Binni Shah
@binitamshah.bsky.social
Linux Evangelist, Malwares , Security Enthusiast, Investor, Contrarian , Neurology , Philanthropist , Reformist ,Sigma female
Pinned
Binni Shah
@binitamshah.bsky.social
· May 18
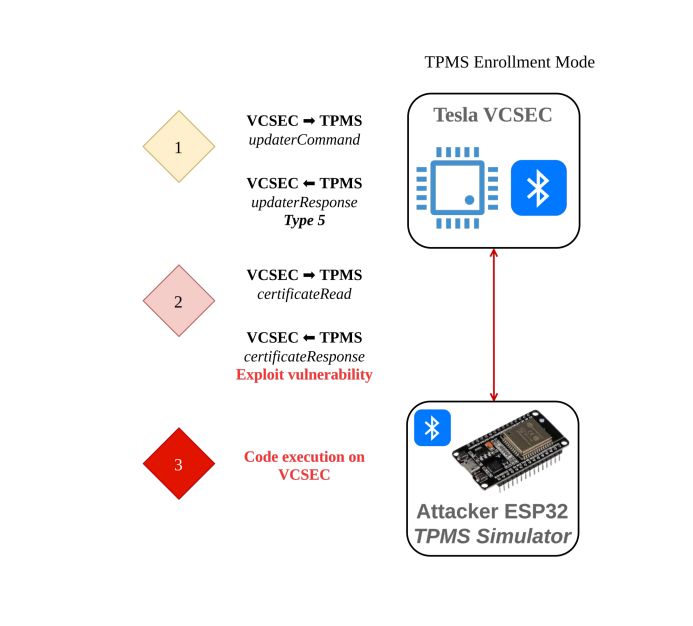
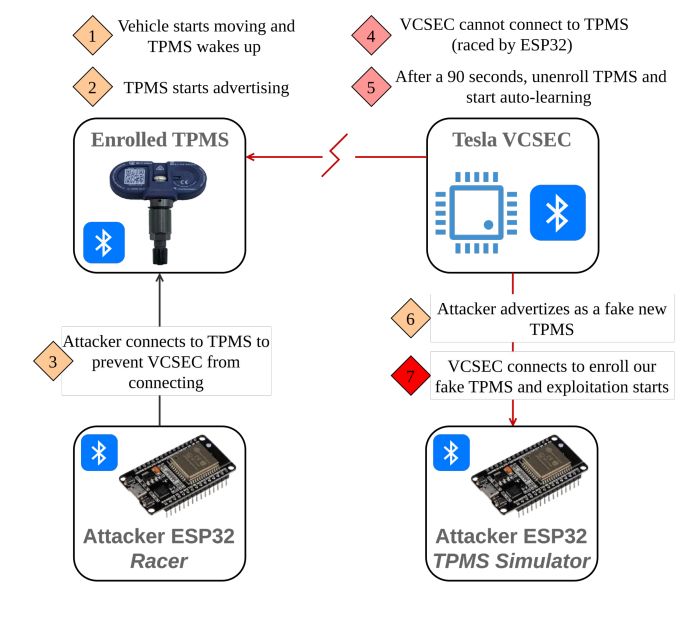
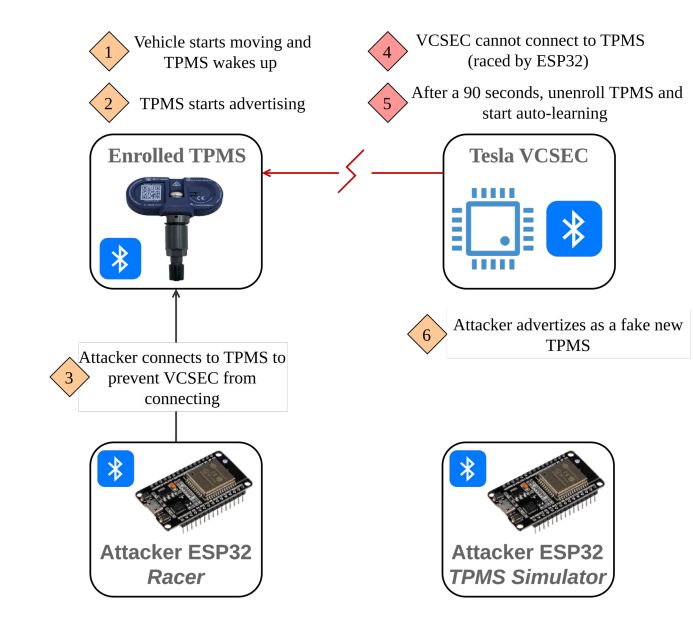
0-click RCE on Tesla Model 3 through TPMS Sensors : www.synacktiv.com/sites/defaul... credits @masthoon @vdehors
Linux Reverse Shell in x86 Assembly : rootfu.in/linux-revers...
Linux Reverse Shell in x86 Assembly - ROOTFU.IN
Introduction: Why Build a Reverse Shell in Assembly? Ever wondered how low-level code can create a powerful remote shell? In this post, we’ll dive into crafting a Linux reverse shell using x86 assembl...
rootfu.in
May 21, 2025 at 1:33 PM
Linux Reverse Shell in x86 Assembly : rootfu.in/linux-revers...
300 Milliseconds to Admin: Mastering DLL Hijacking and Hooking to Win the Race (CVE-2025-24076 and CVE-2025-24994) : blog.compass-security.com/2025/04/3-mi...
