





www.volexity.com/blog/2025/04... #dfir
www.volexity.com/blog/2025/04... #dfir
#dfir

#dfir
61 Talks submitted and so many too good that, once again, we had to increase a bit the number of accepted talks.🔥
#PIVOTcon25 Agenda is finally here, and the caliber is insane!!! Check it out➡️ pivotcon.org/agenda-2025/
#CTI #ThreatIntel
Talks and presenters in🧵⬇️ 1/18
61 Talks submitted and so many too good that, once again, we had to increase a bit the number of accepted talks.🔥
#PIVOTcon25 Agenda is finally here, and the caliber is insane!!! Check it out➡️ pivotcon.org/agenda-2025/
#CTI #ThreatIntel
Talks and presenters in🧵⬇️ 1/18
Paul Rascagneres, Principal Threat Researcher, Volexity (@r00tbsd , @r00tbsd.bsky.social , @[email protected])
5/18

Paul Rascagneres, Principal Threat Researcher, Volexity (@r00tbsd , @r00tbsd.bsky.social , @[email protected])
5/18
#dfir #threatintel #m365security
#dfir #threatintel #m365security
#dfir
#dfir
@citizenlab.ca
leveraging vulnerabilities in applications embedding old versions of Chromium trendmicro.com/en_us/resear...
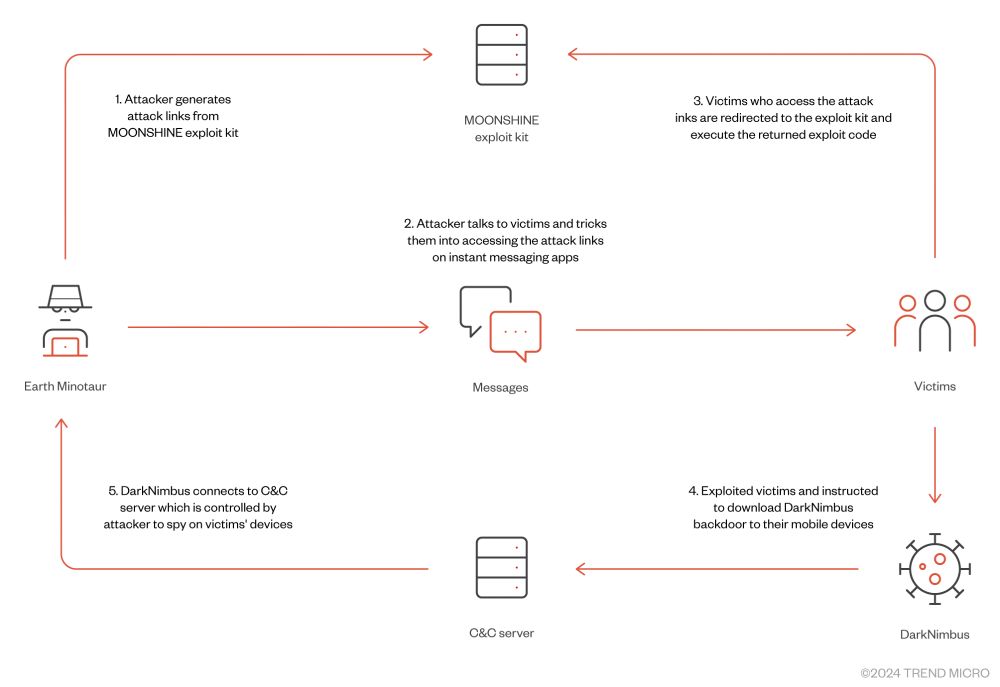
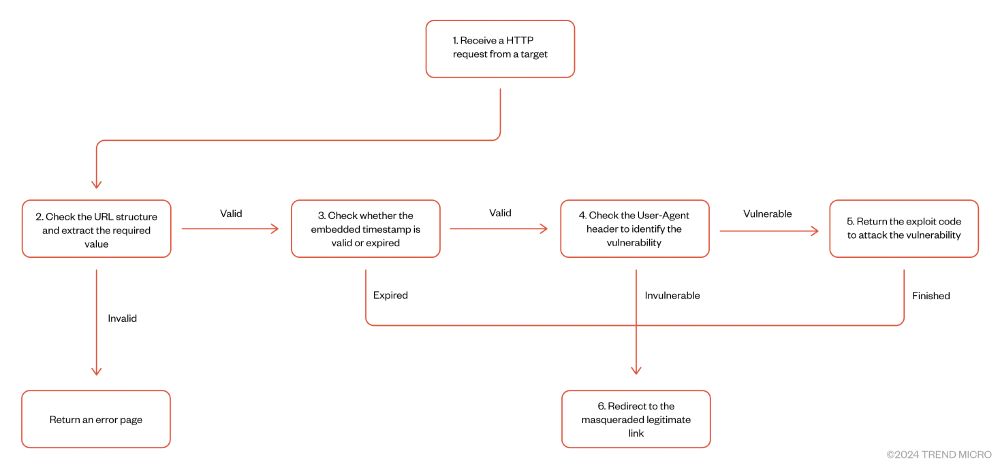
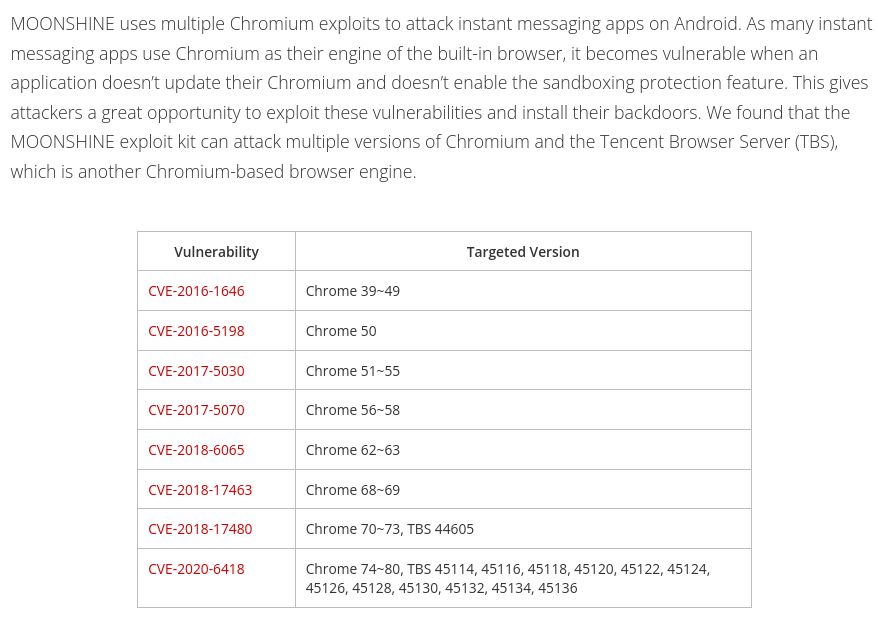
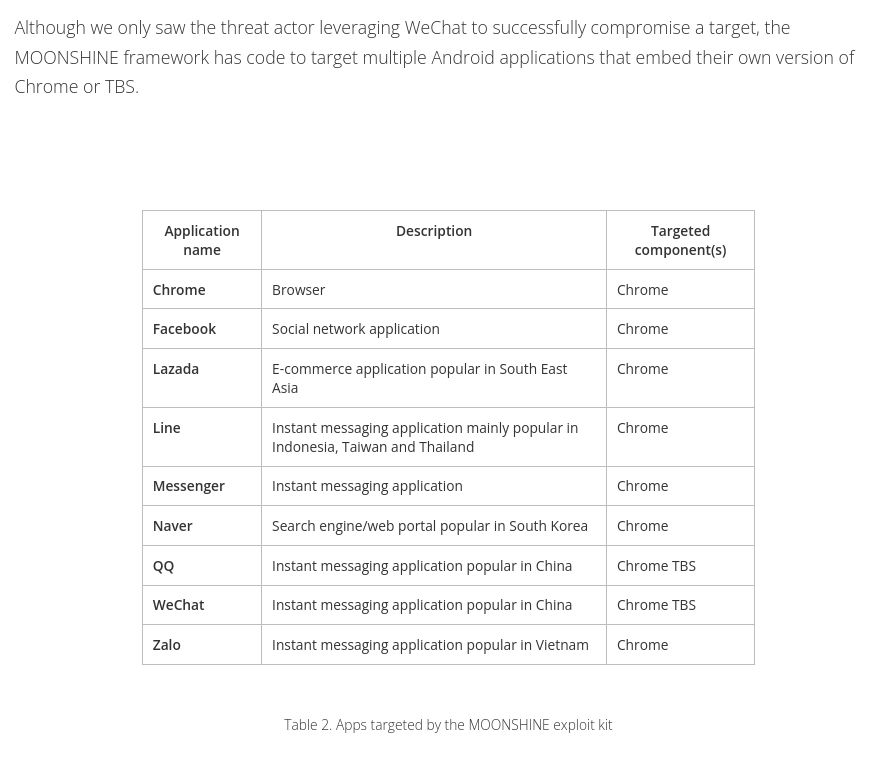
