All of them were fixed in the iOS 26.1 (and equivalent) update last month. Definitely some cool bugs in there!
All of them were fixed in the iOS 26.1 (and equivalent) update last month. Definitely some cool bugs in there!
Fantastic conference as usual, big thanks to the PoC Crew!
Fantastic conference as usual, big thanks to the PoC Crew!
Technical details will be available soon at issuetracker.google.com/issues?q=com...
Technical details will be available soon at issuetracker.google.com/issues?q=com...

It explores the heap to find interesting objects and corrupts them in a deterministic way using V8's memory corruption API. Happy fuzzing!

It explores the heap to find interesting objects and corrupts them in a deterministic way using V8's memory corruption API. Happy fuzzing!
Great opportunity to work on some really hard and interesting problems in the security space!
Great opportunity to work on some really hard and interesting problems in the security space!
Some cool things to note though:
- the bug was mitigated via finch kill switch a day after the report from TAG
- we also fixed the V8 Sandbox bypass within 7 days even though it's not yet considered a security boundary

Some cool things to note though:
- the bug was mitigated via finch kill switch a day after the report from TAG
- we also fixed the V8 Sandbox bypass within 7 days even though it's not yet considered a security boundary
Go check it out at https://github.com/googleprojectzero/fuzzilli.
While we still have a way to go in improving it, we think it shows a promising approach!
Go check it out at https://github.com/googleprojectzero/fuzzilli.
While we still have a way to go in improving it, we think it shows a promising approach!
* No longer limited to d8
* Rewards for controlled writes increased to $20k
* Any memory corruption outside the sandbox is now in scope
bughunters.google.com/about/rules/...
Happy hacking!

* No longer limited to d8
* Rewards for controlled writes increased to $20k
* Any memory corruption outside the sandbox is now in scope
bughunters.google.com/about/rules/...
Happy hacking!

The V8 Heap Sandbox: saelo.github.io/presentation...
Fantastic conference, as usual! :)
The V8 Heap Sandbox: saelo.github.io/presentation...
Fantastic conference, as usual! :)
* Now included in the Chrome VRP: g.co/chrome/vrp/#...
* Motivation & goals discussed in a new technical blog post: v8.dev/blog/sandbox
If there is ever a Sandbox "beta" release, this is it!
* Now included in the Chrome VRP: g.co/chrome/vrp/#...
* Motivation & goals discussed in a new technical blog post: v8.dev/blog/sandbox
If there is ever a Sandbox "beta" release, this is it!
This discusses how a hardware-based sandbox instead of the currently purely software-based one might look like in a somewhat distant future (if at all)
This discusses how a hardware-based sandbox instead of the currently purely software-based one might look like in a somewhat distant future (if at all)
More results linked from chromium-review.googlesource.com/c/v8/v8/+/52...
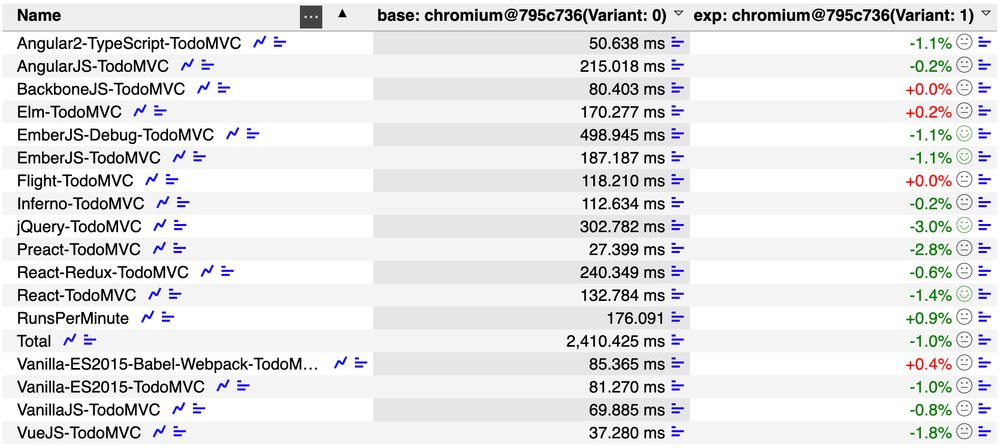
More results linked from chromium-review.googlesource.com/c/v8/v8/+/52...

This should be one of the last pieces of infrastructure required for the sandbox.
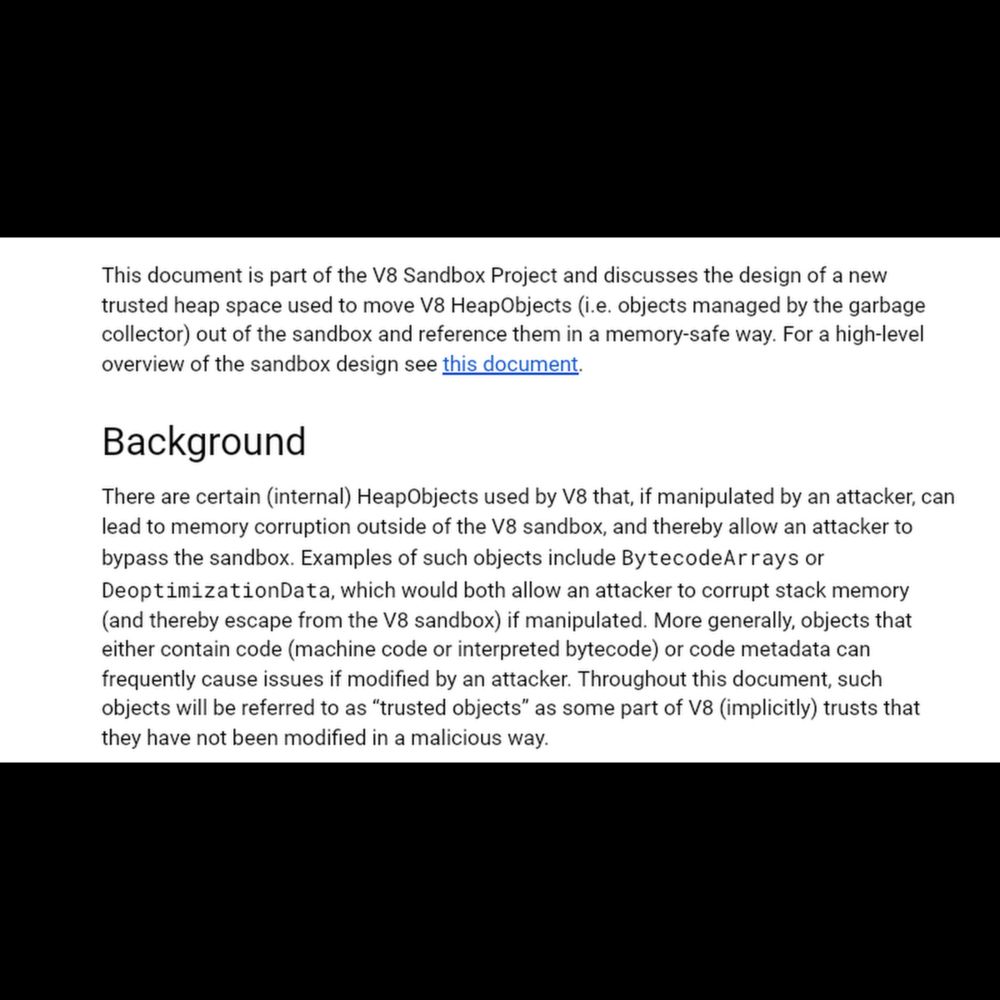
This should be one of the last pieces of infrastructure required for the sandbox.

