
Amateur Photographer
cloud.google.com/blog/topics/...
cloud.google.com/blog/topics/...
Attending a protest: ssd.eff.org/module/atten...
How to Use Signal: ssd.eff.org/module/how-t...
Security starter pack: ssd.eff.org/playlist/wan...
Attending a protest: ssd.eff.org/module/atten...
How to Use Signal: ssd.eff.org/module/how-t...
Security starter pack: ssd.eff.org/playlist/wan...

The Electronic Frontier Foundation highlights RTB as an unregulated system that significantly undermines user privacy.

The Electronic Frontier Foundation highlights RTB as an unregulated system that significantly undermines user privacy.

Now: Fortinet issues advisory and updates for 9.6/10 critical severity vulnerability, acknowledges active exploitation
See update: www.theregister.com/2025/01/14/m...


- Seen at Space Launch Complex 36
- Work commute mapped
- Stops at Home Depot & family visits near Kansas City logged
🔒 A stark reminder of the privacy risks in location data collection.




- Seen at Space Launch Complex 36
- Work commute mapped
- Stops at Home Depot & family visits near Kansas City logged
🔒 A stark reminder of the privacy risks in location data collection.
They shared 3 samples on a Russian forum, exposing millions of location points across the US, Russia, and Europe.
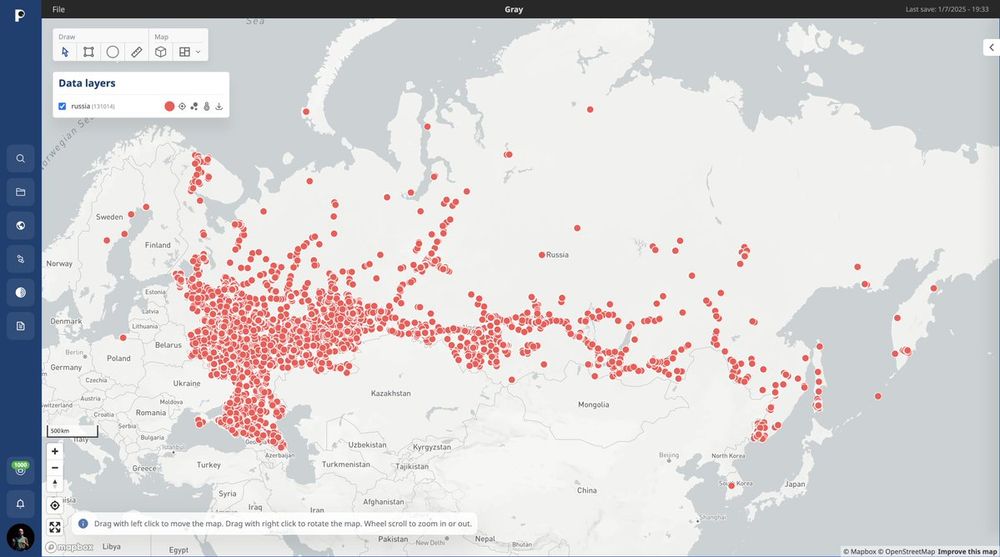
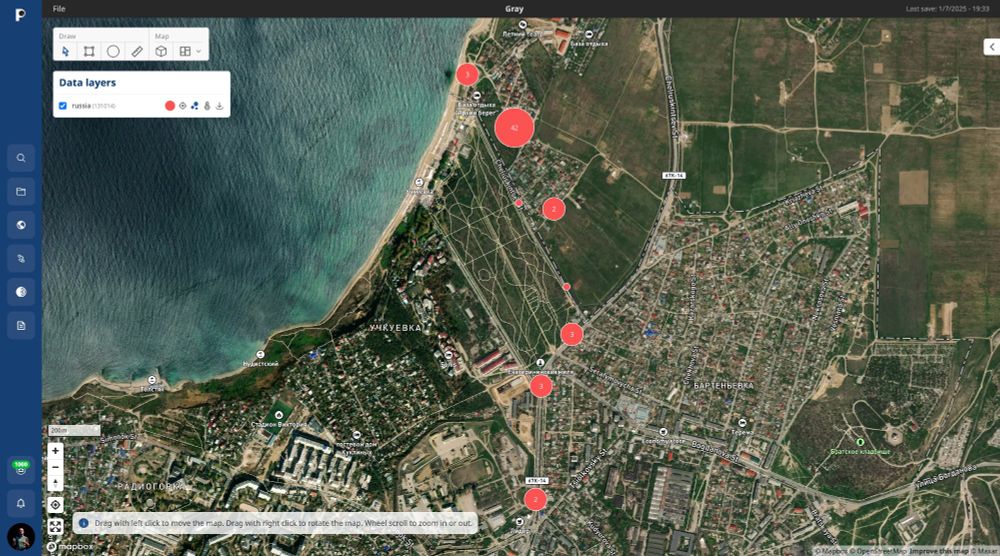
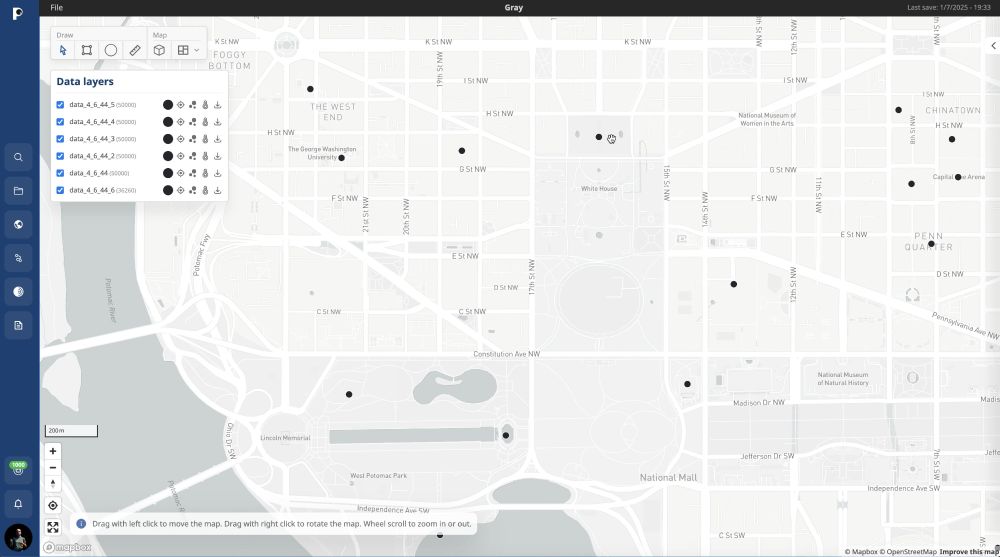
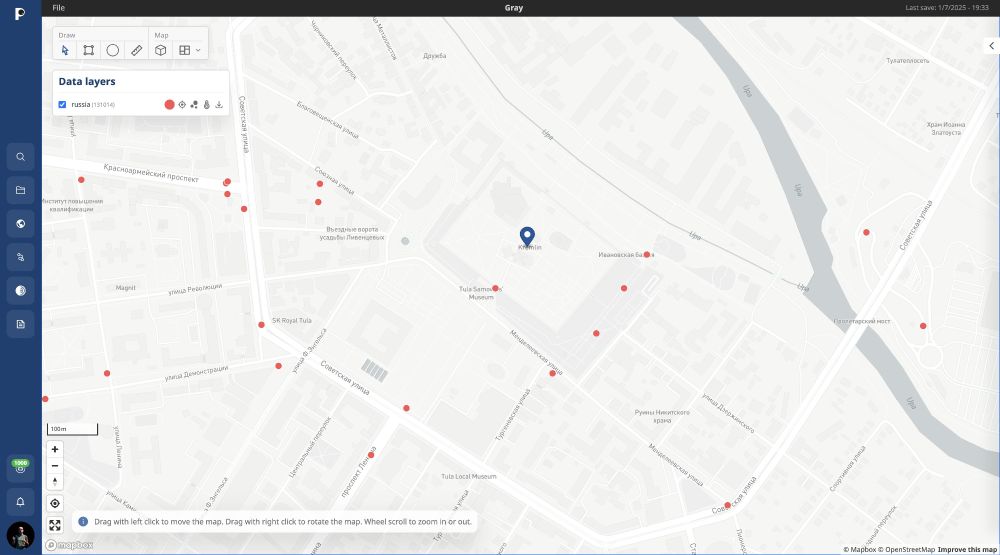
They shared 3 samples on a Russian forum, exposing millions of location points across the US, Russia, and Europe.

