

Since folks are increasingly talking about software supply chain risks to national security, here's a collection of my work on the subject.
Going back to 2022.
'ASX's strategy lacks the vision necessary for the critical role it plays
'ASX's strategy lacks the vision necessary for the critical role it plays
'He said this meant installers had every incentive to sell consumers the biggest possible batteries that were eligible for the scheme.
'He said this meant installers had every incentive to sell consumers the biggest possible batteries that were eligible for the scheme.
Not surprising, but again, sheesh.
therecord.media/germany-summ...

Not surprising, but again, sheesh.
therecord.media/germany-summ...
Screenshot 2: www.asio.gov.au/asio.gov.au/...
I fear that, since 7/10, Global North security risk landscapes have shifted back, in many respects, to the 1970s.
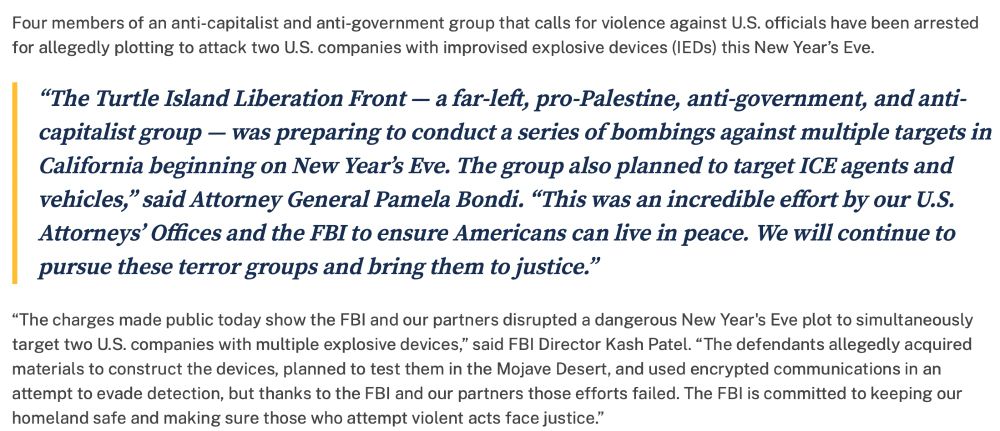

Screenshot 2: www.asio.gov.au/asio.gov.au/...
I fear that, since 7/10, Global North security risk landscapes have shifted back, in many respects, to the 1970s.
'Following reports the Government was implementing a “blanket 5 per cent reduction in discretionary spending” across Commonwealth agencies, the AFPA expressed its concerns to Senator Katy Gallagher in her capacity as Public Service Minister.
'Following reports the Government was implementing a “blanket 5 per cent reduction in discretionary spending” across Commonwealth agencies, the AFPA expressed its concerns to Senator Katy Gallagher in her capacity as Public Service Minister.
Some excerpts attached: www.homeaffairs.gov.au/help-and-sup...



Some excerpts attached: www.homeaffairs.gov.au/help-and-sup...
'... seeking to replace includes tools for incident response and recovery, network orchestration and knowledge sharing among teams ..
'... seeking to replace includes tools for incident response and recovery, network orchestration and knowledge sharing among teams ..
'... up to 73% of the total daily trading volume in the relevant shares, creating a false or misleading appearance of active trading ...
'... up to 73% of the total daily trading volume in the relevant shares, creating a false or misleading appearance of active trading ...
But then there's this bit at the end of the statement which made me furrow my brow:
But then there's this bit at the end of the statement which made me furrow my brow:
www.breakingnews.ie/ireland/hse-...

www.breakingnews.ie/ireland/hse-...
www.koreatimes.co.kr/business/com...

www.koreatimes.co.kr/business/com...
archive.today/bFOgc
archive.today/bFOgc
For the victims, families and first responders.
This is horrible.
Please pray. Hari Om.
For the victims, families and first responders.
This is horrible.
Please pray. Hari Om.
'When there is a loss of satellite connectivity, the VTS interprets it as a potential theft attempt and immobilises the engine'.
'When there is a loss of satellite connectivity, the VTS interprets it as a potential theft attempt and immobilises the engine'.

