Before:
- Manufacturing Observability at Apple
- Co-founder at Transloadit
- Node.js Core Dev
The kind of stuff goroutines get up to behind the scenes can be truly fascinating.

The kind of stuff goroutines get up to behind the scenes can be truly fascinating.
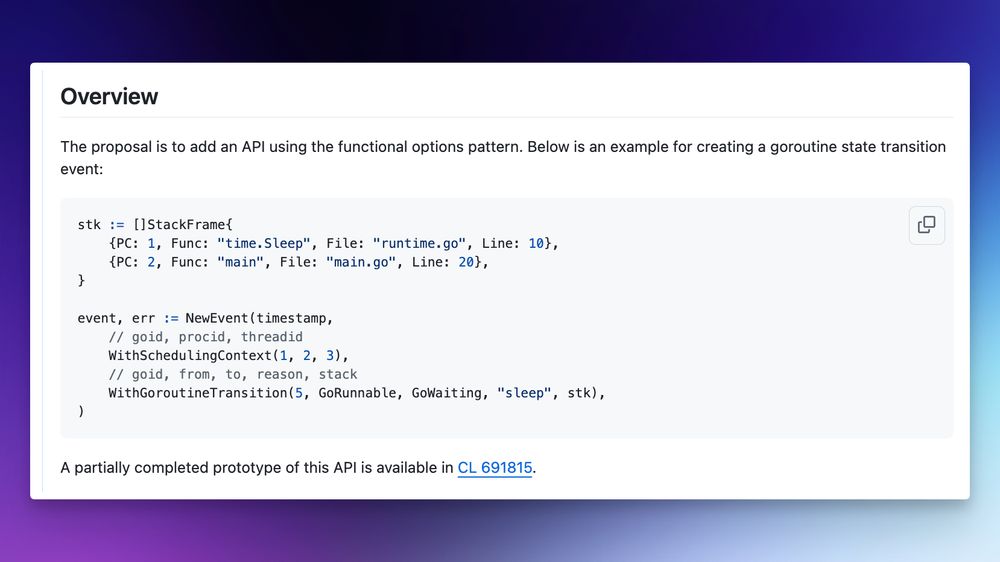
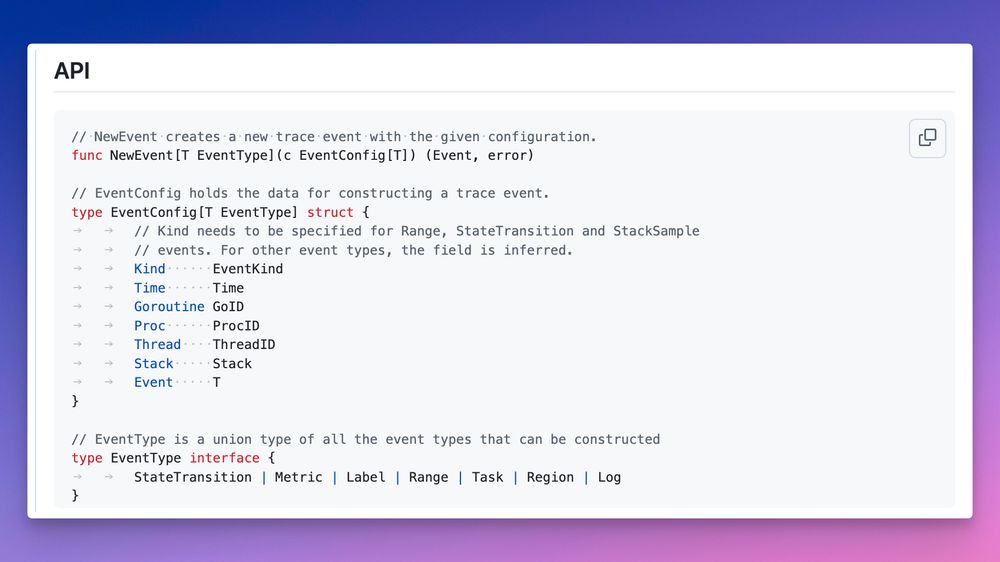
