👇🏼👇🏼👇🏼
go.bsky.app/P9JUTfw
This one works by tricking users into copying a file path in Windows Explorer.
Attackers modify the clipboard, so you're actually pasting and running PowerShell ahead of the file path
mrd0x.com/filefix-clic...

This one works by tricking users into copying a file path in Windows Explorer.
Attackers modify the clipboard, so you're actually pasting and running PowerShell ahead of the file path
mrd0x.com/filefix-clic...
Details here: citizenlab.ca/2025/06/firs...
@billmarczak.org @jsrailton.bsky.social

Details here: citizenlab.ca/2025/06/firs...
@billmarczak.org @jsrailton.bsky.social
Spoiler 1: quality is =, speed is ++.
Spoiler 2: do not expect to get good results in a single question.
arxiv.org/pdf/2504.07574
cc: @radareorg.bsky.social #arxiv #radare2

Spoiler 1: quality is =, speed is ++.
Spoiler 2: do not expect to get good results in a single question.
arxiv.org/pdf/2504.07574
cc: @radareorg.bsky.social #arxiv #radare2


Hindsight v2025.03 focuses on Extensions - parsing more activity and state records, highlighting Extension permissions, and making it easier to examine Manifests.
🌐 Blog: dfir.blog/hindsight-pa...
🛠️ Tool download: hindsig.ht/release
#DFIR #Chrome #Extensions

Hindsight v2025.03 focuses on Extensions - parsing more activity and state records, highlighting Extension permissions, and making it easier to examine Manifests.
🌐 Blog: dfir.blog/hindsight-pa...
🛠️ Tool download: hindsig.ht/release
#DFIR #Chrome #Extensions
Start your hunt now 👉 hunting.abuse.ch
Start your hunt now 👉 hunting.abuse.ch
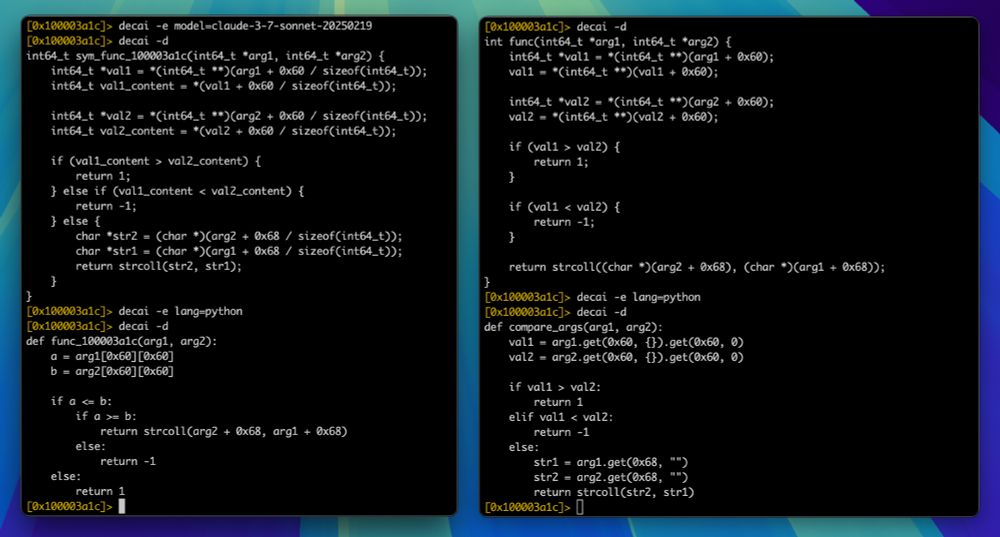


