
Currently:
- Managing military software supply chains risk
- Mitigating US tech dependencies
- Biotechnology + defense
Author of "Building Bridges in Cyber Diplomacy" (2024). She/her.
Armed forces should pay more attention to their software supply chains. These are complex networks of software components, vendors, service providers, and other companies. /1
Armed forces should pay more attention to their software supply chains. These are complex networks of software components, vendors, service providers, and other companies. /1
Armed forces should pay more attention to their software supply chains. These are complex networks of software components, vendors, service providers, and other companies. /1

Say hi if you would like to chat, for example about my piece on Europe's dependencies on the US in the field of cybersecurity: www.swp-berlin.org/en/publicati...

Say hi if you would like to chat, for example about my piece on Europe's dependencies on the US in the field of cybersecurity: www.swp-berlin.org/en/publicati...

In a list of the most critical web application security risks (OWASP Top 10), "software supply chain failures" rank as #3.
NB: This is only the release candidate, which may still undergo minor edits before final release.
owasp.org/Top10/2025/A...
In a list of the most critical web application security risks (OWASP Top 10), "software supply chain failures" rank as #3.
NB: This is only the release candidate, which may still undergo minor edits before final release.
owasp.org/Top10/2025/A...

My key points:
1. Europe's dependencies on the US in the field of cybersecurity extend well beyond software updates, SaaS, and cloud services and would persist even if a EuroStack were developed. /1
My key points:
1. Europe's dependencies on the US in the field of cybersecurity extend well beyond software updates, SaaS, and cloud services and would persist even if a EuroStack were developed. /1
For inspiration, check out last year's list: bindinghook.com/its-the-most...
All English-language books published in 2021 or later qualify.
For inspiration, check out last year's list: bindinghook.com/its-the-most...
All English-language books published in 2021 or later qualify.
For inspiration, check out last year's list: bindinghook.com/its-the-most...
All English-language books published in 2021 or later qualify.
For inspiration, check out last year's list: bindinghook.com/its-the-most...
All English-language books published in 2021 or later qualify.
Watch this space for a policy analysis on this very topic, out soon!
🧵

Watch this space for a policy analysis on this very topic, out soon!

Für Security.Table habe ich aufgeschrieben,
1. warum das so ist,
2. was daraus für die Bundeswehr folgt, und
3. was Bundespolitik und Bundeswehr dagegen tun können.
Zum Gastbeitrag: table.media/security/tab...

Für Security.Table habe ich aufgeschrieben,
1. warum das so ist,
2. was daraus für die Bundeswehr folgt, und
3. was Bundespolitik und Bundeswehr dagegen tun können.
Zum Gastbeitrag: table.media/security/tab...

Diese Frage treibt mich seit Juni 2024 um. Ein gutes Jahr verbrachte ich also in einem ziemlichen Rabbithole. Das Ergebnis ist heute erschienen: www.swp-berlin.org/publikation/...
🧵⬇️

Diese Frage treibt mich seit Juni 2024 um. Ein gutes Jahr verbrachte ich also in einem ziemlichen Rabbithole. Das Ergebnis ist heute erschienen: www.swp-berlin.org/publikation/...
🧵⬇️
www.swp-berlin.org/publikation/...

www.swp-berlin.org/publikation/...
Unbedingt bewerben!
@liviuhorovitz.bsky.social @julianasuess.bsky.social @alexandrapaulus.bsky.social
„Rückkehr des militärischen Wettbewerbs – Deutschlands Sicherheit zwischen russischer Bedrohung und transatlantischer Ungewissheit“
🕒Vollzeit | befristet bis 31.12.2027
💼E 14 TVöD
📅Frist: 01.11.2025
bindinghook.com/how-cyber-di...

bindinghook.com/how-cyber-di...
www.swp-berlin.org/publikation/...

"Across all models and all tasks, ... in 45% of the tasks, the model introduces a known security flaw into the code.
Security performance has been largely unchanged over time, /1
"Across all models and all tasks, ... in 45% of the tasks, the model introduces a known security flaw into the code.
Security performance has been largely unchanged over time, /1

Die #UNcyberOEWG hat beschlossen, den 1. permanenten VN-Cybersicherheitsdialog zu etablieren.
tl;dr: Die Modalitäten sind not great, aber die deutsche Diplomatie kann an einigen Stellschrauben drehen./1

Die #UNcyberOEWG hat beschlossen, den 1. permanenten VN-Cybersicherheitsdialog zu etablieren.
tl;dr: Die Modalitäten sind not great, aber die deutsche Diplomatie kann an einigen Stellschrauben drehen./1
The content of the report and the modalities of the permanent mechanism are far from perfect, /1

The content of the report and the modalities of the permanent mechanism are far from perfect, /1
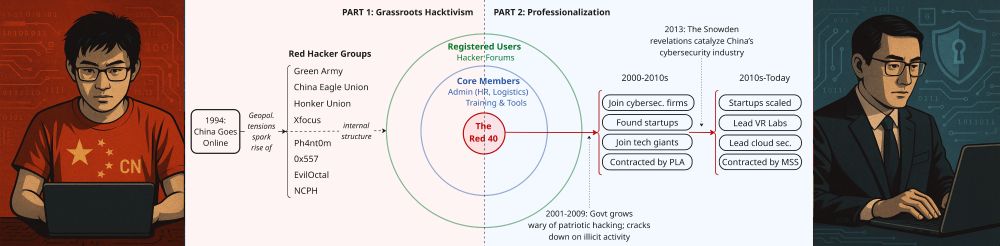
I gathered open source data & interviewed Gov employees, VR and china researchers to figure out what the zero day marketplace looks like in the U.S. and how it compares to China.
key findings below ⬇️- 0/🧵 www.atlanticcouncil.org/in-depth-res...
I gathered open source data & interviewed Gov employees, VR and china researchers to figure out what the zero day marketplace looks like in the U.S. and how it compares to China.
key findings below ⬇️- 0/🧵 www.atlanticcouncil.org/in-depth-res...