May 20, 2025 at 7:25 AM
300 Milliseconds to Admin: Mastering DLL Hijacking and Hooking to Win the Race (CVE-2025-24076 and CVE-2025-24994) : blog.compass-security.com/2025/04/3-mi...
Bypassing kASLR via Cache Timing : r0keb.github.io/posts/Bypass...
kASLR Internals and Evolution : r0keb.github.io/posts/kASLR-... credits @r0keb
kASLR Internals and Evolution : r0keb.github.io/posts/kASLR-... credits @r0keb
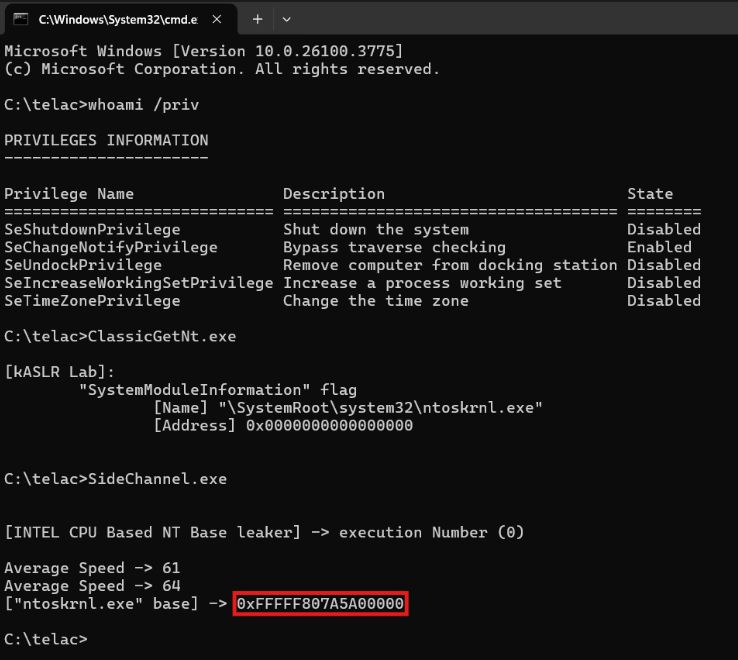
May 20, 2025 at 6:40 AM
Bypassing kASLR via Cache Timing : r0keb.github.io/posts/Bypass...
kASLR Internals and Evolution : r0keb.github.io/posts/kASLR-... credits @r0keb
kASLR Internals and Evolution : r0keb.github.io/posts/kASLR-... credits @r0keb
Cache poisoning via race-condition in Next.js : zhero-web-sec.github.io/research-and... credits @zhero___
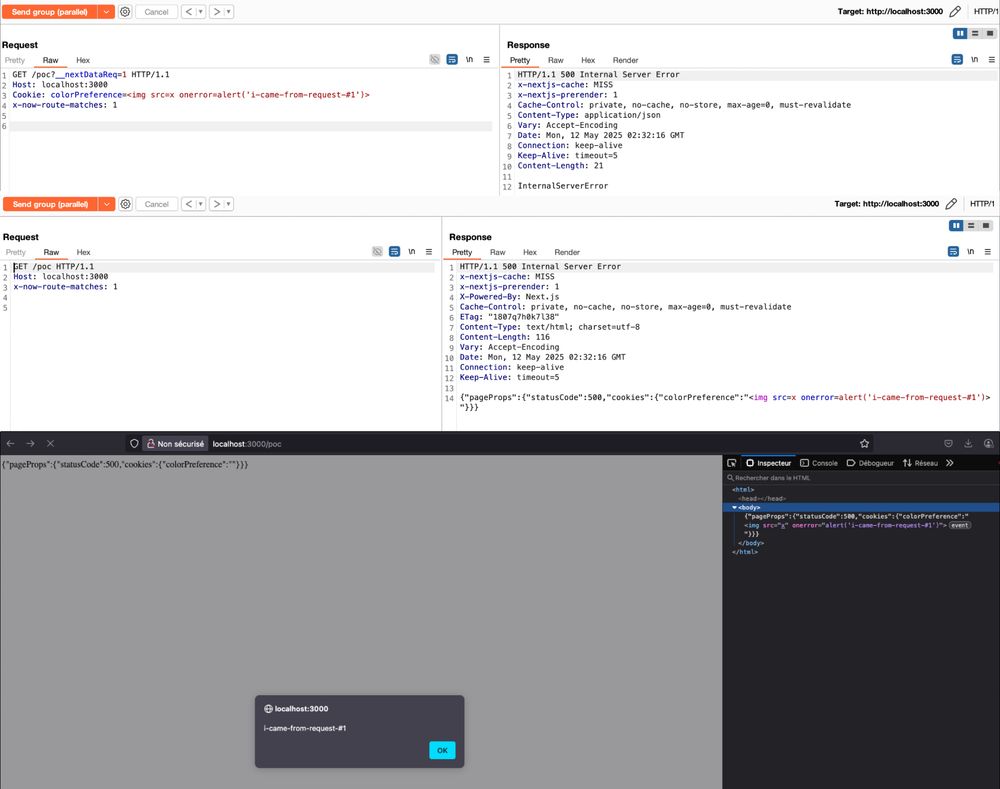
May 20, 2025 at 6:14 AM
Cache poisoning via race-condition in Next.js : zhero-web-sec.github.io/research-and... credits @zhero___
O2 VoLTE : Locating any customer with a phone call : mastdatabase.co.uk/blog/2025/05...
