Azeria
@azeria-labs.com
Founder of Azeria Labs, Trainer, Author of Blue Fox: Arm Assembly Internals & Reverse Engineering
Whoever is reading this stuff in Chinese is on a different level haha
January 17, 2025 at 8:08 PM
Whoever is reading this stuff in Chinese is on a different level haha
The Chinese translation of my book is out and just arrived in the mail! How cool is that?! Still can’t believe this is real 🩵

January 17, 2025 at 8:06 PM
The Chinese translation of my book is out and just arrived in the mail! How cool is that?! Still can’t believe this is real 🩵
Just got the physical copy in the mail! So exciting!!

January 10, 2025 at 2:43 PM
Just got the physical copy in the mail! So exciting!!
In other news, my book has been translated into Korean! 🤩
Absolutely blown away by that. It’s also being the translated into Polish and Chinese.
Here’s the link to the Korean translation of “Blue Fox: Arm Assembly Internals and Reverse Engineering”: product.kyobobook.co.kr/detail/S0002...
Absolutely blown away by that. It’s also being the translated into Polish and Chinese.
Here’s the link to the Korean translation of “Blue Fox: Arm Assembly Internals and Reverse Engineering”: product.kyobobook.co.kr/detail/S0002...

January 8, 2025 at 8:45 PM
In other news, my book has been translated into Korean! 🤩
Absolutely blown away by that. It’s also being the translated into Polish and Chinese.
Here’s the link to the Korean translation of “Blue Fox: Arm Assembly Internals and Reverse Engineering”: product.kyobobook.co.kr/detail/S0002...
Absolutely blown away by that. It’s also being the translated into Polish and Chinese.
Here’s the link to the Korean translation of “Blue Fox: Arm Assembly Internals and Reverse Engineering”: product.kyobobook.co.kr/detail/S0002...
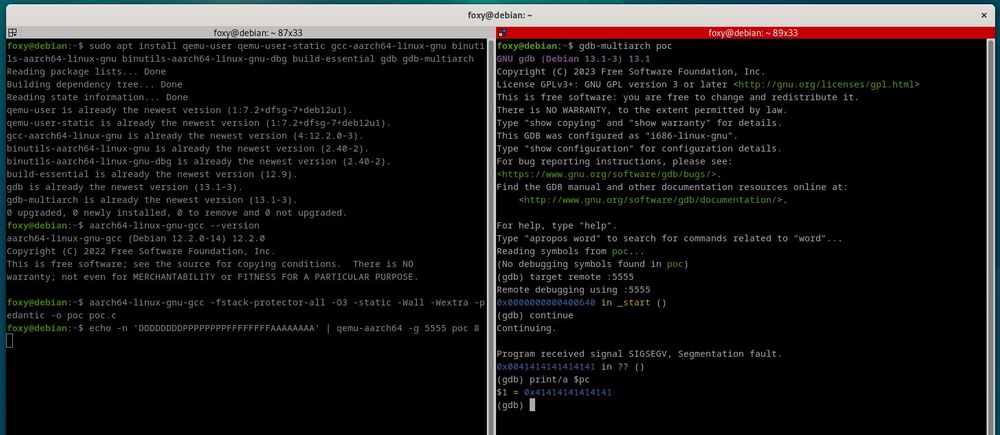
If you want to reproduce this bug with the PoC from the advisory on your x86/64 machine, here’s how:
September 12, 2023 at 4:37 PM
If you want to reproduce this bug with the PoC from the advisory on your x86/64 machine, here’s how:
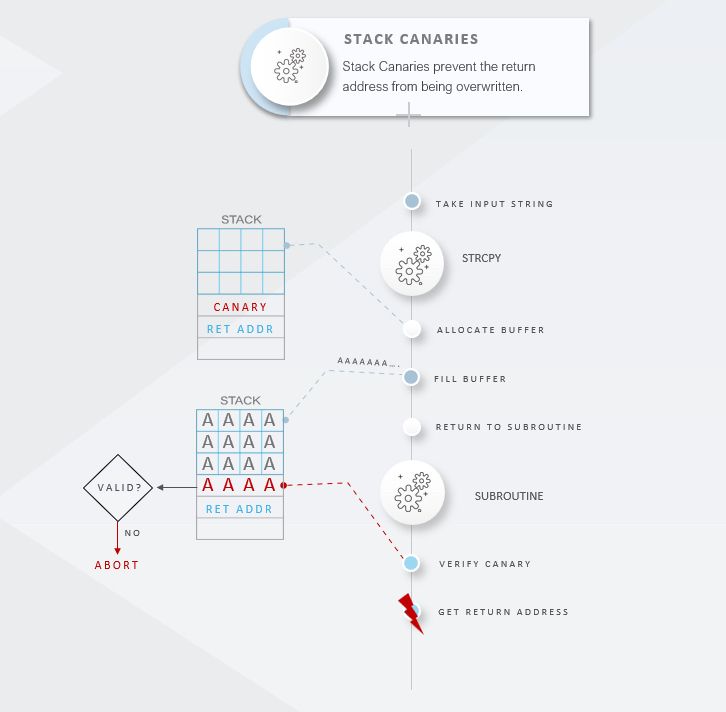
> GCC’s stack protection feature (aka canary) is an exploit mitigation to prevent buffer overflows from overwriting saved registers on the stack to take control over the program flow. It makes exploitation much harder. You often need an additional bug to bypass this mitigation.
