While this site initially showed promise, I've grown tired with its lack of improvement.
You'll find me @[email protected] on Mastodon.

1) First download an archive of your data. (There might be a 1-day delay before you get it)
x.com/settings/dow...
1) First download an archive of your data. (There might be a 1-day delay before you get it)
x.com/settings/dow...

Turns out that their Android app was utilizing an 0day exploit to achieve an advantage over their competition.
Totally normal stuff going on here.
arstechnica.com/information-...
Turns out that their Android app was utilizing an 0day exploit to achieve an advantage over their competition.
Totally normal stuff going on here.
arstechnica.com/information-...
You... You do know that people can't click buttons on paper, right?

You... You do know that people can't click buttons on paper, right?
labs.watchtowr.com/are-we-now-p...


labs.watchtowr.com/are-we-now-p...
How was this handled?
HackerOne assigned CVE-2024-21893 to capture this.
Nobody knows how CVE works, and nobody enforces any rules. 🤦♂️
twitter.com/stephenfewer...

How was this handled?
HackerOne assigned CVE-2024-21893 to capture this.
Nobody knows how CVE works, and nobody enforces any rules. 🤦♂️
twitter.com/stephenfewer...
But what about this recommended factory reset? That restores it to the state when you got it from the factory, right?
Get real.
Please avoid magical thinking, folks 🪄
(insert desire for GIFs here)
But what about this recommended factory reset? That restores it to the state when you got it from the factory, right?
Get real.
Please avoid magical thinking, folks 🪄
(insert desire for GIFs here)
I mean, why bother?

I mean, why bother?
No, not those (which are STILL unfixed).
The new ones: CVE-2024-21888 (privesc to admin) and CVE-2024-21893 (SSRF to access "restricted resources")
mitigation.release.20240126.5.xml
forums.ivanti.com/s/article/KB...

No, not those (which are STILL unfixed).
The new ones: CVE-2024-21888 (privesc to admin) and CVE-2024-21893 (SSRF to access "restricted resources")
mitigation.release.20240126.5.xml
forums.ivanti.com/s/article/KB...
Which makes me wonder... what's the go-to Wi-Fi 6E adapter that people use in the Linux world these days?
Or has the Linux world not quite embraced Wi-Fi yet, and reliable requires wired?
bugzilla.kernel.org/show_bug.cgi...
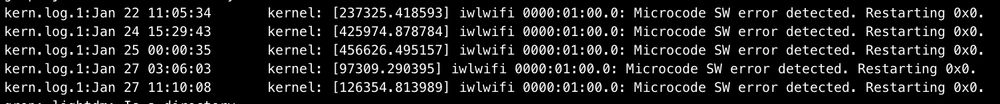
Which makes me wonder... what's the go-to Wi-Fi 6E adapter that people use in the Linux world these days?
Or has the Linux world not quite embraced Wi-Fi yet, and reliable requires wired?
bugzilla.kernel.org/show_bug.cgi...
No? Just me?
No? Just me?

"stop pushing configurations to appliances with the [workaround] XML in place... it stops some key web services from functioning, and stops the mitigation from functioning"
Surely no regrets with Ivanti purchases here.
forums.ivanti.com/s/article/KB...

"stop pushing configurations to appliances with the [workaround] XML in place... it stops some key web services from functioning, and stops the mitigation from functioning"
Surely no regrets with Ivanti purchases here.
forums.ivanti.com/s/article/KB...

If you choose to explicitly enable shell=True, it's the application's responsibility to avoid shell injection vulnerabilities.
Ivanti:
(Hold my beer)
YOLO!!!!!!!1
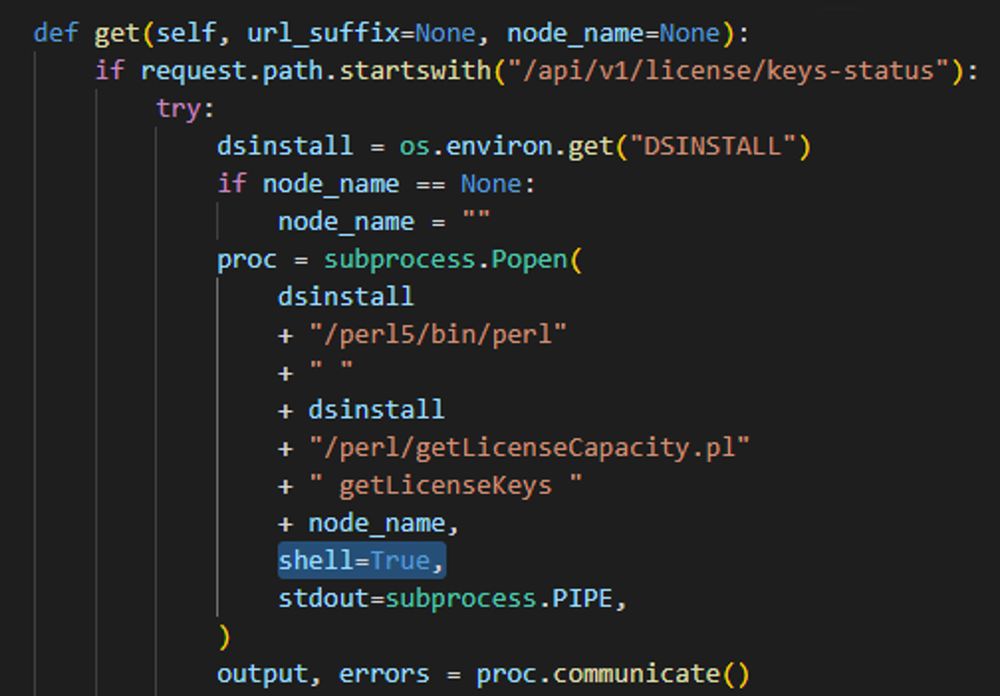

