#CyberSecurity #CyberAI #OpenSource #CTF #BugBounty
#CyberSecurity #CyberAI #OpenSource #CTF #BugBounty
What is your word for 2025?
#cloud #cloudsecurity #cloudai #cyberai
What is your word for 2025?
#cloud #cloudsecurity #cloudai #cyberai
A: AI Red Teaming is a proactive approach designed to uncover vulnerabilities in AI models, data pipelines, and deployment environments—areas that malicious actors could potentially exploit
v/ AppSOC
#cloud #cloudsecurity #cloudai #cyberai
A: AI Red Teaming is a proactive approach designed to uncover vulnerabilities in AI models, data pipelines, and deployment environments—areas that malicious actors could potentially exploit
v/ AppSOC
#cloud #cloudsecurity #cloudai #cyberai

A: Lateral movement specifically focuses on the progression and exploration within a compromised network.
v/@darktrace.bsky.social
#cloud #cloudsecurity #cloudai #cyberai
A: Lateral movement specifically focuses on the progression and exploration within a compromised network.
v/@darktrace.bsky.social
#cloud #cloudsecurity #cloudai #cyberai
Dropping the cover off the inaugural podcast "CyberAI with Alan Silberberg" in a few days...
stay tuned for more. Will be on Spotify + YouTube to start. #cyberaiwithalansilberberg #cyberai #newpodcast
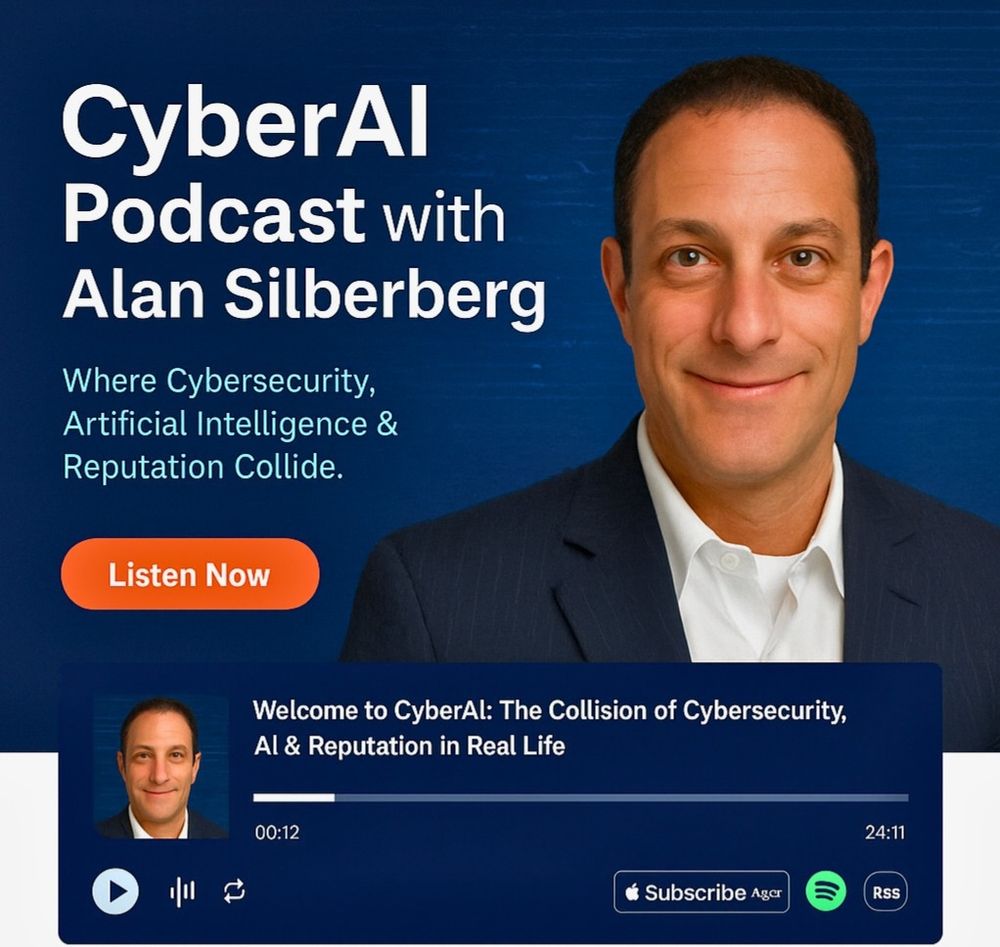
Dropping the cover off the inaugural podcast "CyberAI with Alan Silberberg" in a few days...
stay tuned for more. Will be on Spotify + YouTube to start. #cyberaiwithalansilberberg #cyberai #newpodcast