September 12, 2023 at 4:36 PM
> GCC’s stack protection feature (aka canary) is an exploit mitigation to prevent buffer overflows from overwriting saved registers on the stack to take control over the program flow. It makes exploitation much harder. You often need an additional bug to bypass this mitigation.
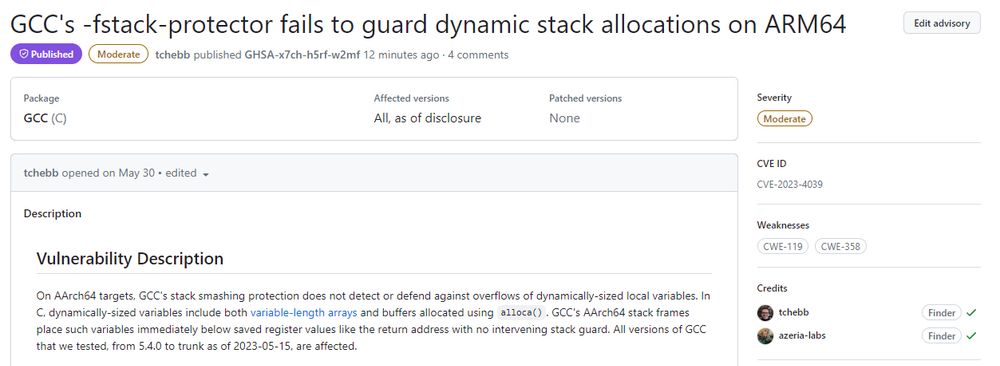
Time for an Arm-twist! CVE-2023-4039
Tom Hebb (Meta red team) and I discovered an 0day in GCC (for AArch64 targets) during my Arm exploitation training.
It renders stack canaries against overflows of dynamically-sized variables useless.
developer.arm.com/Arm%20Securi...
Tom Hebb (Meta red team) and I discovered an 0day in GCC (for AArch64 targets) during my Arm exploitation training.
It renders stack canaries against overflows of dynamically-sized variables useless.
developer.arm.com/Arm%20Securi...
September 12, 2023 at 4:35 PM
Time for an Arm-twist! CVE-2023-4039
Tom Hebb (Meta red team) and I discovered an 0day in GCC (for AArch64 targets) during my Arm exploitation training.
It renders stack canaries against overflows of dynamically-sized variables useless.
developer.arm.com/Arm%20Securi...
Tom Hebb (Meta red team) and I discovered an 0day in GCC (for AArch64 targets) during my Arm exploitation training.
It renders stack canaries against overflows of dynamically-sized variables useless.