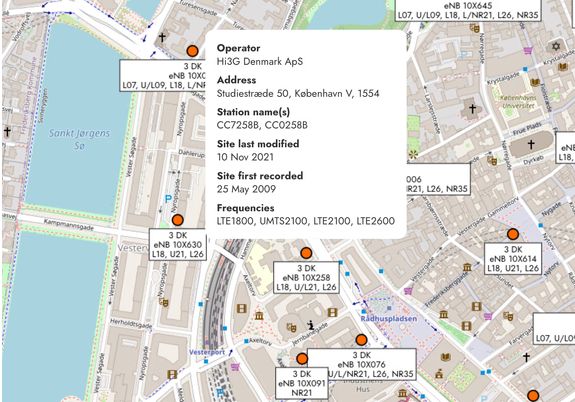
May 20, 2025 at 6:06 AM
O2 VoLTE : Locating any customer with a phone call : mastdatabase.co.uk/blog/2025/05...
Bypassing Web Filters (Part 4) : Host Header Spoofing & Domain Fronting Detection Bypasses : blog.compass-security.com/2025/03/bypa...
3 : Domain Fronting : blog.compass-security.com/2025/03/bypa...
2 : Host Header Spoofing : blog.compass-security.com/2025/03/bypa...
3 : Domain Fronting : blog.compass-security.com/2025/03/bypa...
2 : Host Header Spoofing : blog.compass-security.com/2025/03/bypa...

Bypassing Web Filters Part 4: Host Header Spoofing & Domain Fronting Detection Bypasses – Compass Security Blog
But – as you know – no system is perfect. This last post of the series discusses techniques that can sometimes be used to bypass domain fronting detection and prevention methods.
blog.compass-security.com
May 18, 2025 at 2:55 PM
Bypassing Web Filters (Part 4) : Host Header Spoofing & Domain Fronting Detection Bypasses : blog.compass-security.com/2025/03/bypa...
3 : Domain Fronting : blog.compass-security.com/2025/03/bypa...
2 : Host Header Spoofing : blog.compass-security.com/2025/03/bypa...
3 : Domain Fronting : blog.compass-security.com/2025/03/bypa...
2 : Host Header Spoofing : blog.compass-security.com/2025/03/bypa...
Game Hacking : Part 1 - Land Of The PEB - Modules and DLLs : codeneverdies.github.io/posts/lotp-1/
Part 2 : Running from the debugger : codeneverdies.github.io/posts/lotp-2/
Part 3: BakkesMod : codeneverdies.github.io/posts/gh-1/
4 : Valve Anti-Cheat (VAC) : codeneverdies.github.io/posts/gh-2/
Part 2 : Running from the debugger : codeneverdies.github.io/posts/lotp-2/
Part 3: BakkesMod : codeneverdies.github.io/posts/gh-1/
4 : Valve Anti-Cheat (VAC) : codeneverdies.github.io/posts/gh-2/
1. Land Of The PEB - Modules and DLLs
Welcome to my first series called “Land Of The PEB” where I will be discussing various topics related to the Process Environment Block (PEB).
What is this thing? The Process Environment Block (we will...
codeneverdies.github.io
May 18, 2025 at 1:52 PM
Game Hacking : Part 1 - Land Of The PEB - Modules and DLLs : codeneverdies.github.io/posts/lotp-1/
Part 2 : Running from the debugger : codeneverdies.github.io/posts/lotp-2/
Part 3: BakkesMod : codeneverdies.github.io/posts/gh-1/
4 : Valve Anti-Cheat (VAC) : codeneverdies.github.io/posts/gh-2/
Part 2 : Running from the debugger : codeneverdies.github.io/posts/lotp-2/
Part 3: BakkesMod : codeneverdies.github.io/posts/gh-1/
4 : Valve Anti-Cheat (VAC) : codeneverdies.github.io/posts/gh-2/
0-click RCE on Tesla Model 3 through TPMS Sensors : www.synacktiv.com/sites/defaul... credits @masthoon @vdehors



May 18, 2025 at 11:34 AM
0-click RCE on Tesla Model 3 through TPMS Sensors : www.synacktiv.com/sites/defaul... credits @masthoon @vdehors
PE32 Ransomware : A New Telegram-Based Threat on the Rise : any.run/cybersecurit... credits @MauroEldritch

PE32 Ransomware: A New Telegram-Based Threat on the Rise - ANY.RUN's Cybersecurity Blog
Read technical analysis of PE32, a new ransomware strain that demands ransom for both decryption and not leaking stolen data.
any.run
May 17, 2025 at 1:11 PM
PE32 Ransomware : A New Telegram-Based Threat on the Rise : any.run/cybersecurit... credits @MauroEldritch
Evolution of Tycoon 2FA Defense Evasion Mechanisms : Analysis and Timeline : any.run/cybersecurit...
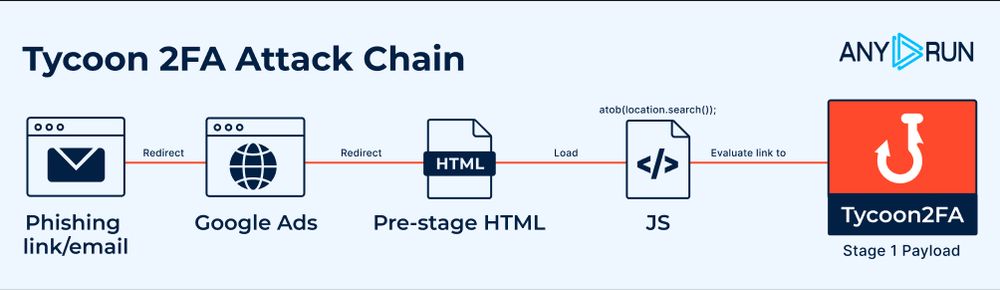
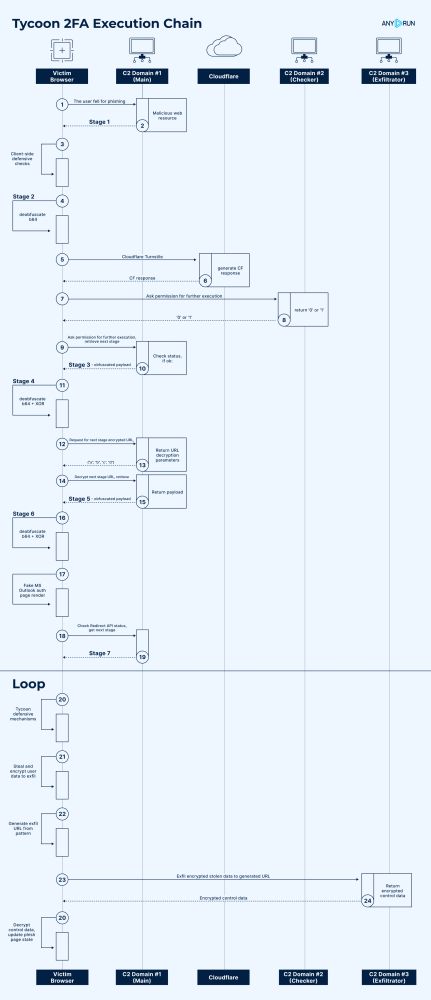
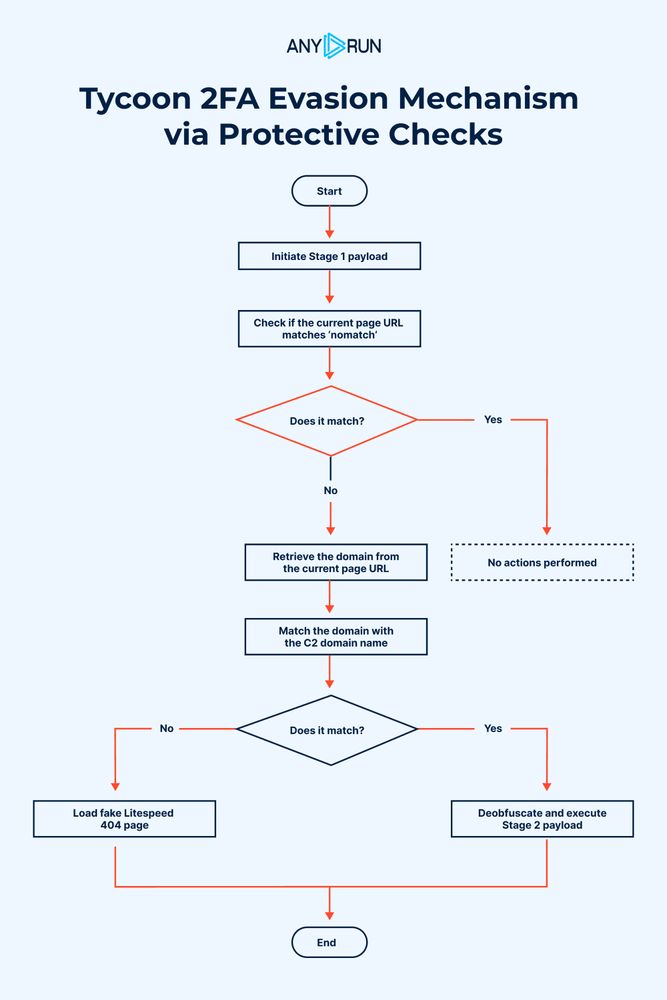
May 17, 2025 at 1:00 PM
Evolution of Tycoon 2FA Defense Evasion Mechanisms : Analysis and Timeline : any.run/cybersecurit...
HTML to PDF Renderer : A tale of local file access and shellcode execution : neodyme.io/en/blog/html...
May 17, 2025 at 12:55 PM
HTML to PDF Renderer : A tale of local file access and shellcode execution : neodyme.io/en/blog/html...
Fileless Execution : PowerShell Based Shellcode Loader Executes Remcos RAT : blog.qualys.com/vulnerabilit...
