. I don't think I've ever been this excited about a talk, with lots of cool stuff to share 🎢 😄.
Reposted by Dirk-jan
Just pushed a new versions for #AADInternals and AADInternals-Endpoint modules! Some bug fixes plus support for:
1️⃣ Microsoft Authentication Library (MSAL)
2️⃣ Token Protection
3️⃣ Continuous Access Evaluation (CAE)
1️⃣ Microsoft Authentication Library (MSAL)
2️⃣ Token Protection
3️⃣ Continuous Access Evaluation (CAE)
April 18, 2025 at 12:10 PM
Just pushed a new versions for #AADInternals and AADInternals-Endpoint modules! Some bug fixes plus support for:
1️⃣ Microsoft Authentication Library (MSAL)
2️⃣ Token Protection
3️⃣ Continuous Access Evaluation (CAE)
1️⃣ Microsoft Authentication Library (MSAL)
2️⃣ Token Protection
3️⃣ Continuous Access Evaluation (CAE)
Just found something super useful for my research...... In my own notes from 2023 😅 how I found it back then and why I didn't do anything with it remains a complete mystery.
April 16, 2025 at 1:30 PM
Just found something super useful for my research...... In my own notes from 2023 😅 how I found it back then and why I didn't do anything with it remains a complete mystery.
Two new Entra ID training opportunities in the next few months! I will give another 4-day edition of my public training July 7-10 in The Hague, NL.
I will also return to RomHack (Rome, IT) this year for a training Sept 23-27 😀
Info and ticket links: outsidersecurity.nl/training/
I will also return to RomHack (Rome, IT) this year for a training Sept 23-27 😀
Info and ticket links: outsidersecurity.nl/training/
Outsider Security - Training
Outsider Security - Training in Entra ID (Azure AD) and Active Directory security.
outsidersecurity.nl
April 10, 2025 at 7:43 AM
Two new Entra ID training opportunities in the next few months! I will give another 4-day edition of my public training July 7-10 in The Hague, NL.
I will also return to RomHack (Rome, IT) this year for a training Sept 23-27 😀
Info and ticket links: outsidersecurity.nl/training/
I will also return to RomHack (Rome, IT) this year for a training Sept 23-27 😀
Info and ticket links: outsidersecurity.nl/training/
Reposted by Dirk-jan
Spent the evening deep diving into MCPs and started a new project: roadrecon_mcp_server! This #MCP takes the web GUI output from the awesome ROADtools by @dirkjanm.io and offers tools to Claude (or your #AI agent of choice) to interact with the data:
github.com/atomicchonk/...
github.com/atomicchonk/...

GitHub - atomicchonk/roadrecon_mcp_server: Claude MCP server to perform analysis on ROADrecon data
Claude MCP server to perform analysis on ROADrecon data - atomicchonk/roadrecon_mcp_server
github.com
March 29, 2025 at 3:17 AM
Spent the evening deep diving into MCPs and started a new project: roadrecon_mcp_server! This #MCP takes the web GUI output from the awesome ROADtools by @dirkjanm.io and offers tools to Claude (or your #AI agent of choice) to interact with the data:
github.com/atomicchonk/...
github.com/atomicchonk/...
Automatic browser SSO with a PRT on a victim device over an Outflank C2 implant 🥰 using ROADtools and some hackery from Max Grim.

March 27, 2025 at 11:52 AM
Automatic browser SSO with a PRT on a victim device over an Outflank C2 implant 🥰 using ROADtools and some hackery from Max Grim.
Reposted by Dirk-jan
My @disobeyfi.bsky.social talk is finally out! Link to video and slides available at aadinternals.com/talks
And yes, @notmynick.bsky.social used some weird filter, I'm not that fat nor old 😜
And yes, @notmynick.bsky.social used some weird filter, I'm not that fat nor old 😜

March 11, 2025 at 5:14 PM
My @disobeyfi.bsky.social talk is finally out! Link to video and slides available at aadinternals.com/talks
And yes, @notmynick.bsky.social used some weird filter, I'm not that fat nor old 😜
And yes, @notmynick.bsky.social used some weird filter, I'm not that fat nor old 😜