A: Confabulation on the part of a Large Language Model (LLM) is the generation of output that is not based on real-world input or information
v/@owasp.bsky.social
#cloud #cloudsecurity #cloudai #cyberai #ai
A: Confabulation on the part of a Large Language Model (LLM) is the generation of output that is not based on real-world input or information
v/@owasp.bsky.social
#cloud #cloudsecurity #cloudai #cyberai #ai
So, while apparently NOT being OpenVPN'd in (I was), I got Cyber AI to brute force successfully
1st attempt vague brief, to test, no joy. 2nd attempt, short robust instruction set, BINGO🥳
#CyberSecurity #CyberAI #BruteForce

So, while apparently NOT being OpenVPN'd in (I was), I got Cyber AI to brute force successfully
1st attempt vague brief, to test, no joy. 2nd attempt, short robust instruction set, BINGO🥳
#CyberSecurity #CyberAI #BruteForce
CSET is currently seeking applications for:
1️⃣ A Senior or Research Fellow to lead our Compete Line of Research.
2️⃣ A Cyber AI Research Fellow to support our CyberAI Project.
Learn about each role and apply by November 13! cset.georgetown.edu/careers/

CSET is currently seeking applications for:
1️⃣ A Senior or Research Fellow to lead our Compete Line of Research.
2️⃣ A Cyber AI Research Fellow to support our CyberAI Project.
Learn about each role and apply by November 13! cset.georgetown.edu/careers/
https://dasgeld.co/posts/3988B859-E80B-44C1-B79D-66C45CC1D0CE
https://dasgeld.co/posts/3988B859-E80B-44C1-B79D-66C45CC1D0CE
A: To restrict access to LLMs, implement access controls like (RBAC), multi-factor authentication (MFA), and user authentication systems, limiting who can interact with LLM
v/ Exabeam.bsky.social
#aisecurity #cloudai #cyberai
A: To restrict access to LLMs, implement access controls like (RBAC), multi-factor authentication (MFA), and user authentication systems, limiting who can interact with LLM
v/ Exabeam.bsky.social
#aisecurity #cloudai #cyberai
A: The time between when an attacker breaches a system and when they are detected
v/ @plurilock.bsky.social
Cc: efeatherston.bsky.social
#cloud #cloudsecurity #cloudai #cyberai
A: The time between when an attacker breaches a system and when they are detected
v/ @plurilock.bsky.social
Cc: efeatherston.bsky.social
#cloud #cloudsecurity #cloudai #cyberai
CSET’s CyberAI project is currently seeking candidates to explore topics at the intersection of AI and cyber as a Research Fellow.
Learn more about the position and apply by Nov. 13! cset.georgetown.edu/job/research...

CSET’s CyberAI project is currently seeking candidates to explore topics at the intersection of AI and cyber as a Research Fellow.
Learn more about the position and apply by Nov. 13! cset.georgetown.edu/job/research...
CVSS V3.1: HIGH
NVIDIA UFM Enterprise, UFM Appliance, and UFM CyberAI contain a vulnerability where an attacker can cause an improper authentication issue by sending a malformed request through the Ethernet management interface. A successful...
#security #infosec #cve-alert
CVSS V3.1: HIGH
NVIDIA UFM Enterprise, UFM Appliance, and UFM CyberAI contain a vulnerability where an attacker can cause an improper authentication issue by sending a malformed request through the Ethernet management interface. A successful...
#security #infosec #cve-alert
www.itforbusiness.fr/les-paradoxe... #DSI #RSSI #Cybersecurité #CyberAI

www.itforbusiness.fr/les-paradoxe... #DSI #RSSI #Cybersecurité #CyberAI
https://eldinero.lat/posts/D73CE4E5-98B0-4DFA-8B7A-D50D2C13D60B
https://eldinero.lat/posts/D73CE4E5-98B0-4DFA-8B7A-D50D2C13D60B

#AISecurity, #CyberDefense, #MachineLearningSecurity, #ThreatIntelligence, #ZeroTrust, #SOCAutomation, #CyberAI, #SecurityAutomation, #UEBA, #SOAR, #VulnerabilityManagement,
medium.com/@jckapadia00...

#AISecurity, #CyberDefense, #MachineLearningSecurity, #ThreatIntelligence, #ZeroTrust, #SOCAutomation, #CyberAI, #SecurityAutomation, #UEBA, #SOAR, #VulnerabilityManagement,
medium.com/@jckapadia00...