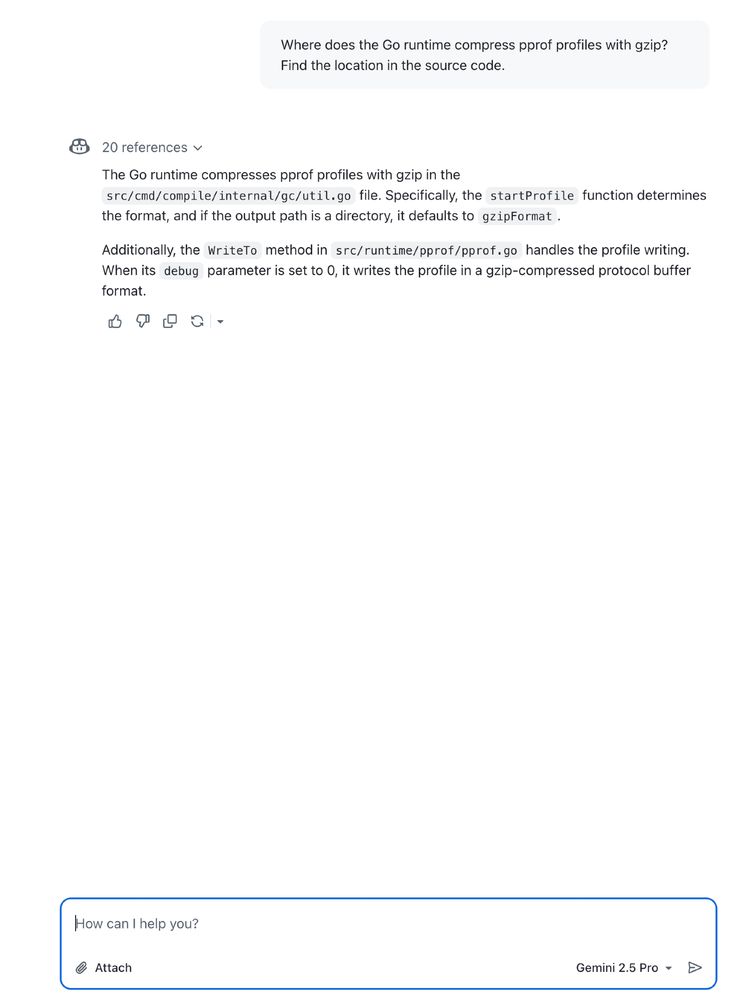
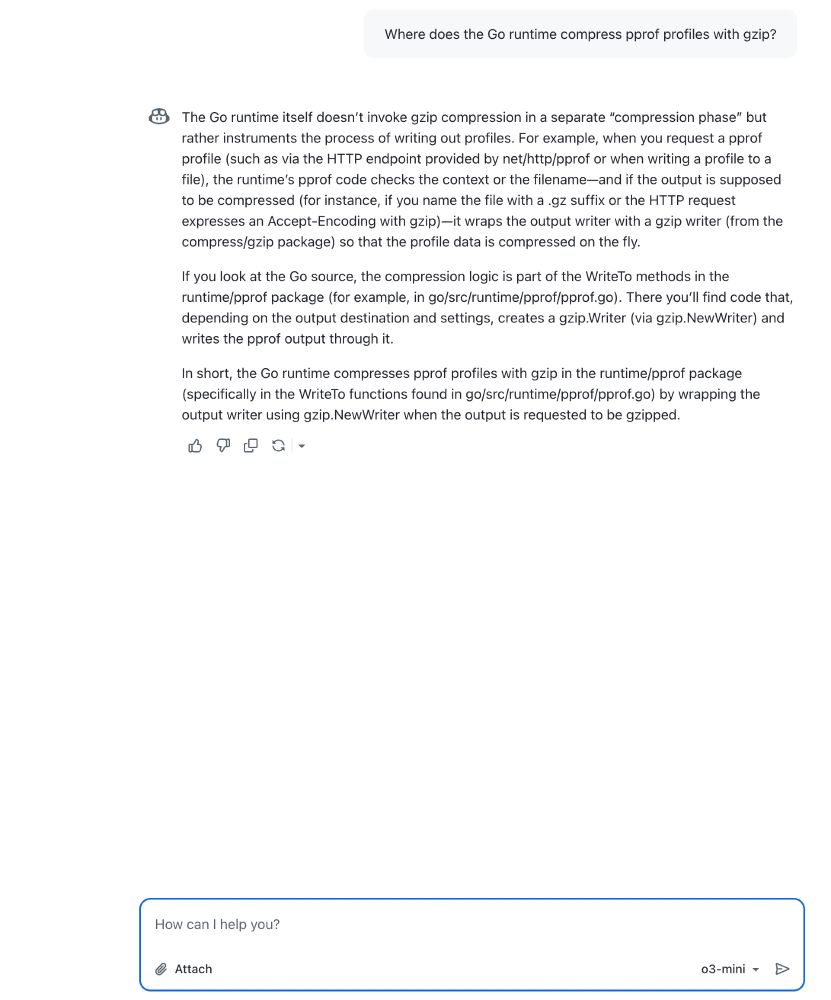
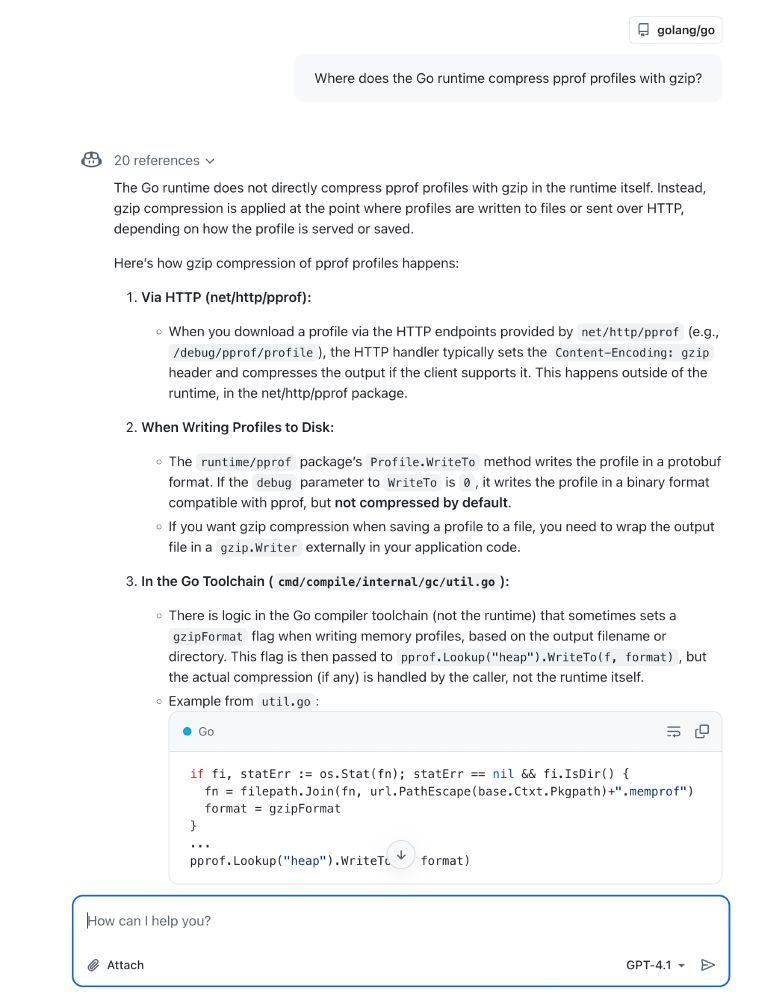
Example: Asked opus to explain some runtime internals, and then turn the analysis into a nice human-readable markdown output that I can use to explain a code change I'm making to a colleague.


