ethicalhack3r
@ethicalhack3r.bsky.social
200 followers
140 following
130 posts
Founder of Damn Vulnerable Web App (DVWA)
Founder of WPScan (acquired by Automattic)
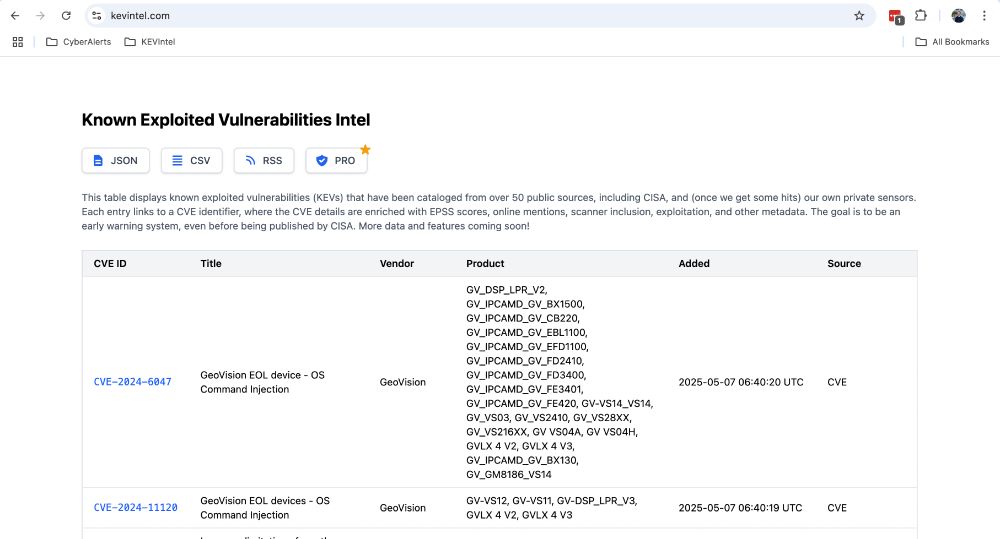
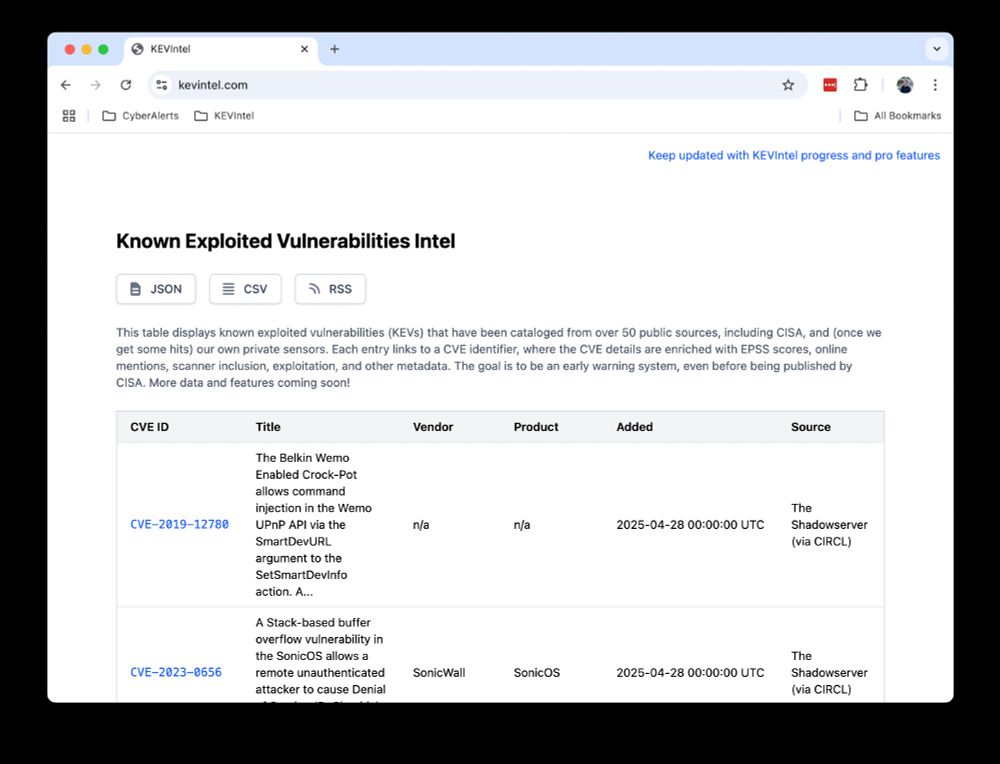
Check out my new project! https://kevintel.com
Posts
Media
Videos
Starter Packs
Reposted by ethicalhack3r
CyberAlerts
@cyberalerts.bsky.social
· Jun 11
ethicalhack3r
@ethicalhack3r.bsky.social
· May 25
Reposted by ethicalhack3r
Reposted by ethicalhack3r
ethicalhack3r
@ethicalhack3r.bsky.social
· Apr 28
Reposted by ethicalhack3r
CyberAlerts
@cyberalerts.bsky.social
· Apr 26
ethicalhack3r
@ethicalhack3r.bsky.social
· Apr 25
ethicalhack3r
@ethicalhack3r.bsky.social
· Apr 25
ethicalhack3r
@ethicalhack3r.bsky.social
· Apr 24
ethicalhack3r
@ethicalhack3r.bsky.social
· Apr 24
ethicalhack3r
@ethicalhack3r.bsky.social
· Apr 24