While this site initially showed promise, I've grown tired with its lack of improvement.
You'll find me @[email protected] on Mastodon.
And RDP still accepted my old password. (No Microsoft Authenticator required)
🤷♂️


And RDP still accepted my old password. (No Microsoft Authenticator required)
🤷♂️
WDAC will only block and not allow.😬

WDAC will only block and not allow.😬
I suppose I was referring to Twitter and Mastodon.
With either of those you can upload a media thing (image, animated, GIF, MP4, etc.), and the trigger to do that is you click a single "media" button.
Separate buttons is completely unnecessary.


I suppose I was referring to Twitter and Mastodon.
With either of those you can upload a media thing (image, animated, GIF, MP4, etc.), and the trigger to do that is you click a single "media" button.
Separate buttons is completely unnecessary.
Animated GIF images maybe need to be uploaded using the "Movie" icon, because GIF89a's are clearly not images? 🤔
Animated GIF images maybe need to be uploaded using the "Movie" icon, because GIF89a's are clearly not images? 🤔
FFS why is this platform so slow to improve?

FFS why is this platform so slow to improve?


If you have a lot of posts to delete, it's going to take a while.
But is worth it, IMO.


If you have a lot of posts to delete, it's going to take a while.
But is worth it, IMO.
Delete away, friends!

Delete away, friends!

The company that runs Pinduoduo and Temu decided to use an 0day exploit.


The company that runs Pinduoduo and Temu decided to use an 0day exploit.
You... You do know that people can't click buttons on paper, right?

You... You do know that people can't click buttons on paper, right?
labs.watchtowr.com/are-we-now-p...


labs.watchtowr.com/are-we-now-p...
CVE-2024-21893 is merely CVE-2023-36661

CVE-2024-21893 is merely CVE-2023-36661
How was this handled?
HackerOne assigned CVE-2024-21893 to capture this.
Nobody knows how CVE works, and nobody enforces any rules. 🤦♂️
twitter.com/stephenfewer...

How was this handled?
HackerOne assigned CVE-2024-21893 to capture this.
Nobody knows how CVE works, and nobody enforces any rules. 🤦♂️
twitter.com/stephenfewer...
Completely ridiculous, right???
Actually, no. This advice is evidence that Barracuda actually understands how things work.
Thoughts and prayers for the Ivanti customers out there...

Completely ridiculous, right???
Actually, no. This advice is evidence that Barracuda actually understands how things work.
Thoughts and prayers for the Ivanti customers out there...

I mean, why bother?

I mean, why bother?
As such, here are the mitigitations for CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893.
CVE-2024-21888 has no love?
tinyurl.com/2vyjedh6
tinyurl.com/bp5t7vr5
tinyurl.com/4jjmtnj9



As such, here are the mitigitations for CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893.
CVE-2024-21888 has no love?
tinyurl.com/2vyjedh6
tinyurl.com/bp5t7vr5
tinyurl.com/4jjmtnj9
No, not those (which are STILL unfixed).
The new ones: CVE-2024-21888 (privesc to admin) and CVE-2024-21893 (SSRF to access "restricted resources")
mitigation.release.20240126.5.xml
forums.ivanti.com/s/article/KB...

No, not those (which are STILL unfixed).
The new ones: CVE-2024-21888 (privesc to admin) and CVE-2024-21893 (SSRF to access "restricted resources")
mitigation.release.20240126.5.xml
forums.ivanti.com/s/article/KB...
Which makes me wonder... what's the go-to Wi-Fi 6E adapter that people use in the Linux world these days?
Or has the Linux world not quite embraced Wi-Fi yet, and reliable requires wired?
bugzilla.kernel.org/show_bug.cgi...
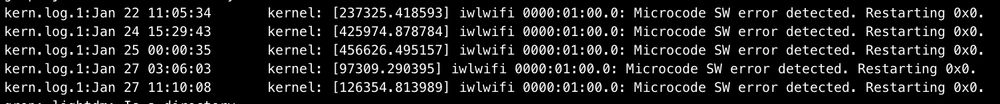
Which makes me wonder... what's the go-to Wi-Fi 6E adapter that people use in the Linux world these days?
Or has the Linux world not quite embraced Wi-Fi yet, and reliable requires wired?
bugzilla.kernel.org/show_bug.cgi...
I guess updating websites without breaking existing links is... difficult?

I guess updating websites without breaking existing links is... difficult?