developer.arm.com/Arm%20Securi...
I’m doing two book signing sessions in collaboration with Patrick Wardle at Black Hat and Defcon this year! 🥳
Black Hat:
Thursday 8/10 - 12:15pm:
BH Bookstore - Breakers Registration 2
Defcon:
Saturday 8/12 - 11:00am
Caesar’s - Alliance Ballroom - Room 321
Black Hat:
Thursday 8/10 - 12:15pm:
BH Bookstore - Breakers Registration 2
Defcon:
Saturday 8/12 - 11:00am
Caesar’s - Alliance Ballroom - Room 321

August 7, 2023 at 2:30 AM
I’m doing two book signing sessions in collaboration with Patrick Wardle at Black Hat and Defcon this year! 🥳
Black Hat:
Thursday 8/10 - 12:15pm:
BH Bookstore - Breakers Registration 2
Defcon:
Saturday 8/12 - 11:00am
Caesar’s - Alliance Ballroom - Room 321
Black Hat:
Thursday 8/10 - 12:15pm:
BH Bookstore - Breakers Registration 2
Defcon:
Saturday 8/12 - 11:00am
Caesar’s - Alliance Ballroom - Room 321
I can’t believe I’ll be keynoting Black Hat this year 😵
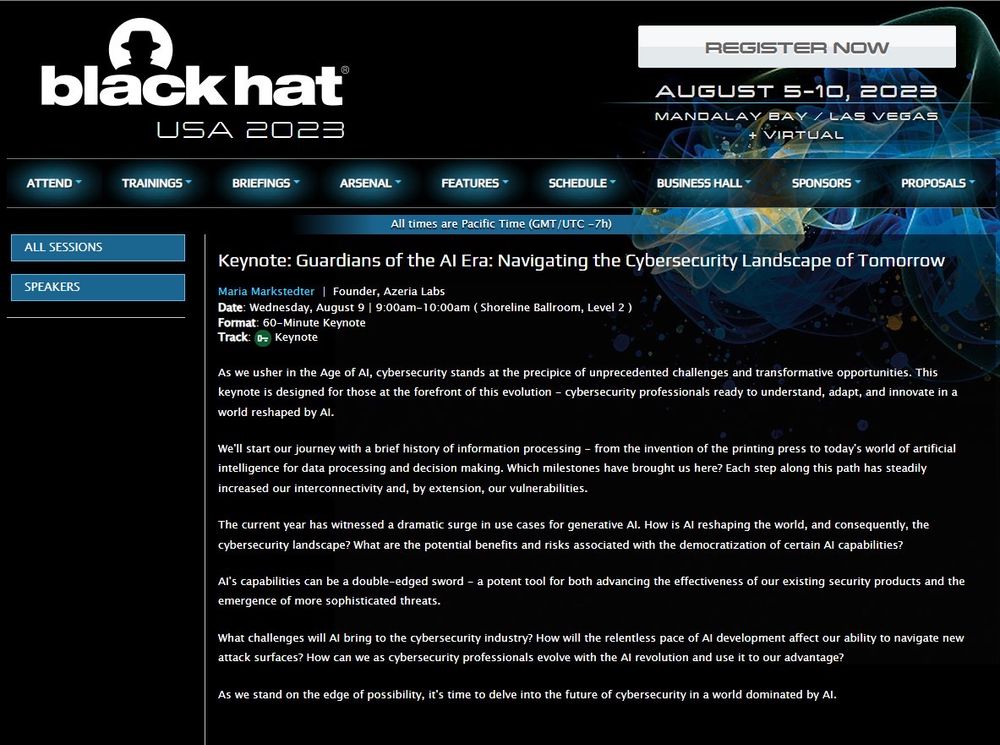
July 7, 2023 at 11:05 AM
I can’t believe I’ll be keynoting Black Hat this year 😵
All the lovely people who posted a photo of their copy of my book. I’m humbled. 🥰
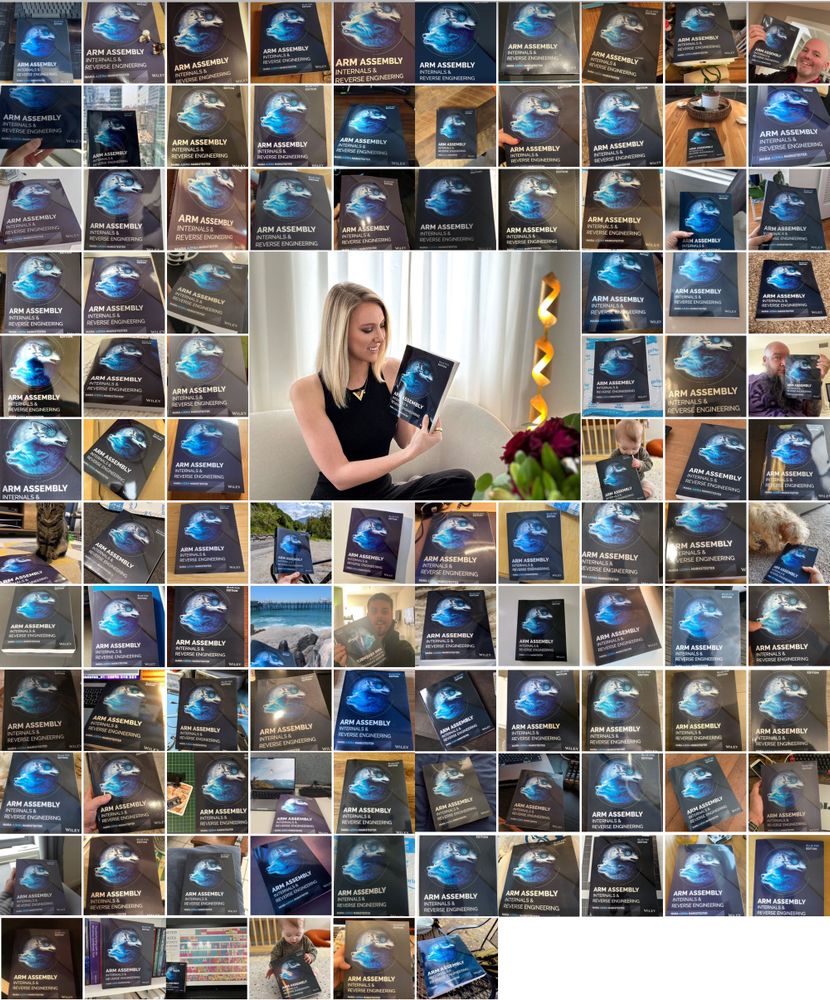
May 13, 2023 at 7:28 AM
All the lovely people who posted a photo of their copy of my book. I’m humbled. 🥰