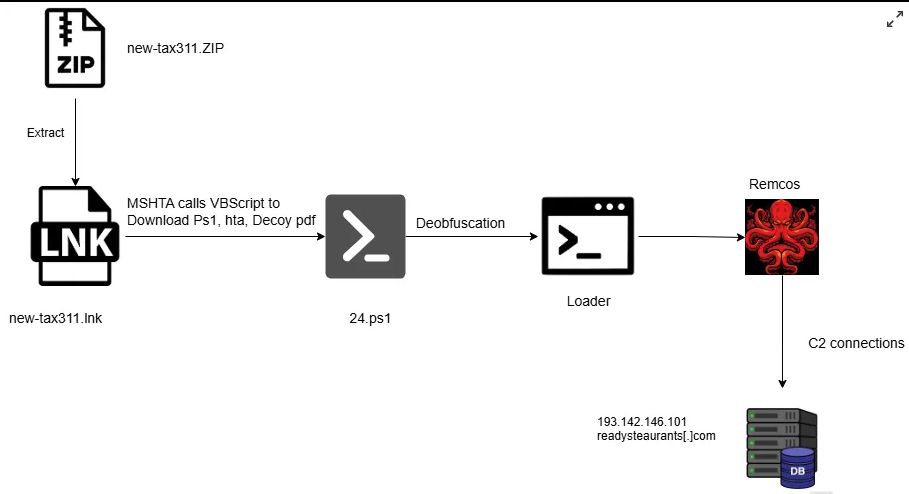
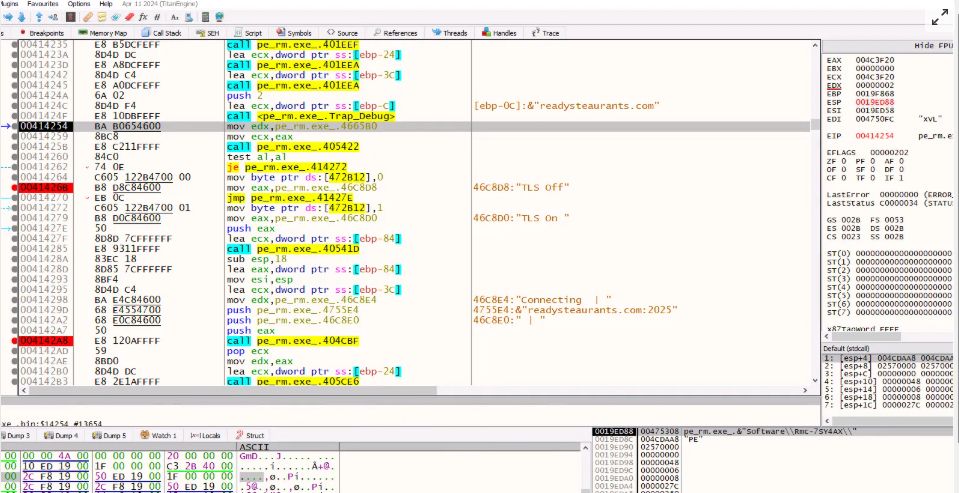
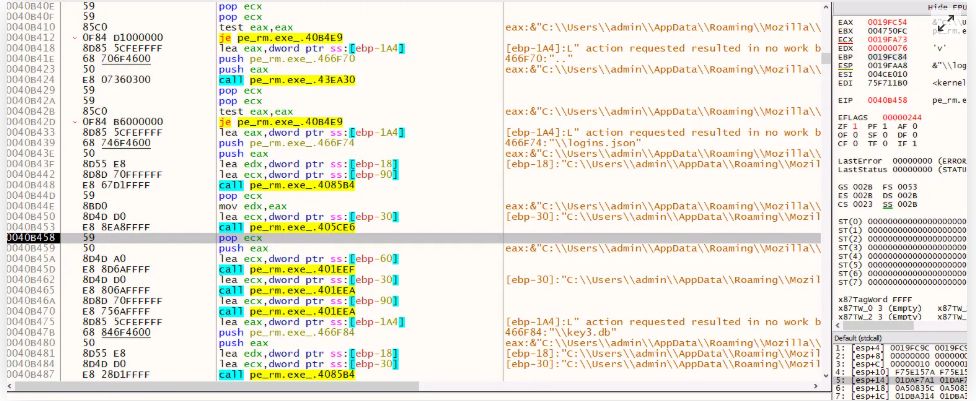
May 17, 2025 at 9:16 AM
Fileless Execution : PowerShell Based Shellcode Loader Executes Remcos RAT : blog.qualys.com/vulnerabilit...
Breaking up-to-date Windows 11 BitLocker encryption -- on-device but software-only : neodyme.io/en/blog/bitl...
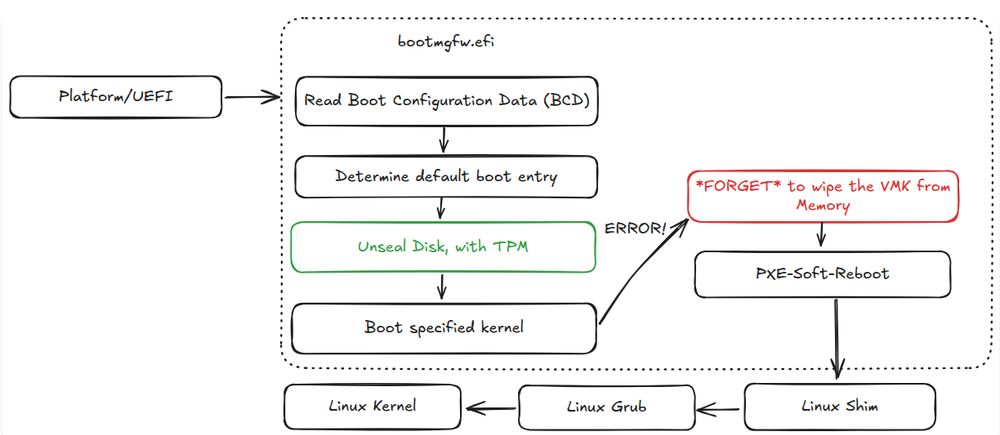
May 17, 2025 at 9:04 AM
Breaking up-to-date Windows 11 BitLocker encryption -- on-device but software-only : neodyme.io/en/blog/bitl...