Example: Asked opus to explain some runtime internals, and then turn the analysis into a nice human-readable markdown output that I can use to explain a code change I'm making to a colleague.
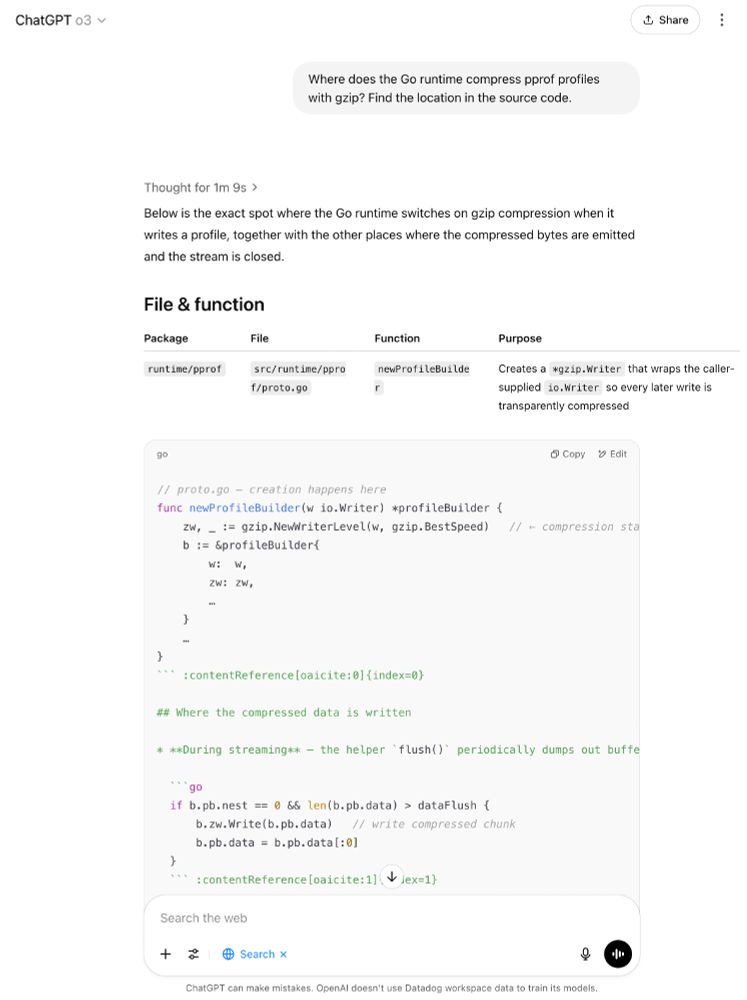
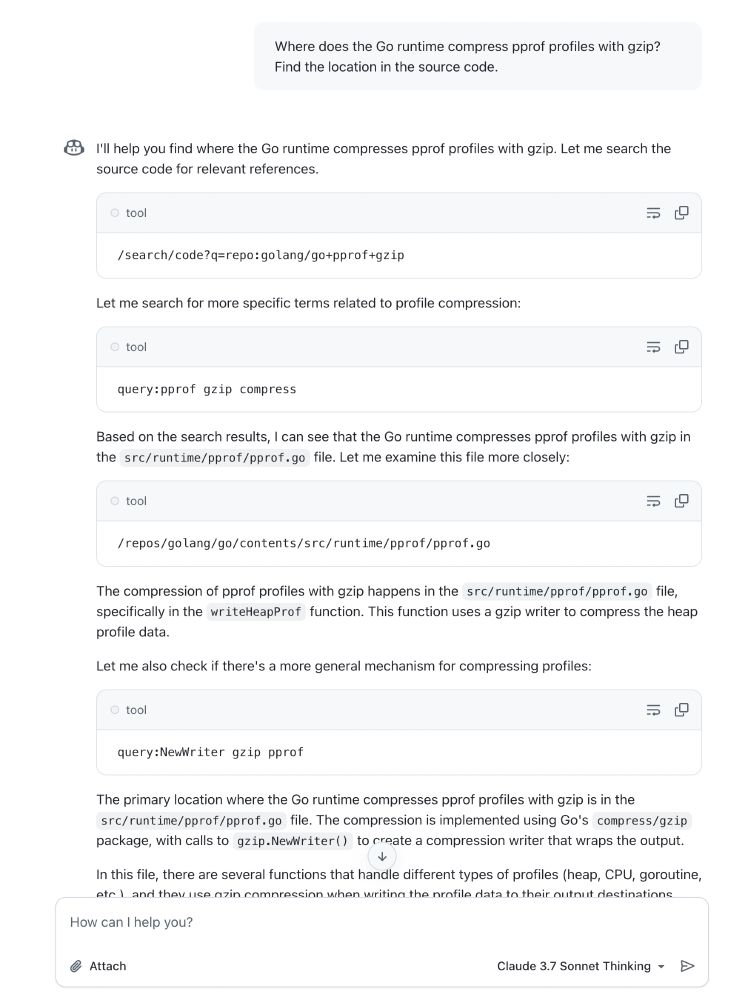
Typically they align, but one answer is better than the other.
But it turns out no amount of AI can solve the "too many chefs in the kitchen" problem 😂.


