Founder + President of Volexity leading a team of experts that deal w/ complex cyber intrusions from nation-state level intruders. His talk will cover a Chinese APT actor that Volexity tracks as UTA0388.
Check out the official agenda:
cyberwarcon.com

Founder + President of Volexity leading a team of experts that deal w/ complex cyber intrusions from nation-state level intruders. His talk will cover a Chinese APT actor that Volexity tracks as UTA0388.
Check out the official agenda:
cyberwarcon.com

See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...

See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...

See the full details in our blog post: volatilityfoundation.org/announcing-f...

See the full details in our blog post: volatilityfoundation.org/announcing-f...

See the full details in our blog post: volatilityfoundation.org/announcing-f...
rvasec.com/rvasec-14-sp...

rvasec.com/rvasec-14-sp...
Following FTSCon will be a 4-day Malware & Memory Forensics Training course with Volatility 3.
See the full details here: volatilityfoundation.org/announcing-f...

Following FTSCon will be a 4-day Malware & Memory Forensics Training course with Volatility 3.
See the full details here: volatilityfoundation.org/announcing-f...
www.volexity.com/blog/2025/04... #dfir
www.justice.gov/opa/pr/justi...
#dfir #threatintel

www.justice.gov/opa/pr/justi...
#dfir #threatintel
[1/2]
#dfir #memoryforensics #memoryanalysis

[1/2]
#dfir #memoryforensics #memoryanalysis
#dfir #threatintel #m365security
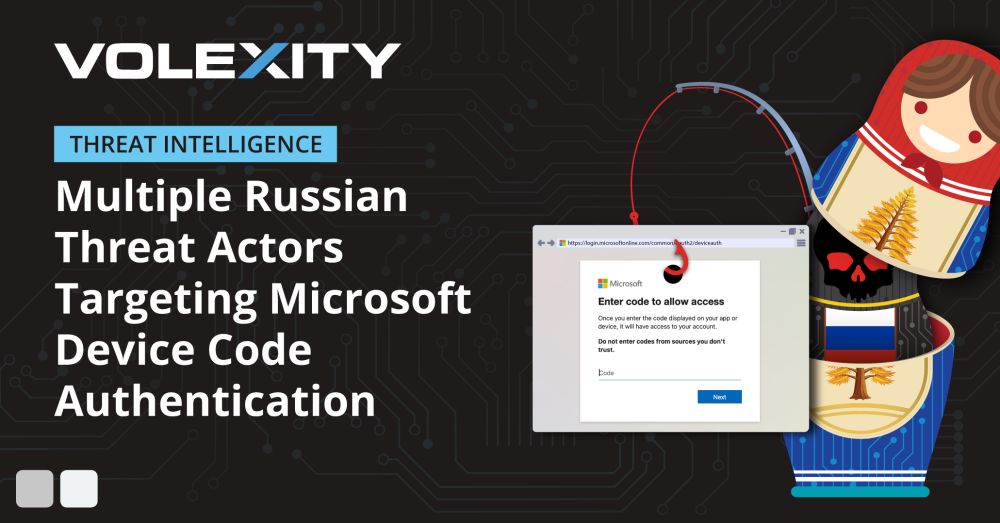
www.ncsc.gov.uk/news/cyber-a...

www.ncsc.gov.uk/news/cyber-a...

www.ncsc.gov.uk/news/cyber-a...
Conference agenda:
wildwesthackinfest.com/wild-west-ha....
#dfir #memoryforensics #Volatility3 @volatilityfoundation.org


Read more here: www.volexity.com/blog/2024/11...


Read more here: www.volexity.com/blog/2024/11...

Read more here: www.volexity.com/blog/2024/11...

