hextree.io. Contact: [email protected]

We've extended the RP2350 side-channel hacking challenge to April 30 - and even better: To make attacks for the challenge easier, we decided to disable the random chaffing and some more mitigations!
www.raspberrypi.com/news/rp2350-...

We've extended the RP2350 side-channel hacking challenge to April 30 - and even better: To make attacks for the challenge easier, we decided to disable the random chaffing and some more mitigations!
www.raspberrypi.com/news/rp2350-...
Time to take them apart 🧵

Time to take them apart 🧵

Hobby: Fix rust issues 👨🏭
😭

Hobby: Fix rust issues 👨🏭
😭
If you have leftover or rare SPI flash-chips that I can have for testing some tooling I’m building I’d be very thankful.
Also if you have devices where you had trouble dumping in-system I’d love to give it a try. I’ll be at Embedded Systems Village :)
If you have leftover or rare SPI flash-chips that I can have for testing some tooling I’m building I’d be very thankful.
Also if you have devices where you had trouble dumping in-system I’d love to give it a try. I’ll be at Embedded Systems Village :)
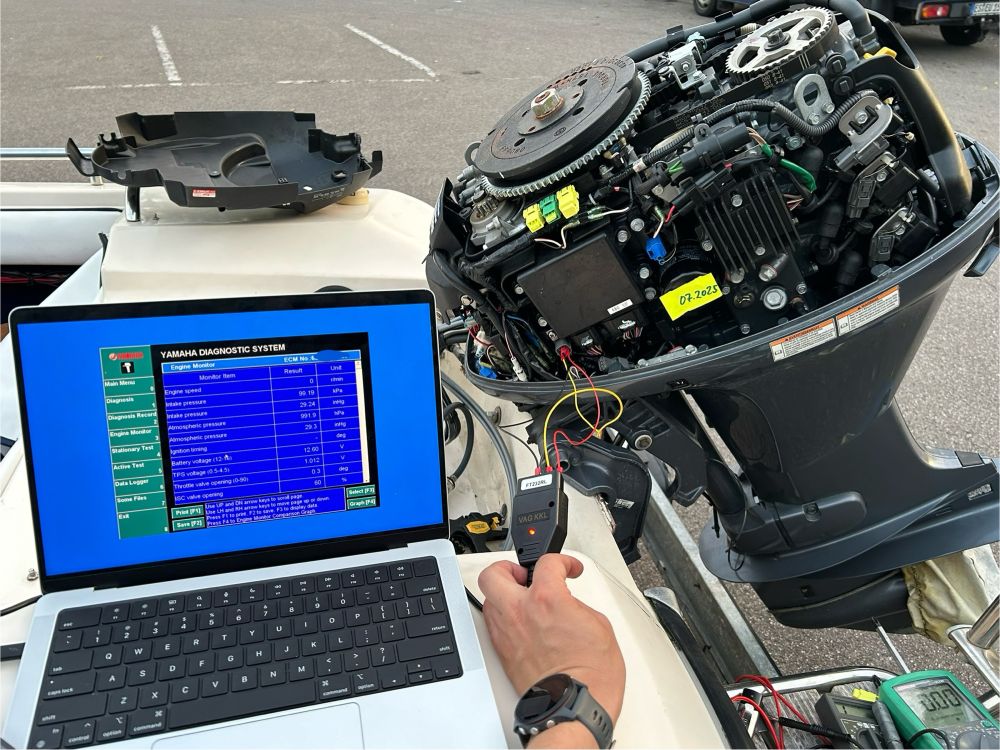
:RECord:WREPlay:FCURrent 2
:WAV:DATA?
...does not seem to work
:RECord:WREPlay:FCURrent 2
:WAV:DATA?
...does not seem to work