If you choose to explicitly enable shell=True, it's the application's responsibility to avoid shell injection vulnerabilities.
Ivanti:
(Hold my beer)
YOLO!!!!!!!1
attackerkb.com/topics/AdUh6...


attackerkb.com/topics/AdUh6...
Apache created CVE-2023-49070 to capture: "Our OFBiz product has Apache XML-RPC, which is vulnerable to CVE-2019-17570".
This seems... wrong?
If every vendor created a new CVE to capture "Hey, we use library <foo> that already has a CVE", how can this possibly scale?
Apache created CVE-2023-49070 to capture: "Our OFBiz product has Apache XML-RPC, which is vulnerable to CVE-2019-17570".
This seems... wrong?
If every vendor created a new CVE to capture "Hey, we use library <foo> that already has a CVE", how can this possibly scale?
Oops? 🤦♂️
zolutal.github.io/aslrnt/
(Insert desire for BlueSky to support animated GIFs here)

Oops? 🤦♂️
zolutal.github.io/aslrnt/
(Insert desire for BlueSky to support animated GIFs here)
If you think your web server was compromised, would you use a remote web browser to confirm whether this is true?
This is what the "external" ICT workflow does.
Thoughts and prayers to customers.




If you think your web server was compromised, would you use a remote web browser to confirm whether this is true?
This is what the "external" ICT workflow does.
Thoughts and prayers to customers.

I really wish this exodus would happen quicker than the current pace. 😕

I really wish this exodus would happen quicker than the current pace. 😕
Elmo finds a way to make it better for the worst people on the planet.
I also love how it says "subscribed", which I'm clearly not, and have had the account blocked for years.
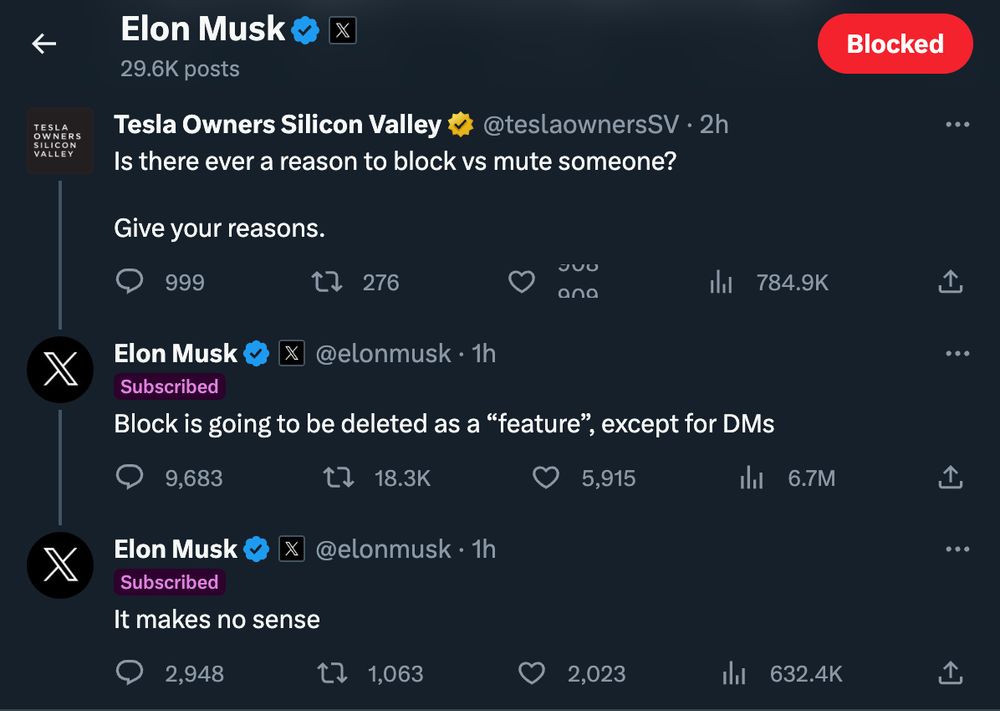
Elmo finds a way to make it better for the worst people on the planet.
I also love how it says "subscribed", which I'm clearly not, and have had the account blocked for years.
My hope is that BlueSky will get to the point where it's open to the public before Twitter explodes and/or the exodus actually happens.
Otherwise, it'll just be a fun little experiment.

My hope is that BlueSky will get to the point where it's open to the public before Twitter explodes and/or the exodus actually happens.
Otherwise, it'll just be a fun little experiment.

