
Figma's MCP tool has just had a serious security issue that allowed hackers to execute code remotely.
New MCPs are released daily, but AI companies fail to verify their safety before they are used widely.

Figma's MCP tool has just had a serious security issue that allowed hackers to execute code remotely.
New MCPs are released daily, but AI companies fail to verify their safety before they are used widely.
🎯 FOR SECURITY TEAMS
→ Find tools in seconds, not hours
18 categories → 106 specializations → 944 specific tasks
Need "API security testing for cloud"? Go straight there.

🎯 FOR SECURITY TEAMS
→ Find tools in seconds, not hours
18 categories → 106 specializations → 944 specific tasks
Need "API security testing for cloud"? Go straight there.
And yes, their own on-premises GitLab instance.
Shocking? Not really.
Today, it doesn't really matter if you host your systems on-premises or in the cloud.

And yes, their own on-premises GitLab instance.
Shocking? Not really.
Today, it doesn't really matter if you host your systems on-premises or in the cloud.
They’re game-changers for building and extending LLMs.
But let’s be honest: from a cybersecurity perspective, MCPs are a dangerous wild card for enterprises.
Right now, it’s almost impossible to verify which MCP servers are legit.

They’re game-changers for building and extending LLMs.
But let’s be honest: from a cybersecurity perspective, MCPs are a dangerous wild card for enterprises.
Right now, it’s almost impossible to verify which MCP servers are legit.
Many are calling this a “win” for CISOs.
Regulators are preparing to fine executives directly when security breaches occur.
People are calling this an 'accountability revolution' in cybersecurity, but I think that's premature.

Many are calling this a “win” for CISOs.
Regulators are preparing to fine executives directly when security breaches occur.
People are calling this an 'accountability revolution' in cybersecurity, but I think that's premature.
In just the past 28 days:
→ 13,500 unique visitors
→ 8,500 from organic search engines
→ 100+ visitors from ChatGPT
ChatGPT is now sending us traffic as people ask it for cybersecurity tool recommendations.


In just the past 28 days:
→ 13,500 unique visitors
→ 8,500 from organic search engines
→ 100+ visitors from ChatGPT
ChatGPT is now sending us traffic as people ask it for cybersecurity tool recommendations.
The traditional approach to AI agent development has been painfully complex – requiring intricate orchestration, custom parsers, and months of tuning.
aws.amazon.com/blogs/openso...
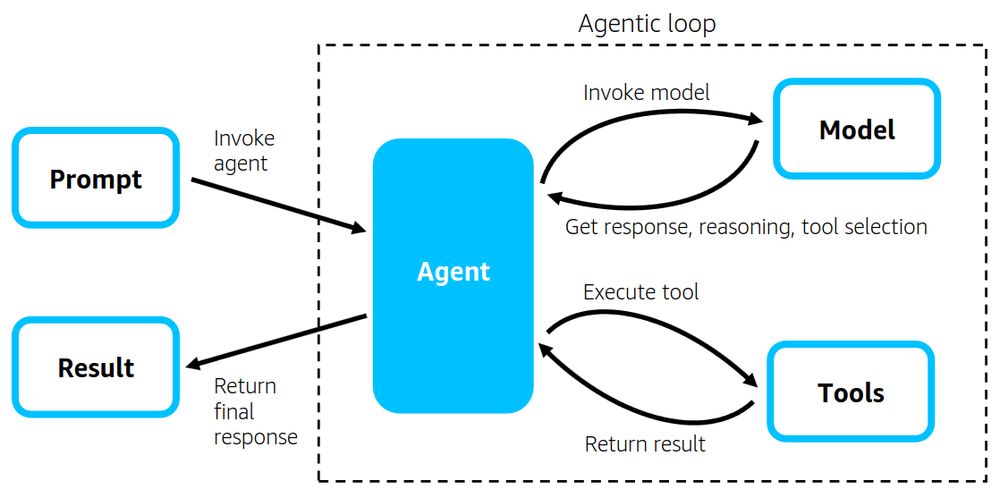
The traditional approach to AI agent development has been painfully complex – requiring intricate orchestration, custom parsers, and months of tuning.
aws.amazon.com/blogs/openso...
The data tells a sobering story:
‣ 55% of organizations still operate with crippling IT/security data silos
‣ 62% say these silos slow security response times

The data tells a sobering story:
‣ 55% of organizations still operate with crippling IT/security data silos
‣ 62% say these silos slow security response times
Here's my decade-tested list:
Want to cultivate a strategic security mindset? → Join 1000+ cybersecurity leaders developing executive-level thinking: mandos.io/newsletter

Here's my decade-tested list:
Want to cultivate a strategic security mindset? → Join 1000+ cybersecurity leaders developing executive-level thinking: mandos.io/newsletter
Research just published shows LLMs failing dramatically on actual threat reports. Previous papers claimed 80-90% accuracy, but they tested on tiny text samples (fewer than 200 words). Real CTI reports average 3,000+ words.

