have a look at case 1. case 2 has been documented by MS int the meantime as you discovered.
for the exclusions of policies, there are similar problems as in case 1. so if you want exclude a single (3rd pt) app from MFA you can't in some cases.

have a look at case 1. case 2 has been documented by MS int the meantime as you discovered.
for the exclusions of policies, there are similar problems as in case 1. so if you want exclude a single (3rd pt) app from MFA you can't in some cases.
for example it's not possible anymore to exlude or include a specific app in some circumstances.
CA unfortunatly is getting useless for 3rd party apps without resources within M365..
for example it's not possible anymore to exlude or include a specific app in some circumstances.
CA unfortunatly is getting useless for 3rd party apps without resources within M365..
www.msb365.blog?p=5780
When MS decided to change from targeting resources instead of apps, several problems have been created for us & our customers. Hopefully MS will resolve this issues also on a technical level, not only adjusting the docs..
www.msb365.blog?p=5780
When MS decided to change from targeting resources instead of apps, several problems have been created for us & our customers. Hopefully MS will resolve this issues also on a technical level, not only adjusting the docs..
Auth behaviour :
- Web: Applied
- Single-page application: NOT Applied
- Mobile and desktop applications: NOT Applied
This applies only to policies with GRANT Controls. Policies with Session controls are always applied.
Auth behaviour :
- Web: Applied
- Single-page application: NOT Applied
- Mobile and desktop applications: NOT Applied
This applies only to policies with GRANT Controls. Policies with Session controls are always applied.
CA Policy, Include Resources: All, Exclude: None
Auth behaviour depending on platform config of the App:
- Web: Applied
- Single-page application: Applied
- Mobile and desktop applications: Applied
CA Policy, Include Resources: All, Exclude: None
Auth behaviour depending on platform config of the App:
- Web: Applied
- Single-page application: Applied
- Mobile and desktop applications: Applied
Its seems that, i can exclude any random app (tested with custom App or even 'Report Message').
As soon as one app is excluded from the CA Policy, when getting a token for my test app, behaviour is again the same.
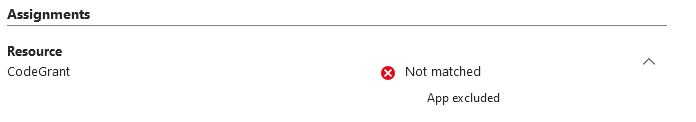
Its seems that, i can exclude any random app (tested with custom App or even 'Report Message').
As soon as one app is excluded from the CA Policy, when getting a token for my test app, behaviour is again the same.
Other CAs targeted to specific App still 'not included', but that seems to be expected behaviour.
Other CAs targeted to specific App still 'not included', but that seems to be expected behaviour.
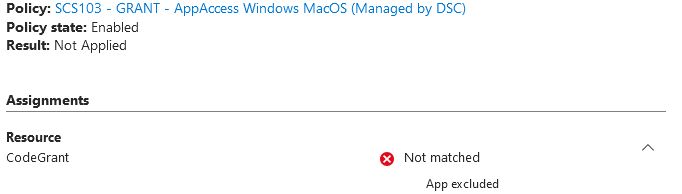
BUT: I might have found the problem: CA Policy which is targeted to all resources had one App excluded: 'Microsoft Intune Enrollment'
BUT: I might have found the problem: CA Policy which is targeted to all resources had one App excluded: 'Microsoft Intune Enrollment'
"https://graph.microsoft.com/v1.0/me/people"
with platform configuration SinglePageApp (also public client), I'm not able to do so withour fullfulling requested CA controls.
"https://graph.microsoft.com/v1.0/me/people"
with platform configuration SinglePageApp (also public client), I'm not able to do so withour fullfulling requested CA controls.