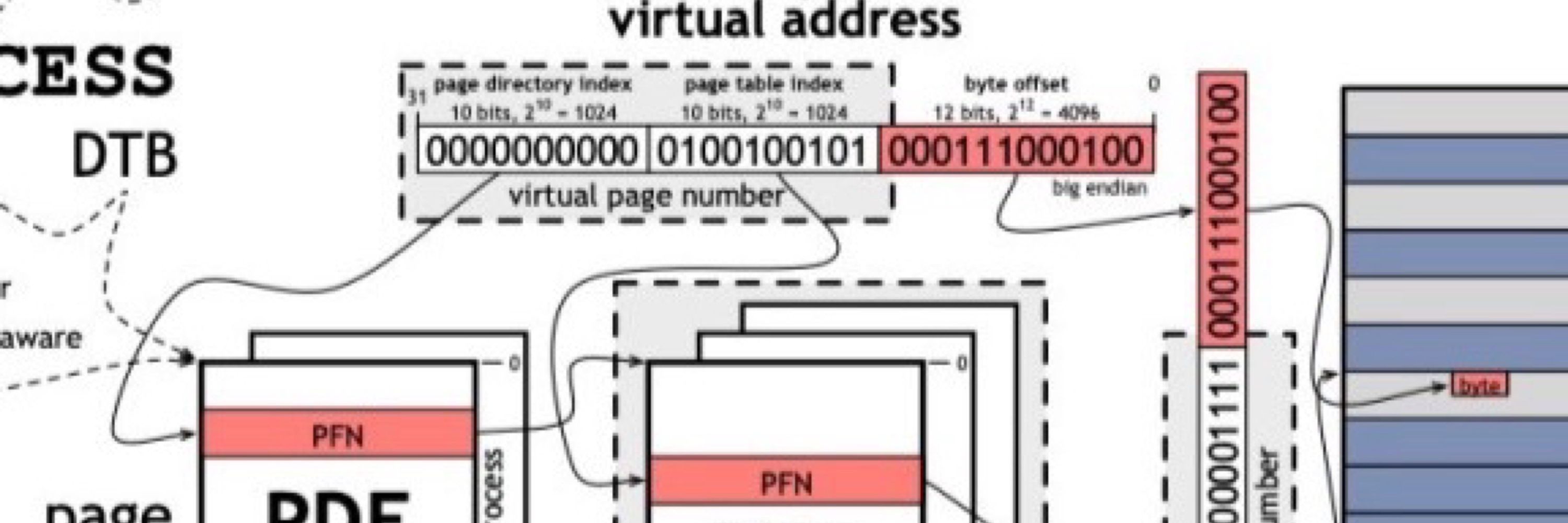
👉 blog.scrt.ch/2025/02/18/r...
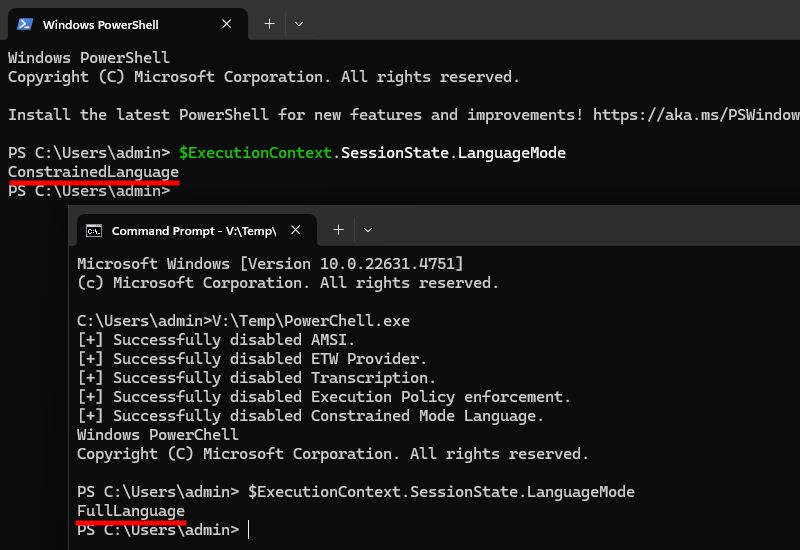
👉 blog.scrt.ch/2025/02/18/r...
#dfir #threatintel #m365security
#dfir #threatintel #m365security
As always, Victor and the contributors are cranking out quality improvements!
In particular, check out the docs on how to use the formatter and linter and open issues (or tell me somehow) if you hit bugs or have things you want to see.
As always, Victor and the contributors are cranking out quality improvements!
In particular, check out the docs on how to use the formatter and linter and open issues (or tell me somehow) if you hit bugs or have things you want to see.
vertex.link/blogs/catego...

vertex.link/blogs/catego...
Rule: github.com/mgreen27/100...
VQL: github.com/mgreen27/100...



Rule: github.com/mgreen27/100...
VQL: github.com/mgreen27/100...
www.youtube.com/watc...
Grab Venture here: github.com/mttaggart...

www.youtube.com/watc...
Grab Venture here: github.com/mttaggart...

github.com/Santandersec...

github.com/Santandersec...

github.com/yo-yo-yo-jbo...

github.com/yo-yo-yo-jbo...



