
Gerald Benischke
@beny23.github.io
Maker, breaker and fixer of software. Adventures in #appsec and #agile: beny23.github.io he/him
Brb, just broom scrolling

October 28, 2025 at 8:29 AM
Brb, just broom scrolling
Little Bobby Tables would proud. imgs.xkcd.com/comics/explo...

October 15, 2025 at 9:43 AM
Little Bobby Tables would proud. imgs.xkcd.com/comics/explo...
Just like all the crypto mining infrastructure was reused. Wait what? ;-)

October 11, 2025 at 11:01 AM
Just like all the crypto mining infrastructure was reused. Wait what? ;-)
@safesecs.bsky.social closing #bsidesncl - thank you to everyone, it was fab!!!

September 27, 2025 at 5:01 PM
@safesecs.bsky.social closing #bsidesncl - thank you to everyone, it was fab!!!
It wouldn’t be a @rnbwkat.bsky.social talk without honeypots!
Great whirlwind tour of “just do the fucking basics already”!!!
Loved it.
9/fin
Great whirlwind tour of “just do the fucking basics already”!!!
Loved it.
9/fin


September 27, 2025 at 4:56 PM
It wouldn’t be a @rnbwkat.bsky.social talk without honeypots!
Great whirlwind tour of “just do the fucking basics already”!!!
Loved it.
9/fin
Great whirlwind tour of “just do the fucking basics already”!!!
Loved it.
9/fin
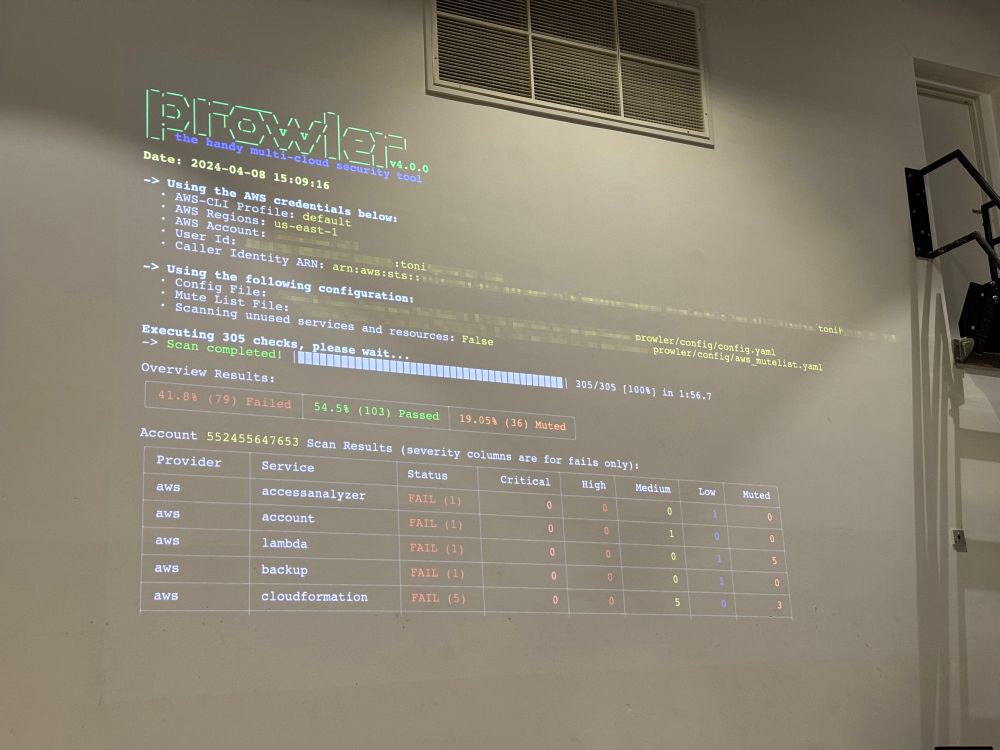
It’s funny how a simple hardcoded credential can lead to complete takeover: 8/n

September 27, 2025 at 4:56 PM
It’s funny how a simple hardcoded credential can lead to complete takeover: 8/n


September 27, 2025 at 4:56 PM
Some tools to help: 6/n

September 27, 2025 at 4:56 PM
Some tools to help: 6/n
It’s the usual suspects: 5/n


September 27, 2025 at 4:56 PM
It’s the usual suspects: 5/n
It takes minutes for a leaked key to be exploited. Usually it’s crypto miners. But sometimes crypto is used as a decoy. 4/n

