hackarcana.com/public-exerc...
hackarcana.com/public-exerc...
(third one coming next week, will be a bit harder)

hackarcana.com/public-exerc...
hackarcana.com/public-exerc...
(third one coming next week, will be a bit harder)
This contest is designed to encourage research & development in the field of #memoryanalysis. Every year, contributions from all around the world continue to help build the next generation of #memoryforensics.

This contest is designed to encourage research & development in the field of #memoryanalysis. Every year, contributions from all around the world continue to help build the next generation of #memoryforensics.
-Starlink disables 2.5k scam compound terminals
-Caribbean hospital still down 5 months after ransomware attack
-Poland charges officials in Pegasus scandal
Newsletter: news.risky.biz/risky-bullet...
Podcast: risky.biz/RBNEWS495/

-Starlink disables 2.5k scam compound terminals
-Caribbean hospital still down 5 months after ransomware attack
-Poland charges officials in Pegasus scandal
Newsletter: news.risky.biz/risky-bullet...
Podcast: risky.biz/RBNEWS495/


See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...

See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
60% off for the next two weeks.
malwareanalysis-for-hedgehogs.learnworlds.com/course/inter...

60% off for the next two weeks.
malwareanalysis-for-hedgehogs.learnworlds.com/course/inter...
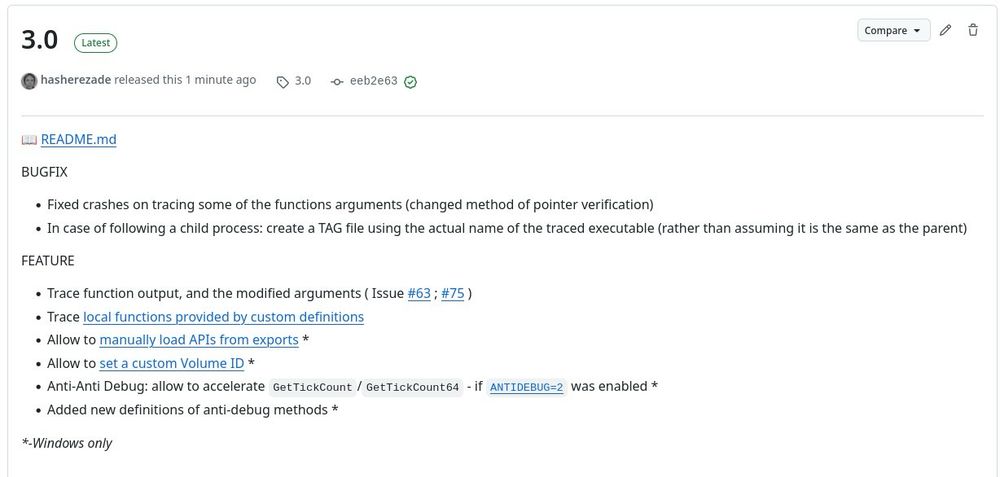
2. Or block entire CPU core. Kernel APCs run at APC_LEVEL (🤯), so thread scheduling kinda disabled (think priority == ∞).
3. Or build upon @hasherezade.bsky.social work & generalize #WaitingThreadHijacking — making it, in fact, Waitless.
2. Or block entire CPU core. Kernel APCs run at APC_LEVEL (🤯), so thread scheduling kinda disabled (think priority == ∞).
3. Or build upon @hasherezade.bsky.social work & generalize #WaitingThreadHijacking — making it, in fact, Waitless.
It's a nasty new technique: puts target thread into ⓪ deadloop, for as long as you can afford. Requires THREAD_GET_CONTEXT right.
The gist? Just spam NtGetContextThread(tgt).😸
Target will be jailed, running nt!PspGetSetContextSpecialApc 🔁.
Src & binary in [ALT].
Usecases: ⤵️
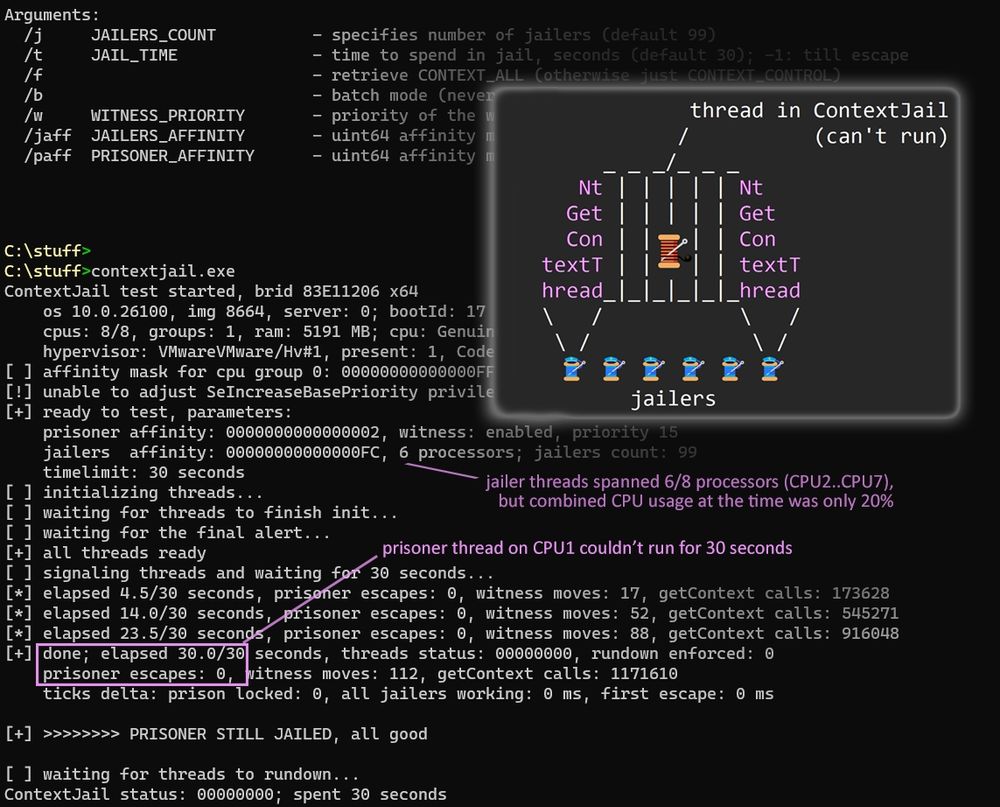
It's a nasty new technique: puts target thread into ⓪ deadloop, for as long as you can afford. Requires THREAD_GET_CONTEXT right.
The gist? Just spam NtGetContextThread(tgt).😸
Target will be jailed, running nt!PspGetSetContextSpecialApc 🔁.
Src & binary in [ALT].
Usecases: ⤵️

www.zscaler.com/blogs/securi...

www.zscaler.com/blogs/securi...
www.kelacyber.com/blog/hellcat...

www.kelacyber.com/blog/hellcat...

A+ work. This is amazing (we're going to ingest this eventually)
github.com/Cryakl/Ultim...

A+ work. This is amazing (we're going to ingest this eventually)
github.com/Cryakl/Ultim...
- automatic OEP finding, reconstructing IAT, avoiding antidebugs and fixing imports broken by shims
- automatic OEP finding, reconstructing IAT, avoiding antidebugs and fixing imports broken by shims
tmpout.sh/4/
tmpout.sh/4/
tmpout.sh/4/



catalyst.prodaft.com/public/repor...
catalyst.prodaft.com/public/repor...