Researchers Expose New Intel CPU Flaws Enabling Memory Leaks and Spectre v2 Attacks : ethz.ch/en/news-and-...
Ref :
*Speculative calculations open a backdoor to information theft (*2022) : ethz.ch/en/news-and-...
RETBLEED : www.usenix.org/system/files...
Ref :
*Speculative calculations open a backdoor to information theft (*2022) : ethz.ch/en/news-and-...
RETBLEED : www.usenix.org/system/files...
ETH Zurich researchers discover new security vulnerability in Intel processors
Computer scientists at ETH Zurich discover new class of vulnerabilities in Intel processors, allowing them to break down barriers between different users of a processor using carefully crafted instruc...
ethz.ch
May 17, 2025 at 8:47 AM
Researchers Expose New Intel CPU Flaws Enabling Memory Leaks and Spectre v2 Attacks : ethz.ch/en/news-and-...
Ref :
*Speculative calculations open a backdoor to information theft (*2022) : ethz.ch/en/news-and-...
RETBLEED : www.usenix.org/system/files...
Ref :
*Speculative calculations open a backdoor to information theft (*2022) : ethz.ch/en/news-and-...
RETBLEED : www.usenix.org/system/files...
Mastering Rate Limit Bypass Techniques : infosecwriteups.com/mastering-ra...
Mastering Rate Limit Bypass Techniques
Learn How Hackers Bypass Rate Limits — and How You Can Too
infosecwriteups.com
May 17, 2025 at 8:22 AM
Mastering Rate Limit Bypass Techniques : infosecwriteups.com/mastering-ra...
Hacking Casino - How Math Beats the Casino Odds : www.youtube.com/watch?v=87Fg...
Shuffle Up and Deal: Analyzing the Security of Automated Card Shufflers : i.blackhat.com/BH-US-23/Pre...
How To Rob a Casino : 0x00sec.org/t/how-to-rob...
Shuffle Up and Deal: Analyzing the Security of Automated Card Shufflers : i.blackhat.com/BH-US-23/Pre...
How To Rob a Casino : 0x00sec.org/t/how-to-rob...

Hacking Casino | How Math Beats the Casino Odds
YouTube video by Sumsub
www.youtube.com
May 17, 2025 at 8:19 AM
Hacking Casino - How Math Beats the Casino Odds : www.youtube.com/watch?v=87Fg...
Shuffle Up and Deal: Analyzing the Security of Automated Card Shufflers : i.blackhat.com/BH-US-23/Pre...
How To Rob a Casino : 0x00sec.org/t/how-to-rob...
Shuffle Up and Deal: Analyzing the Security of Automated Card Shufflers : i.blackhat.com/BH-US-23/Pre...
How To Rob a Casino : 0x00sec.org/t/how-to-rob...
Writing a Self-Mutating Malware : 0x00sec.org/t/writing-a-...
Metamorphic Code Examples : stackoverflow.com/questions/10...
Metamorphic Code Examples : stackoverflow.com/questions/10...

Writing a Self-Mutating Malware
This topic was automatically closed after 121 days. New replies are no longer allowed.
0x00sec.org
May 17, 2025 at 7:29 AM
Writing a Self-Mutating Malware : 0x00sec.org/t/writing-a-...
Metamorphic Code Examples : stackoverflow.com/questions/10...
Metamorphic Code Examples : stackoverflow.com/questions/10...
How To Rob a Casino : 0x00sec.org/t/how-to-rob...

How To Rob a Casino
Casinos, some view these places as something that corrupts the soul, leading individuals astray with the allure of easy money and instant gratification. Others see casinos as an escape from reality, s...
0x00sec.org
May 17, 2025 at 7:26 AM
How To Rob a Casino : 0x00sec.org/t/how-to-rob...
macOS Malware Development (Part 2) : 0x00sec.org/t/macos-malw...
Part 1 : 0x00sec.org/t/macos-malw...
Ref :
Inside a Hello World executable on OS X : adrummond.net/posts/macho
The Mystery of Mach-O Object Structure : alexdremov.me/mystery-of-m...
www2.cs.arizona.edu/~collberg/Te...
Part 1 : 0x00sec.org/t/macos-malw...
Ref :
Inside a Hello World executable on OS X : adrummond.net/posts/macho
The Mystery of Mach-O Object Structure : alexdremov.me/mystery-of-m...
www2.cs.arizona.edu/~collberg/Te...

macOS Malware Development II
Today’s post is about writing fully custom malware targeting macOS. We’ll walk through its architecture, mutation techniques, and anti-analysis methods, with a focus on Mach-O internals and Darwin AP...
0x00sec.org
May 17, 2025 at 7:20 AM
macOS Malware Development (Part 2) : 0x00sec.org/t/macos-malw...
Part 1 : 0x00sec.org/t/macos-malw...