September 27, 2025 at 4:56 PM
It takes minutes for a leaked key to be exploited. Usually it’s crypto miners. But sometimes crypto is used as a decoy. 4/n
It’s used to be much work pentesting. Now it’s just about finding misconfigrations. Or people accidentally uploading creds. 3/n

September 27, 2025 at 4:56 PM
It’s used to be much work pentesting. Now it’s just about finding misconfigrations. Or people accidentally uploading creds. 3/n
With 1400 different privileges, is it any wonder that it’s so easy to misconfigure. 2/n



September 27, 2025 at 4:56 PM
With 1400 different privileges, is it any wonder that it’s so easy to misconfigure. 2/n
@rnbwkat.bsky.social doing the lock note at #bsidesncl about cloud misconfiguration.
So most of the incidents then.
1/n
So most of the incidents then.
1/n

September 27, 2025 at 4:56 PM
@rnbwkat.bsky.social doing the lock note at #bsidesncl about cloud misconfiguration.
So most of the incidents then.
1/n
So most of the incidents then.
1/n
Top tip: “different phones for fun and profit”. And adopt an elderly person.
That was fun!
But how do I launder money, we’ve not learned that yet ;-)
8/fin
That was fun!
But how do I launder money, we’ve not learned that yet ;-)
8/fin


September 27, 2025 at 2:26 PM
Top tip: “different phones for fun and profit”. And adopt an elderly person.
That was fun!
But how do I launder money, we’ve not learned that yet ;-)
8/fin
That was fun!
But how do I launder money, we’ve not learned that yet ;-)
8/fin
Incident maps illustrate dangers and possible mitigations. 7/n



September 27, 2025 at 2:26 PM
Incident maps illustrate dangers and possible mitigations. 7/n
Then we look at incidents that can lead to dirty money. 6/n

September 27, 2025 at 2:26 PM
Then we look at incidents that can lead to dirty money. 6/n
And of course it’s not really anonymous because the blockchain is public after all. Despite all kinds of crypto tech that enables laundering. 5/n


September 27, 2025 at 2:26 PM
And of course it’s not really anonymous because the blockchain is public after all. Despite all kinds of crypto tech that enables laundering. 5/n
There’s a fundamental weakness in crypto. It doesn’t care who should own it. Only knowing the private key matters.
Make a mistake: all your money gone.
Lose your key: all your money gone.
Great - future of finance right there.
4/n
Make a mistake: all your money gone.
Lose your key: all your money gone.
Great - future of finance right there.
4/n

September 27, 2025 at 2:26 PM
There’s a fundamental weakness in crypto. It doesn’t care who should own it. Only knowing the private key matters.
Make a mistake: all your money gone.
Lose your key: all your money gone.
Great - future of finance right there.
4/n
Make a mistake: all your money gone.
Lose your key: all your money gone.
Great - future of finance right there.
4/n
Can’t talk about money laundering without the blockchain. Crypto is an enabler. How is this not illegal. 💯
3/n
3/n

September 27, 2025 at 2:26 PM
Can’t talk about money laundering without the blockchain. Crypto is an enabler. How is this not illegal. 💯
3/n
3/n
Laundering money is about hiding money you shouldn’t have from the tax man.
Hiding many that is yours is fine, bike to work, pensions are tax avoidance. Every does that.
Tax evasion is not. But at least it was your money. 2/n
Hiding many that is yours is fine, bike to work, pensions are tax avoidance. Every does that.
Tax evasion is not. But at least it was your money. 2/n

September 27, 2025 at 2:26 PM
Laundering money is about hiding money you shouldn’t have from the tax man.
Hiding many that is yours is fine, bike to work, pensions are tax avoidance. Every does that.
Tax evasion is not. But at least it was your money. 2/n
Hiding many that is yours is fine, bike to work, pensions are tax avoidance. Every does that.
Tax evasion is not. But at least it was your money. 2/n
Chris King talks about money laundering at #bsidesncl. It’s a full house. Seems like a lot of dodgy people. 1/n


September 27, 2025 at 2:26 PM
Chris King talks about money laundering at #bsidesncl. It’s a full house. Seems like a lot of dodgy people. 1/n
Example: take control of robotic arms because their jobs were uploaded to the controllers by FTP…
So not that different to legacy IT ;-)
6/fin
So not that different to legacy IT ;-)
6/fin

September 27, 2025 at 1:44 PM
Example: take control of robotic arms because their jobs were uploaded to the controllers by FTP…
So not that different to legacy IT ;-)
6/fin
So not that different to legacy IT ;-)
6/fin