Typically they align, but one answer is better than the other.
But it turns out no amount of AI can solve the "too many chefs in the kitchen" problem 😂.

Feedback welcome! 🙇🏻♂️
Feedback welcome! 🙇🏻♂️



My team at @datadoghq.com has recently shipped a guided memory leak workflow that can quickly guide you through the right steps to find and fix the problematic code.

My team at @datadoghq.com has recently shipped a guided memory leak workflow that can quickly guide you through the right steps to find and fix the problematic code.
Also: If you enjoy a project with less than ~1000 stars, consider letting the author know. It's a small effort and can easily make someones day.

Also: If you enjoy a project with less than ~1000 stars, consider letting the author know. It's a small effort and can easily make someones day.
Here is the declaration for instrumenting the gin web framework and how it rewrites your code behind the scenes.

Here is the declaration for instrumenting the gin web framework and how it rewrites your code behind the scenes.
For example, RASP can detect if your application calls os.OpenFile() using a user provided string and block the call if it is malicious.

For example, RASP can detect if your application calls os.OpenFile() using a user provided string and block the call if it is malicious.
In addition to distributed tracing, you can also opt into additional features such as Profiling, Data Streams Monitoring and Application Security Monitoring.

In addition to distributed tracing, you can also opt into additional features such as Profiling, Data Streams Monitoring and Application Security Monitoring.
Usage is simple: Setup a repository once, and then tell Go’s toolchain to use Orchestrion in CI.

Usage is simple: Setup a repository once, and then tell Go’s toolchain to use Orchestrion in CI.
Solutions based on binary patching and eBPF have attempted to solve this, but they often come with undesirable tradeoffs.
That’s why we built Orchestrion … 🧵

Solutions based on binary patching and eBPF have attempted to solve this, but they often come with undesirable tradeoffs.
That’s why we built Orchestrion … 🧵