Ref :
Inside a Hello World executable on OS X : adrummond.net/posts/macho
The Mystery of Mach-O Object Structure : alexdremov.me/mystery-of-m...
www2.cs.arizona.edu/~collberg/Te...
Part 1 : 0x00sec.org/t/macos-malw...
Ref :
Inside a Hello World executable on OS X : adrummond.net/posts/macho
The Mystery of Mach-O Object Structure : alexdremov.me/mystery-of-m...
www2.cs.arizona.edu/~collberg/Te...
Fuzzing Windows ARM64 closed-source binary : www.romainthomas.fr/post/25-04-w...
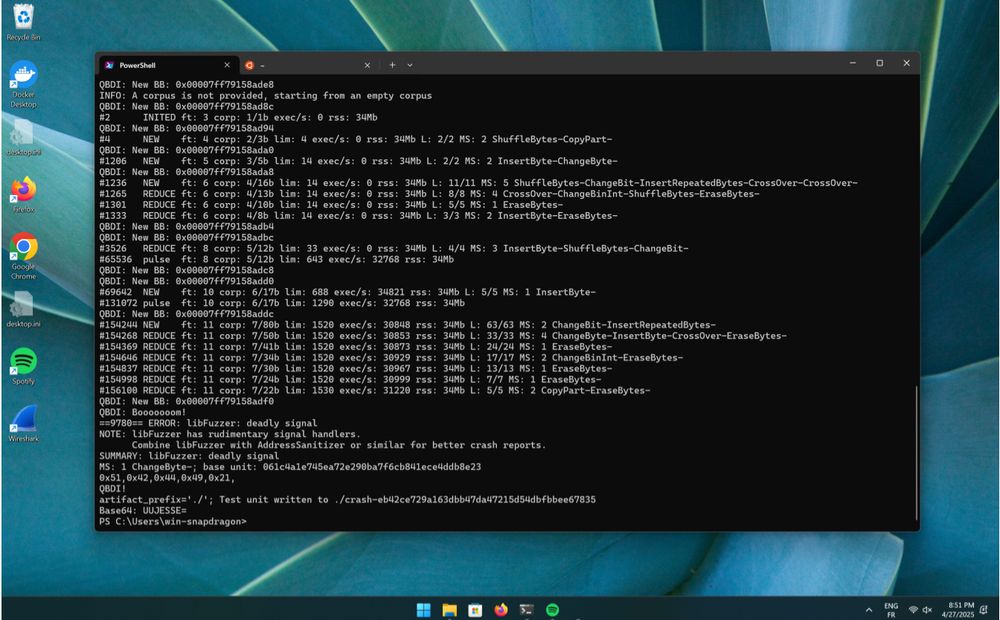
May 17, 2025 at 6:15 AM
Fuzzing Windows ARM64 closed-source binary : www.romainthomas.fr/post/25-04-w...
Litterbox : Sandbox approach for malware developers and red teamers to test payloads against detection mechanisms before deployment : github.com/BlackSnufkin...
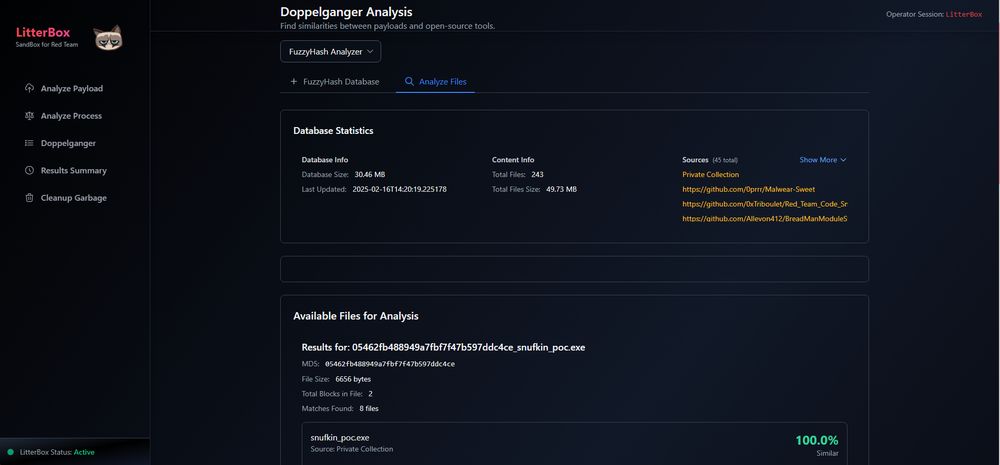
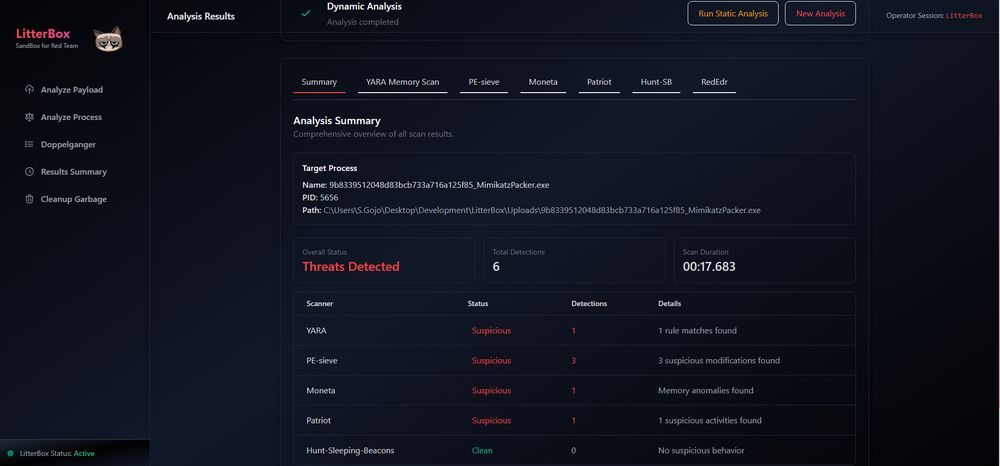
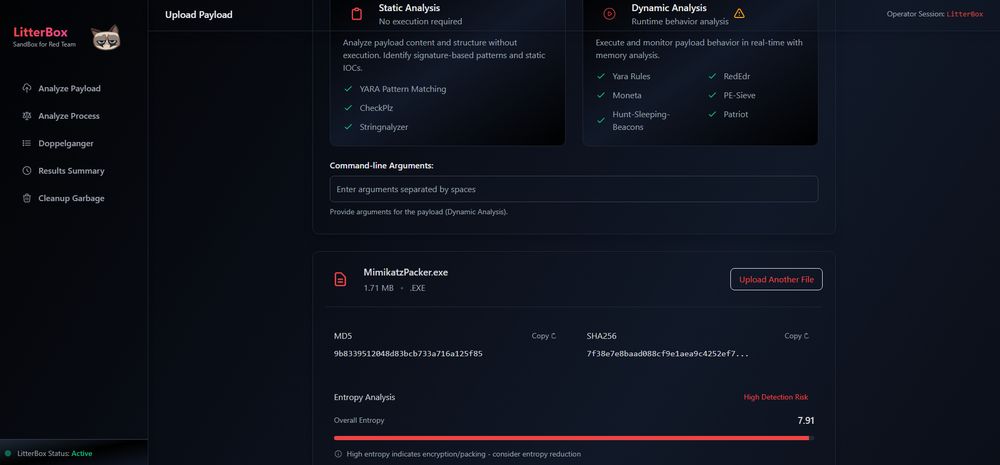
May 17, 2025 at 6:04 AM
Litterbox : Sandbox approach for malware developers and red teamers to test payloads against detection mechanisms before deployment : github.com/BlackSnufkin...
Pupkin : a deceptively simple .NET-based stealer designed to harvest browser passwords, Discord tokens, and Telegram sessions — all controlled silently through a Telegram C2 : muff-in.github.io/blog/pupkin-...