@citizenlab.ca
leveraging vulnerabilities in applications embedding old versions of Chromium trendmicro.com/en_us/resear...
Remember
- one track,30m
- no recording/streaming/tweeting. U should feel comfy to share more
- No TLP:WHITE
- Original content only
Let us guide u through with a little meme-thread
#CTI #ThreatIntel 1/10

Remember
- one track,30m
- no recording/streaming/tweeting. U should feel comfy to share more
- No TLP:WHITE
- Original content only
Let us guide u through with a little meme-thread
#CTI #ThreatIntel 1/10
pivotcon.org
#CTI #ThreatResearch #ThreatIntel
Please read carefully the whole 🧵 for the rules about invite -> registration (1/5)

pivotcon.org
#CTI #ThreatResearch #ThreatIntel
Please read carefully the whole 🧵 for the rules about invite -> registration (1/5)
* A 0-day exploit
* Physical trips to the customer site to determine root cause
* Compromise via Wi-Fi.
www.volexity.com/blog/2024/11...
#nearestneighbor #threatintel

* A 0-day exploit
* Physical trips to the customer site to determine root cause
* Compromise via Wi-Fi.
www.volexity.com/blog/2024/11...
#nearestneighbor #threatintel
Read more here: www.volexity.com/blog/2024/11...

Read more here: www.volexity.com/blog/2024/11...