Research just published shows LLMs failing dramatically on actual threat reports. Previous papers claimed 80-90% accuracy, but they tested on tiny text samples (fewer than 200 words). Real CTI reports average 3,000+ words.
These 10 findings go beyond the headlines:
AI is advancing at unprecedented speed, transforming business, science, and daily life.
After diving deep into Stanford's comprehensive report, these key trends emerge with clarity.

These 10 findings go beyond the headlines:
AI is advancing at unprecedented speed, transforming business, science, and daily life.
After diving deep into Stanford's comprehensive report, these key trends emerge with clarity.
Want maximum security? Disconnect everything and lock it in a vault.
Congratulations, you've achieved 99% security and 0% business value.
The real cybersecurity challenge isn't building Fort Knox. It's about:

Want maximum security? Disconnect everything and lock it in a vault.
Congratulations, you've achieved 99% security and 0% business value.
The real cybersecurity challenge isn't building Fort Knox. It's about:
Yesterday Wiz announced their new MCP Server - an implementation of the Model Context Protocol that's reshaping how AI and security tools communicate.
The security community is buzzing about it, but what's the real impact?
Let's break it down.

Yesterday Wiz announced their new MCP Server - an implementation of the Model Context Protocol that's reshaping how AI and security tools communicate.
The security community is buzzing about it, but what's the real impact?
Let's break it down.
CrowdStrike just revealed a fascinating proof of concept at NVIDIA GTC 2025 - using AI to secure AI-generated code.
With "vibe coding" becoming mainstream, we're facing a potential flood of vulnerable code.

CrowdStrike just revealed a fascinating proof of concept at NVIDIA GTC 2025 - using AI to secure AI-generated code.
With "vibe coding" becoming mainstream, we're facing a potential flood of vulnerable code.
After digging through the data, here are 5 findings worth sharing:

After digging through the data, here are 5 findings worth sharing:
Your robust SOC won't detect:

Your robust SOC won't detect:
A GitHub repository of 300 open-source MCP servers just dropped, including 16 security-focused implementations that could transform your SecOps workflow.
But what does this mean for security professionals?
(continue reading for a link)

A GitHub repository of 300 open-source MCP servers just dropped, including 16 security-focused implementations that could transform your SecOps workflow.
But what does this mean for security professionals?
(continue reading for a link)
1. Shared knowledge repositories are game-changing. M-25-21 and M-25-22 mandate government-wide sharing of AI best practices, creating the first collaborative AI knowledge ecosystem across federal agencies.

1. Shared knowledge repositories are game-changing. M-25-21 and M-25-22 mandate government-wide sharing of AI best practices, creating the first collaborative AI knowledge ecosystem across federal agencies.

The Model Context Protocol (MCP) is revolutionizing how AI applications access data and tools - essentially becoming the "USB-C port for AI." But this powerful capability creates serious security blind spots.

The Model Context Protocol (MCP) is revolutionizing how AI applications access data and tools - essentially becoming the "USB-C port for AI." But this powerful capability creates serious security blind spots.
Just came across an interesting case of how Ankit Masrani landed a cybersecurity role at Microsoft without a traditional security background. See his resume:

Just came across an interesting case of how Ankit Masrani landed a cybersecurity role at Microsoft without a traditional security background. See his resume:
Cloudflare just announced an AI-powered context analysis feature for their DLP solution that actually learns from your feedback to reduce false positives over time.
As someone who's battled DLP alert f

Cloudflare just announced an AI-powered context analysis feature for their DLP solution that actually learns from your feedback to reduce false positives over time.
As someone who's battled DLP alert f
‣ Universal "language of thought" across languages
‣ Plans ahead in writing
‣ Can fabricate reasoning when misled
‣ Declines answering when unsure
Useful? Join my newsletter for more: mandos.io/newsletter
‣ Universal "language of thought" across languages
‣ Plans ahead in writing
‣ Can fabricate reasoning when misled
‣ Declines answering when unsure
Useful? Join my newsletter for more: mandos.io/newsletter
Let's talk about the cybersecurity equivalent of emergency room triage.
Unlike goal-based agents that see the world in black and white, utility-based agents operate on a spectrum of preferences.

Let's talk about the cybersecurity equivalent of emergency room triage.
Unlike goal-based agents that see the world in black and white, utility-based agents operate on a spectrum of preferences.
AWS released CloudTrail network activity events for VPC Endpoints, and it's a game-changer for those of us battling the data exfiltration problem.

AWS released CloudTrail network activity events for VPC Endpoints, and it's a game-changer for those of us battling the data exfiltration problem.

