
February 26, 2025 at 7:45 AM
I made an ImHex pattern file for the ftab file format used for Apple C1 firmware and Apple accessories
gist.github.com/matteyeux/d1...
gist.github.com/matteyeux/d1...

February 21, 2025 at 6:41 AM
I made an ImHex pattern file for the ftab file format used for Apple C1 firmware and Apple accessories
gist.github.com/matteyeux/d1...
gist.github.com/matteyeux/d1...
Today is December 1st, and it's your yearly reminder that Stefan Esser, made a "macOS and iOS Security Internals" Advent calendar playlist on Youtube
www.youtube.com/playlist?lis...
www.youtube.com/playlist?lis...

macOS and iOS Security Internals Advent Calendar 2022 - YouTube
www.youtube.com
December 1, 2024 at 9:51 AM
Today is December 1st, and it's your yearly reminder that Stefan Esser, made a "macOS and iOS Security Internals" Advent calendar playlist on Youtube
www.youtube.com/playlist?lis...
www.youtube.com/playlist?lis...
Next gen Apple Silicon (A19/M5) should have MTE
Internally there is a boot-arg to disable it : -disable_mte
Internally there is a boot-arg to disable it : -disable_mte
November 25, 2024 at 7:30 AM
Next gen Apple Silicon (A19/M5) should have MTE
Internally there is a boot-arg to disable it : -disable_mte
Internally there is a boot-arg to disable it : -disable_mte
Is it common to see tests added by SEAR Red Team in XNU source code (rel/xnu-11215)

November 24, 2024 at 4:45 PM
Is it common to see tests added by SEAR Red Team in XNU source code (rel/xnu-11215)
Reposted by matteyeux
how do you design a privacy-preserving ML inference system?
Peeking Inside Apple's Private Cloud Compute, with art by @restlessrice.bsky.social
research.meekolab.com/peeking-insi...
Peeking Inside Apple's Private Cloud Compute, with art by @restlessrice.bsky.social
research.meekolab.com/peeking-insi...

Peeking Inside Apple's Private Cloud Compute
An unprecedented look into Apple Intelligence's internal server tools and security features
research.meekolab.com
November 21, 2024 at 4:26 PM
how do you design a privacy-preserving ML inference system?
Peeking Inside Apple's Private Cloud Compute, with art by @restlessrice.bsky.social
research.meekolab.com/peeking-insi...
Peeking Inside Apple's Private Cloud Compute, with art by @restlessrice.bsky.social
research.meekolab.com/peeking-insi...
Reposted by matteyeux
How does the new iOS inactivity reboot work? What does it protect from?
I reverse engineered the kernel extension and the secure enclave processor, where this feature is implemented.
naehrdine.blogspot.com/2024/11/reve...
I reverse engineered the kernel extension and the secure enclave processor, where this feature is implemented.
naehrdine.blogspot.com/2024/11/reve...

Reverse Engineering iOS 18 Inactivity Reboot
Wireless and firmware hacking, PhD life, Technology
naehrdine.blogspot.com
November 17, 2024 at 9:42 PM
How does the new iOS inactivity reboot work? What does it protect from?
I reverse engineered the kernel extension and the secure enclave processor, where this feature is implemented.
naehrdine.blogspot.com/2024/11/reve...
I reverse engineered the kernel extension and the secure enclave processor, where this feature is implemented.
naehrdine.blogspot.com/2024/11/reve...
ARMv7m core, started when the sep-firmware is loaded.
It's firmware can be dumped but you need a special device...
It's firmware can be dumped but you need a special device...
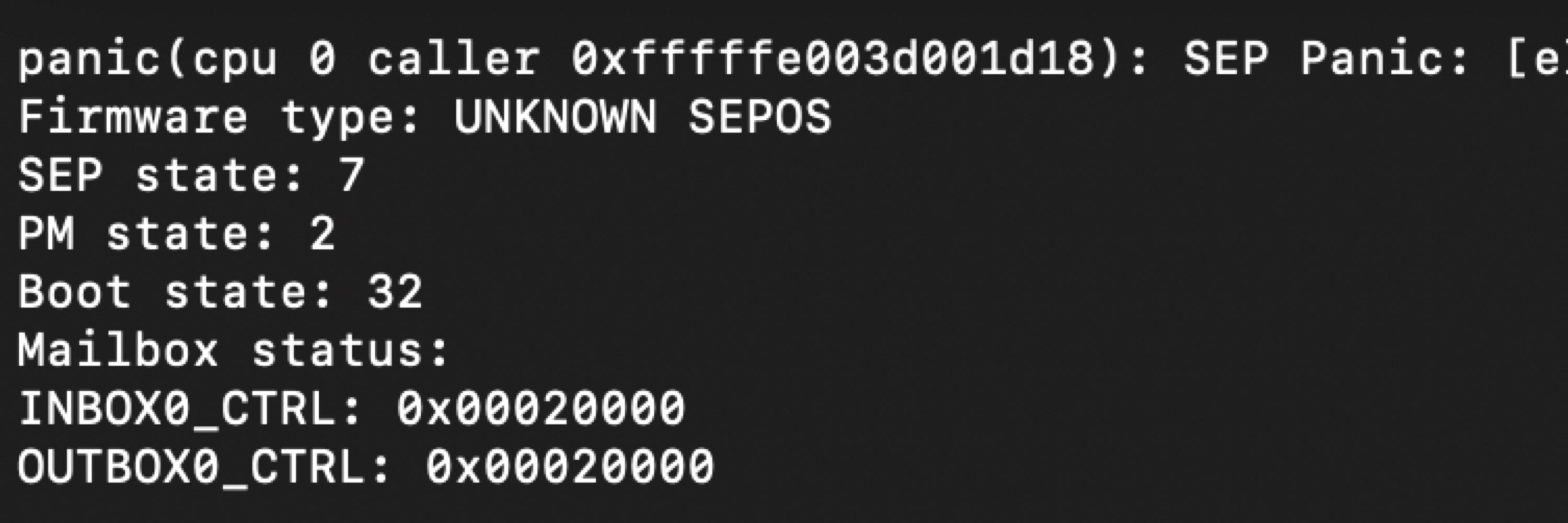
I have not seen yet any research the Secure Enclave Boot Monitor

October 20, 2024 at 5:04 PM
ARMv7m core, started when the sep-firmware is loaded.
It's firmware can be dumped but you need a special device...
It's firmware can be dumped but you need a special device...
I have not seen yet any research the Secure Enclave Boot Monitor

October 20, 2024 at 5:01 PM
I have not seen yet any research the Secure Enclave Boot Monitor
Reposted by matteyeux
I'm watching some folks reverse engineer the xz backdoor, sharing some *preliminary* analysis with permission.
The hooked RSA_public_decrypt verifies a signature on the server's host key by a fixed Ed448 key, and then passes a payload to system().
It's RCE, not auth bypass, and gated/unreplayable.
The hooked RSA_public_decrypt verifies a signature on the server's host key by a fixed Ed448 key, and then passes a payload to system().
It's RCE, not auth bypass, and gated/unreplayable.
This might be the best executed supply chain attack we've seen described in the open, and it's a nightmare scenario: malicious, competent, authorized upstream in a widely used library.
Looks like this got caught by chance. Wonder how long it would have taken otherwise.
Looks like this got caught by chance. Wonder how long it would have taken otherwise.
Woah. Backdoor in liblzma targeting ssh servers.
www.openwall.com/lists/oss-se...
It has everything: malicious upstream, masterful obfuscation, detection due to performance degradation, inclusion in OpenSSH via distro patches for systemd support…
Now I’m curious what it does in RSA_public_decrypt
www.openwall.com/lists/oss-se...
It has everything: malicious upstream, masterful obfuscation, detection due to performance degradation, inclusion in OpenSSH via distro patches for systemd support…
Now I’m curious what it does in RSA_public_decrypt
March 30, 2024 at 5:13 PM
I'm watching some folks reverse engineer the xz backdoor, sharing some *preliminary* analysis with permission.
The hooked RSA_public_decrypt verifies a signature on the server's host key by a fixed Ed448 key, and then passes a payload to system().
It's RCE, not auth bypass, and gated/unreplayable.
The hooked RSA_public_decrypt verifies a signature on the server's host key by a fixed Ed448 key, and then passes a payload to system().
It's RCE, not auth bypass, and gated/unreplayable.
One of the Limefix payload decrypted

December 23, 2023 at 9:56 AM
One of the Limefix payload decrypted
Old plugin I made for Binary Ninja to have the function doc of a native Windows function

October 29, 2023 at 2:00 PM
Old plugin I made for Binary Ninja to have the function doc of a native Windows function
Swift in M1 Secure Enclave

October 21, 2023 at 11:01 AM
Swift in M1 Secure Enclave
The first Apple Security Research Device

October 18, 2023 at 11:17 AM
The first Apple Security Research Device
Linux ARM64 Kernel debugging in Binary Ninja. The target runs in qemu.

October 13, 2023 at 6:43 AM
Linux ARM64 Kernel debugging in Binary Ninja. The target runs in qemu.
iPhone 15 Pro serial output

September 29, 2023 at 7:13 AM
iPhone 15 Pro serial output
Some info about DFU mode on iPhone 15 Pro :
DFU with buttons goes into "Port DFU" (USB-C Controller DFU)
If you use macvdmtool you can boot in DFU "Debug USB" then get OG USB string with a kis compatible tool like irecovery
x.com/ghidraninja/...
DFU with buttons goes into "Port DFU" (USB-C Controller DFU)
If you use macvdmtool you can boot in DFU "Debug USB" then get OG USB string with a kis compatible tool like irecovery
x.com/ghidraninja/...

September 24, 2023 at 12:22 PM
Some info about DFU mode on iPhone 15 Pro :
DFU with buttons goes into "Port DFU" (USB-C Controller DFU)
If you use macvdmtool you can boot in DFU "Debug USB" then get OG USB string with a kis compatible tool like irecovery
x.com/ghidraninja/...
DFU with buttons goes into "Port DFU" (USB-C Controller DFU)
If you use macvdmtool you can boot in DFU "Debug USB" then get OG USB string with a kis compatible tool like irecovery
x.com/ghidraninja/...
3 bugs, including a codesign bypass 😵💫
support.apple.com/en-us/HT213926
support.apple.com/en-us/HT213926
September 21, 2023 at 6:26 PM
3 bugs, including a codesign bypass 😵💫
support.apple.com/en-us/HT213926
support.apple.com/en-us/HT213926

