(ht @feikeh.bsky.social)
www.trendmicro.com/en_us/resear...

(ht @feikeh.bsky.social)
www.trendmicro.com/en_us/resear...


@citizenlab.ca
leveraging vulnerabilities in applications embedding old versions of Chromium trendmicro.com/en_us/resear...
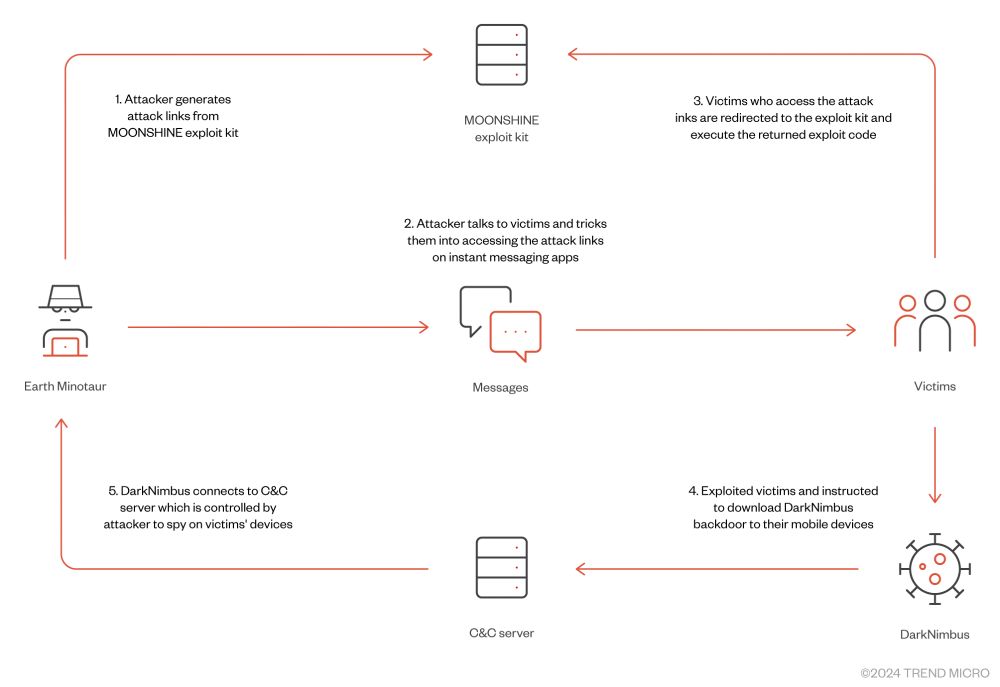
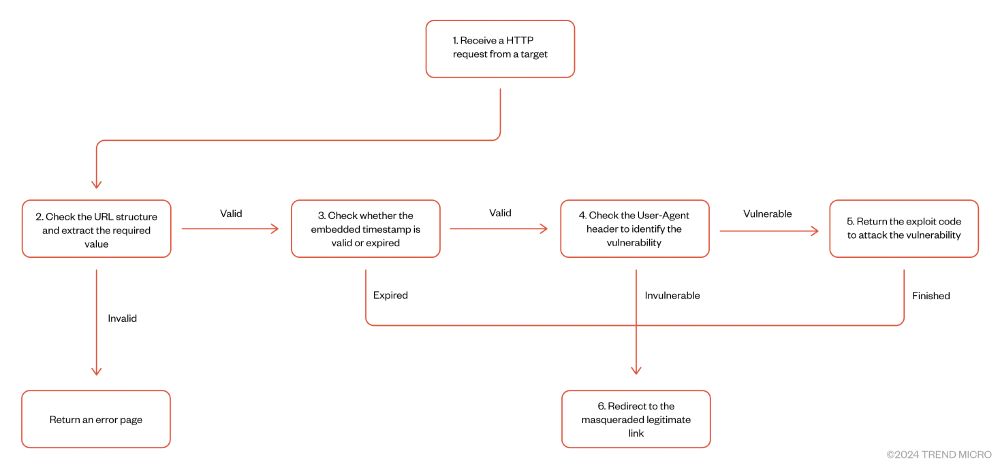
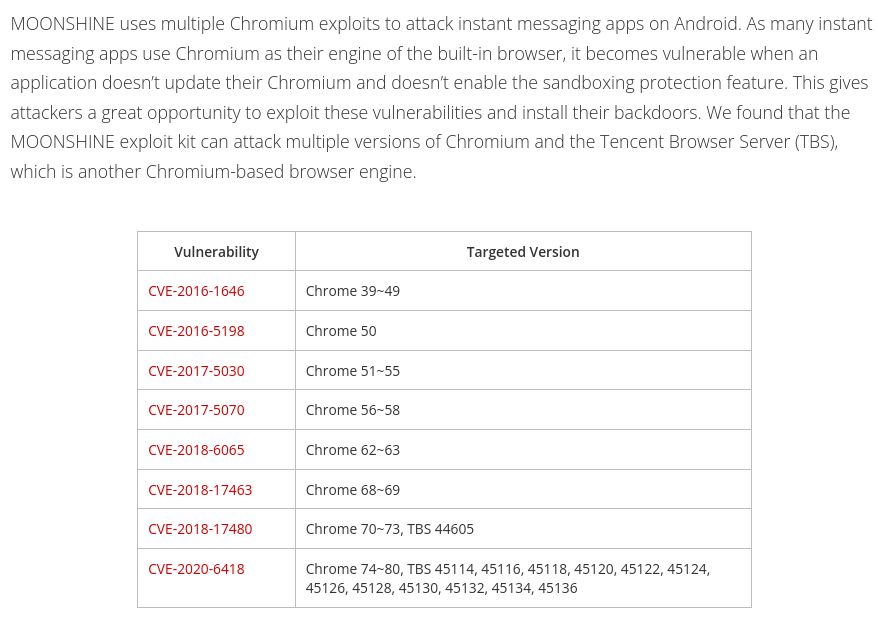
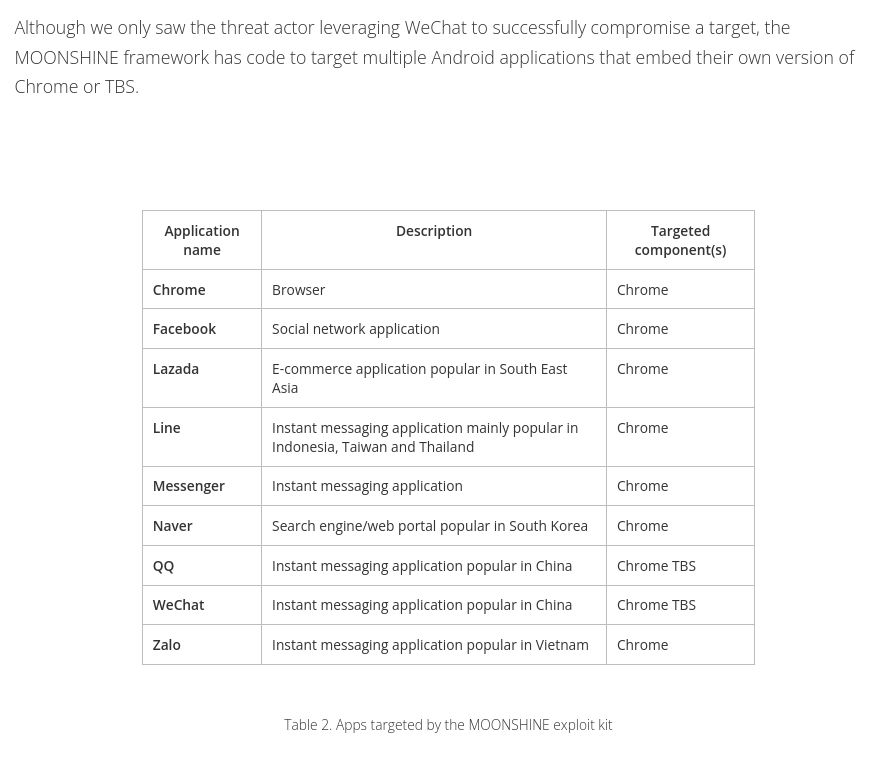
@citizenlab.ca
leveraging vulnerabilities in applications embedding old versions of Chromium trendmicro.com/en_us/resear...