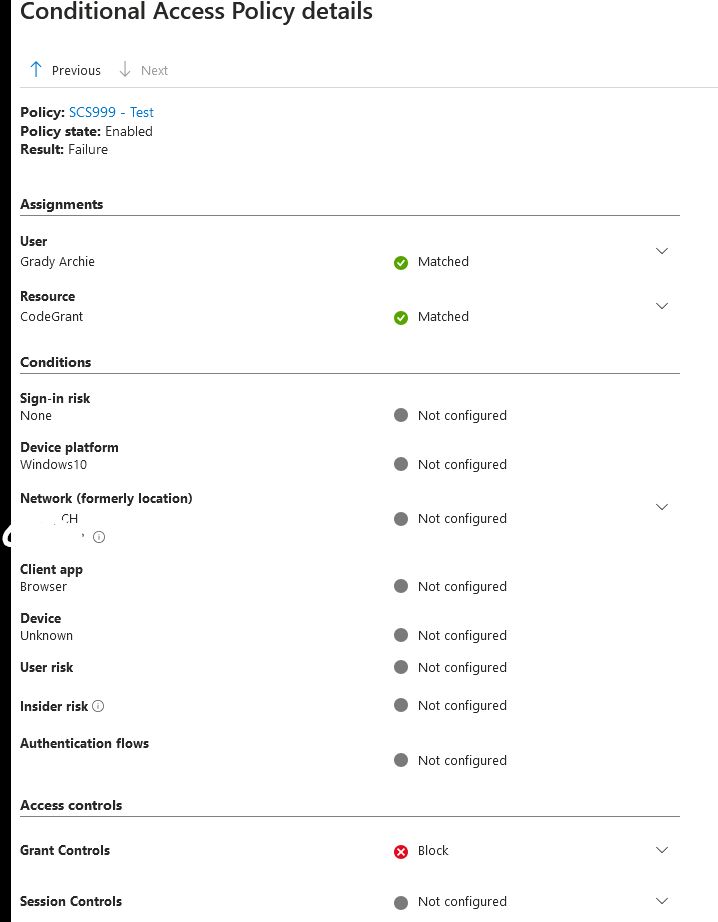
And why is there a difference in CA Policy evaluation between the different platforms when requesting the same scopes?
And why is there a difference in CA Policy evaluation between the different platforms when requesting the same scopes?
Therefore #ZeroTrust and #SASE implementations with CA are not possible anymore. What am I missing?
@merill.net @markasimos.bsky.social
#MicrosoftSecurity
Therefore #ZeroTrust and #SASE implementations with CA are not possible anymore. What am I missing?
@merill.net @markasimos.bsky.social
#MicrosoftSecurity
When requesting a token for the platform 'Mobile and desktop applications' #ConditionalAccess policies are 'not applied' anymore because the app is 'excluded':
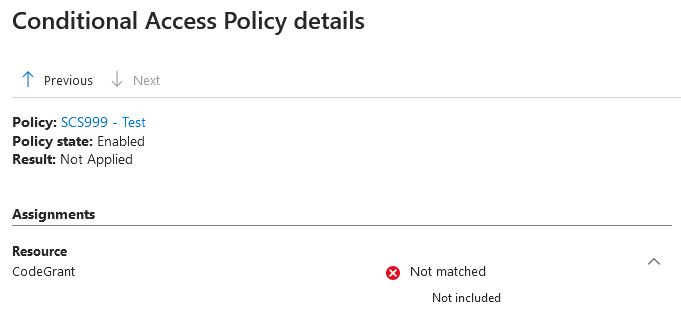
When requesting a token for the platform 'Mobile and desktop applications' #ConditionalAccess policies are 'not applied' anymore because the app is 'excluded':
Device Filter would require an additional Policy wich blocks Devices (Control Block) and exclude Devices with correct enrollment profile name.
Device Filter would require an additional Policy wich blocks Devices (Control Block) and exclude Devices with correct enrollment profile name.
If you use other enrollment methods for Android (MDM), maybe you could use the include Filter IN CA (personal, corporate, .)
If you use other enrollment methods for Android (MDM), maybe you could use the include Filter IN CA (personal, corporate, .)