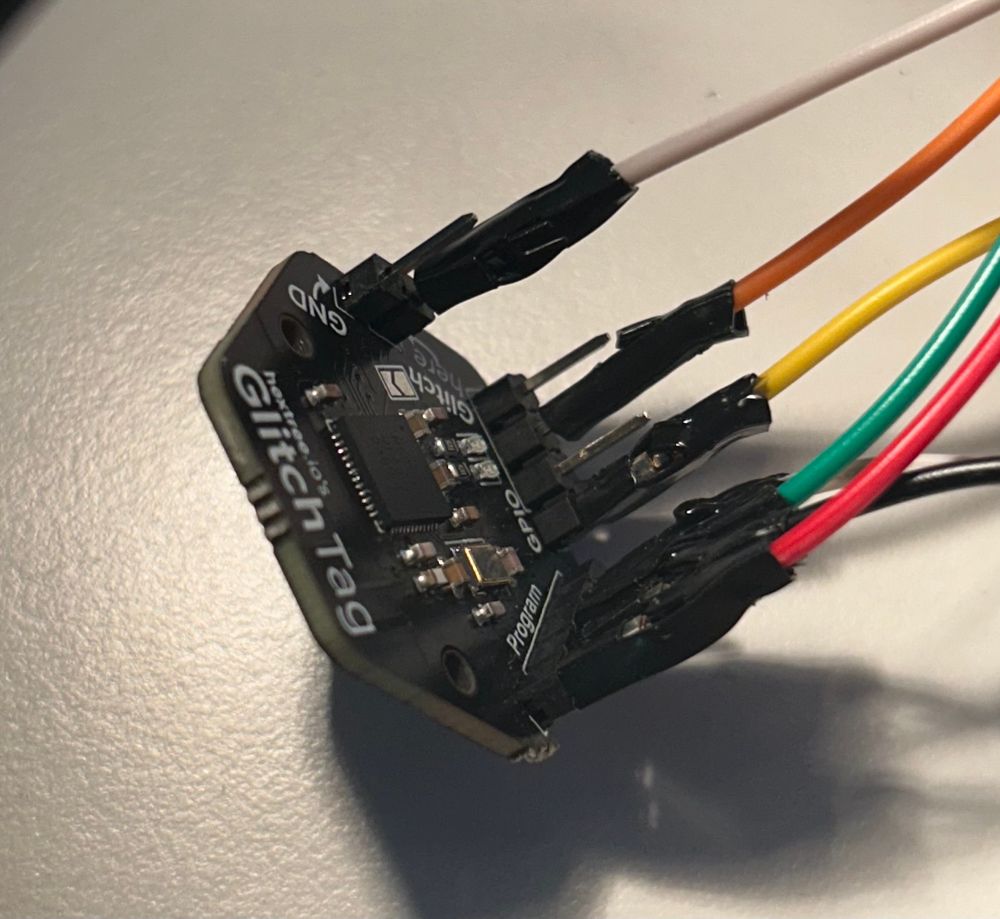
A relay is not opening/closing reliably.
The relay is epoxied into a PCB assembly.
Replacement cost for the 5EUR (being generous here) relay is 400EUR because you can only buy the entire assembly.
A relay is not opening/closing reliably.
The relay is epoxied into a PCB assembly.
Replacement cost for the 5EUR (being generous here) relay is 400EUR because you can only buy the entire assembly.
Pretty sure there’s a market there.
Pretty sure there’s a market there.
It's faster to send something from the UK to Finland, import it there, and then forward it to Germany than trying to import something from the UK to Germany directly.
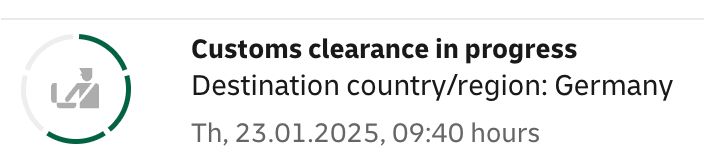
It's faster to send something from the UK to Finland, import it there, and then forward it to Germany than trying to import something from the UK to Germany directly.

It's faster to send something from the UK to Finland, import it there, and then forward it to Germany than trying to import something from the UK to Germany directly.

Absolute legend, thanks for everything you do.
frida.re/news/2025/01...
Absolute legend, thanks for everything you do.
frida.re/news/2025/01...

My fuzzer just before bedtime:
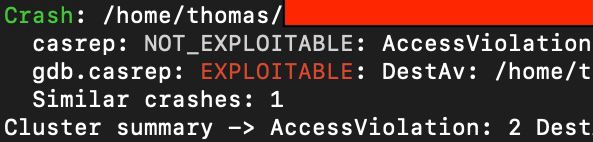
My fuzzer just before bedtime:


