
I do Active Directory stuff for a living. Security research to be more specific. One of my favorite niche AD topics is AdminSDHolder. It's even my vanity domain.
I wrote a 159 pg book about AdminSDHolder. I'm kinda proud of it.
specterops.io/resources/ad...

I do Active Directory stuff for a living. Security research to be more specific. One of my favorite niche AD topics is AdminSDHolder. It's even my vanity domain.
I wrote a 159 pg book about AdminSDHolder. I'm kinda proud of it.
specterops.io/resources/ad...
Meet ShareHound, an OpenGraph collector for BloodHound CE & Enterprise that reveals share-level attack paths at scale.
@podalirius.bsky.social unpacks all the details in our latest blog post. ghst.ly/4ogiBqt

Meet ShareHound, an OpenGraph collector for BloodHound CE & Enterprise that reveals share-level attack paths at scale.
@podalirius.bsky.social unpacks all the details in our latest blog post. ghst.ly/4ogiBqt
@runzero.com with attack path visualization.
Love seeing the community take BloodHound in new directions!

@runzero.com with attack path visualization.
Love seeing the community take BloodHound in new directions!
Valdemar Carøe just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled.
Read for more: ghst.ly/4qtl2rm

Valdemar Carøe just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled.
Read for more: ghst.ly/4qtl2rm

Thank you again to the organizers and everyone else who helps put on the conference. I look forward to coming back!
youtu.be/G2CfMWXLU1U?...

Thank you again to the organizers and everyone else who helps put on the conference. I look forward to coming back!
youtu.be/G2CfMWXLU1U?...
@1cemoon.bsky.social documents NAA flows and BroCI—filling a gap for research on Microsoft identity protocols. ghst.ly/3Jdhp7Z


There might be bugs with the new search - let me know if you see any strangeness. Happy hunting :-)

There might be bugs with the new search - let me know if you see any strangeness. Happy hunting :-)
Ever wondered about those obscure AD special identity groups that quietly grant permissions to every principal in your environment?
With BloodHound, you can uncover compromising permissions tied to these groups.
🧵: 1/2

Ever wondered about those obscure AD special identity groups that quietly grant permissions to every principal in your environment?
With BloodHound, you can uncover compromising permissions tied to these groups.
🧵: 1/2
@sadprocessor.bsky.social dives into the BloodHound OpenGraph functionality & demonstrates the new PowerShell cmdlets added to the BloodHound Operator module to work with the OpenGraph feature. ghst.ly/4peTTrB

@sadprocessor.bsky.social dives into the BloodHound OpenGraph functionality & demonstrates the new PowerShell cmdlets added to the BloodHound Operator module to work with the OpenGraph feature. ghst.ly/4peTTrB
This is how I used to design BloodHound's entity panels. Just a text editor to list out what I as a red-teamer wanted to see, with the corresponding (then new) cypher queries listed as well.
Simple, VERY low-fidelity mockup, but really helped during the design phase.

This is how I used to design BloodHound's entity panels. Just a text editor to list out what I as a red-teamer wanted to see, with the corresponding (then new) cypher queries listed as well.
Simple, VERY low-fidelity mockup, but really helped during the design phase.
✅ - Unisex adult/child and ladies sizes available
✅ - Cool design :)
✅ - ALL profits go to charity
This time we are supporting Hope for HIE, which supports families suffering the effects of hypoxic ischemic encephalopathy
Get your shirt here: ghst.ly/bh8-tshirt

✅ - Unisex adult/child and ladies sizes available
✅ - Cool design :)
✅ - ALL profits go to charity
This time we are supporting Hope for HIE, which supports families suffering the effects of hypoxic ischemic encephalopathy
Get your shirt here: ghst.ly/bh8-tshirt

Meet DeepPass2, our new secret scanning tool that goes beyond structured tokens to catch those tricky free-form passwords too. Read Neeraj Gupta's blog post for more. ghst.ly/40HLNNA
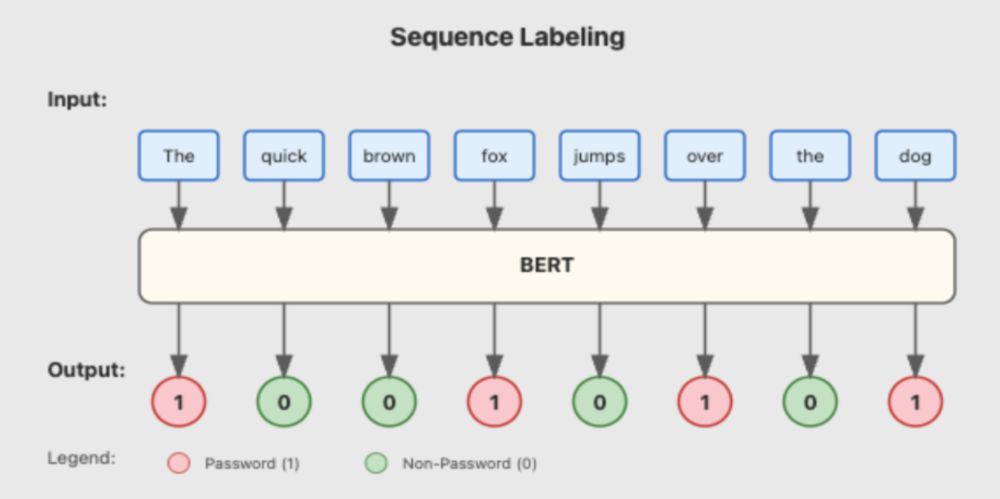
Meet DeepPass2, our new secret scanning tool that goes beyond structured tokens to catch those tricky free-form passwords too. Read Neeraj Gupta's blog post for more. ghst.ly/40HLNNA
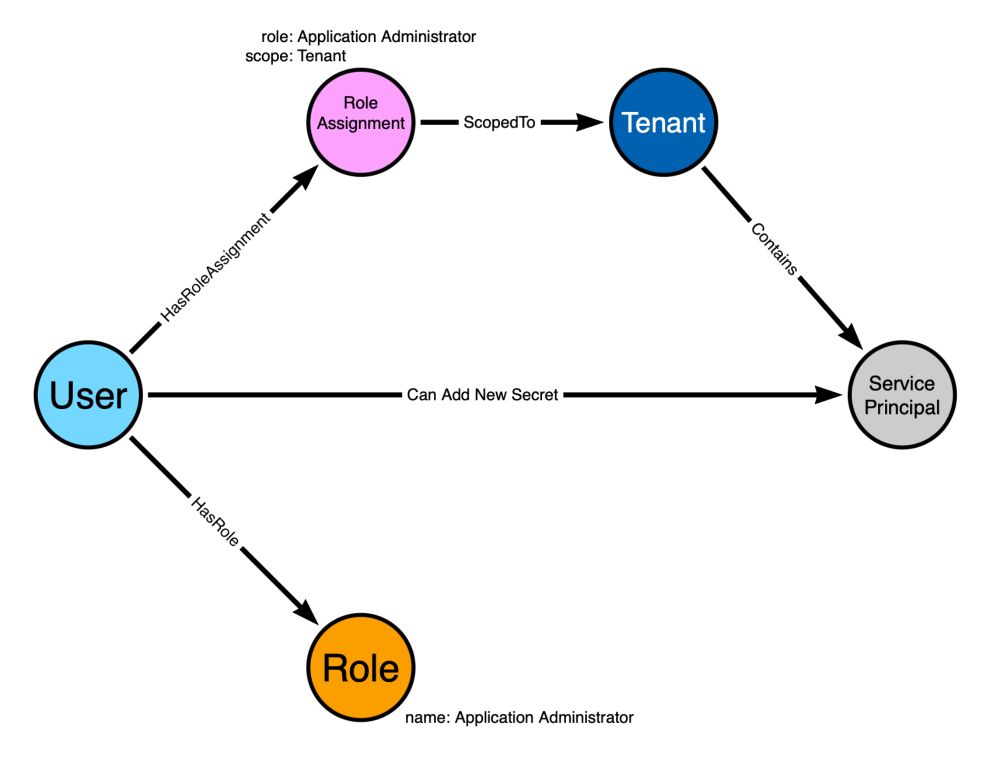
@hotnops.bsky.social explores cross-domain compromise tradecraft within the same tenant.
Read more: ghst.ly/3ISMGN9

@hotnops.bsky.social explores cross-domain compromise tradecraft within the same tenant.
Read more: ghst.ly/3ISMGN9
This update introduces BloodHound OpenGraph, revolutionizing Identity Attack Path Management by exposing attack paths throughout your entire tech stack, not just AD/Entra ID.
Read more from Justin Kohler: ghst.ly/bloodhoundv8
🧵: 1/7
This update introduces BloodHound OpenGraph, revolutionizing Identity Attack Path Management by exposing attack paths throughout your entire tech stack, not just AD/Entra ID.
Read more from Justin Kohler: ghst.ly/bloodhoundv8
🧵: 1/7
Read more: ghst.ly/445tQKL
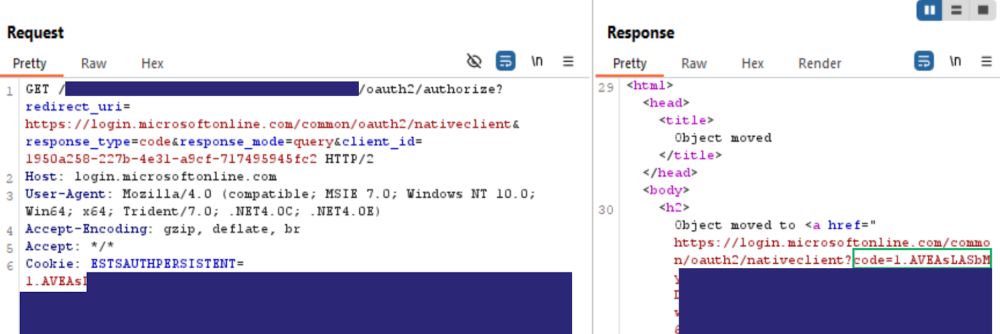
Read more: ghst.ly/445tQKL
First dives into how we're improving the way BloodHound models attack paths through AD trusts: specterops.io/blog/2025/06...
Second covers an attack technique I came across while exploring AD trust abuse: specterops.io/blog/2025/06...
Hope you enjoy the read 🥳
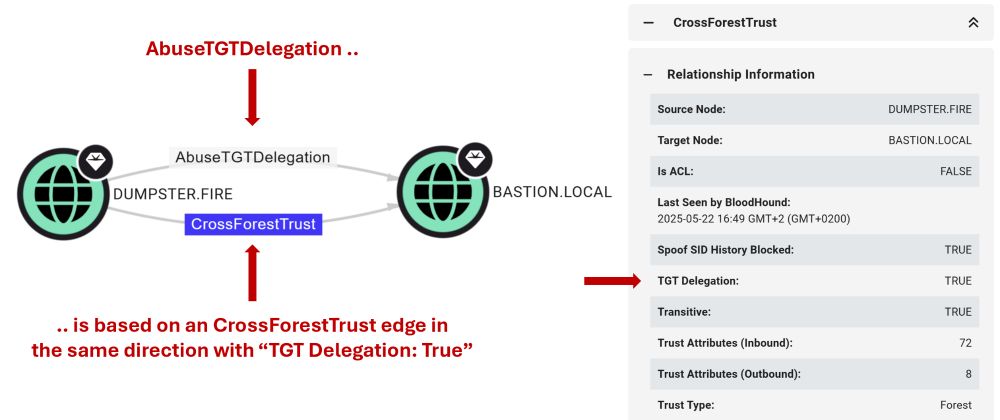
First dives into how we're improving the way BloodHound models attack paths through AD trusts: specterops.io/blog/2025/06...
Second covers an attack technique I came across while exploring AD trust abuse: specterops.io/blog/2025/06...
Hope you enjoy the read 🥳
If you can’t make it, talks are streamed at: www.youtube.com/@fwdcloudsec

If you can’t make it, talks are streamed at: www.youtube.com/@fwdcloudsec
posts.specterops.io/update-dumpi...

posts.specterops.io/update-dumpi...