Pupkin: A Simple .NET Info-Stealer Exfiltrating Data via Telegram
Pupkin Stealer is a deceptively simple .NET-based stealer designed to harvest browser passwords, Discord tokens, and Telegram sessions — all controlled silently through a Telegram C2.
muff-in.github.io
May 2, 2025 at 4:25 PM
Pupkin : a deceptively simple .NET-based stealer designed to harvest browser passwords, Discord tokens, and Telegram sessions — all controlled silently through a Telegram C2 : muff-in.github.io/blog/pupkin-...
Linux running in Excel : github.com/NSG650/Linux...
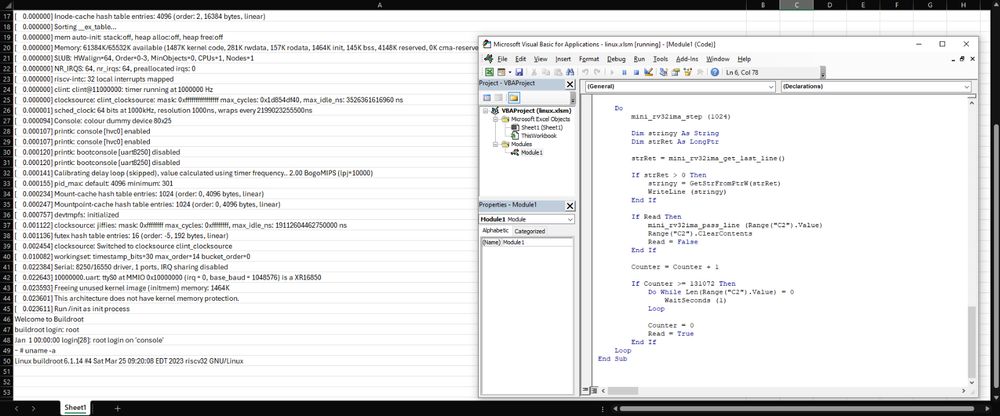
May 2, 2025 at 3:46 PM
Linux running in Excel : github.com/NSG650/Linux...
felix86 : Run x86-64 programs on RISC-V Linux : github.com/OFFTKP/felix86
GitHub - OFFTKP/felix86: Run x86-64 programs on RISC-V Linux
Run x86-64 programs on RISC-V Linux. Contribute to OFFTKP/felix86 development by creating an account on GitHub.
github.com
May 2, 2025 at 3:37 PM
felix86 : Run x86-64 programs on RISC-V Linux : github.com/OFFTKP/felix86
LigerLabs - Educational Modules for (Anti-)Reverse Engineering : ligerlabs.org
Home
ligerlabs.org
May 1, 2025 at 3:53 PM
LigerLabs - Educational Modules for (Anti-)Reverse Engineering : ligerlabs.org

