
Checkmarx Zero
@checkmarxzero.bsky.social
Specializing in breaking and protecting the building blocks of modern software development. From traditional #AppSec, through #opensource #SupplyChain threats, to #LLM security. https://checkmarx.com/zero/
🚨 Critical #Django #Vulnerability 🚨
CVE-2025-64459 (CVSSv3 9.1) → buff.ly/kfcbY7e
A newly disclosed flaw affects:
• 5.1 (< 5.1.14)
• 4.2 (< 4.2.26)
• 5.2 (< 5.2.8)
#AppSec #Python #WebSecurity 🧵1/5
CVE-2025-64459 (CVSSv3 9.1) → buff.ly/kfcbY7e
A newly disclosed flaw affects:
• 5.1 (< 5.1.14)
• 4.2 (< 4.2.26)
• 5.2 (< 5.2.8)
#AppSec #Python #WebSecurity 🧵1/5

November 7, 2025 at 4:23 PM
🚨 Critical #Django #Vulnerability 🚨
CVE-2025-64459 (CVSSv3 9.1) → buff.ly/kfcbY7e
A newly disclosed flaw affects:
• 5.1 (< 5.1.14)
• 4.2 (< 4.2.26)
• 5.2 (< 5.2.8)
#AppSec #Python #WebSecurity 🧵1/5
CVE-2025-64459 (CVSSv3 9.1) → buff.ly/kfcbY7e
A newly disclosed flaw affects:
• 5.1 (< 5.1.14)
• 4.2 (< 4.2.26)
• 5.2 (< 5.2.8)
#AppSec #Python #WebSecurity 🧵1/5
Seen the news about #PhantomRaven, the NPM malware campaign? Good news: Our Malicious Package Identification API already identifies relevant packages as malicious (see image for one example), and our Malicious Package Protection component has been flagging them during SCA scans. 🧵1/2

November 4, 2025 at 3:50 PM
Seen the news about #PhantomRaven, the NPM malware campaign? Good news: Our Malicious Package Identification API already identifies relevant packages as malicious (see image for one example), and our Malicious Package Protection component has been flagging them during SCA scans. 🧵1/2
🚨 A CVSSv3=10.0 #Vulnerability 🚨 in #DNN (Formerly DotNetNuke) versions prior to 10.1.1 allows unauthenticated users to upload files, even overwriting website assets and other critical components. This is a "the front door is unlocked" situation
CVE-2025-64095 -- buff.ly/UdKZLPl 🧵1/3
CVE-2025-64095 -- buff.ly/UdKZLPl 🧵1/3

October 30, 2025 at 9:08 PM
🚨 A CVSSv3=10.0 #Vulnerability 🚨 in #DNN (Formerly DotNetNuke) versions prior to 10.1.1 allows unauthenticated users to upload files, even overwriting website assets and other critical components. This is a "the front door is unlocked" situation
CVE-2025-64095 -- buff.ly/UdKZLPl 🧵1/3
CVE-2025-64095 -- buff.ly/UdKZLPl 🧵1/3
#Vulnerability alert: Python's `langgraph‑checkpoint‑sqlite` version 2.0.10 — a component of the #langchain #AI project — is vulnerable to SQL injection in filter operators ($eq, $ne, $gt, $lt, $gte, $lte) due to unsafe string concatenation. Update to version 2.0.11 buff.ly/AjRM91E

October 30, 2025 at 2:42 PM
#Vulnerability alert: Python's `langgraph‑checkpoint‑sqlite` version 2.0.10 — a component of the #langchain #AI project — is vulnerable to SQL injection in filter operators ($eq, $ne, $gt, $lt, $gte, $lte) due to unsafe string concatenation. Update to version 2.0.11 buff.ly/AjRM91E
#Vulnerability: A path traversal in #ApacheTomcat (CVE-2025-55752, #CVSS v3=7.5) allows attackers to gain access to protected URLs including `/WEB-INF/` and `/META-INF/` paths. If PUT method is enabled, this issue could in some cases lead to remote command execution buff.ly/xpnvts6

October 29, 2025 at 9:08 PM
#Vulnerability: A path traversal in #ApacheTomcat (CVE-2025-55752, #CVSS v3=7.5) allows attackers to gain access to protected URLs including `/WEB-INF/` and `/META-INF/` paths. If PUT method is enabled, this issue could in some cases lead to remote command execution buff.ly/xpnvts6
🥷 If you’re using #dotNET Core’s web server components, know about CVE-2025-55315 — an HTTP Request Smuggling vulnerability rated #CVSS 9.9.
Severity depends on how your apps handle requests, so calculate your environmental score carefully.
buff.ly/QHRV8ht
🧵1/5
Severity depends on how your apps handle requests, so calculate your environmental score carefully.
buff.ly/QHRV8ht
🧵1/5

October 24, 2025 at 9:08 PM
🥷 If you’re using #dotNET Core’s web server components, know about CVE-2025-55315 — an HTTP Request Smuggling vulnerability rated #CVSS 9.9.
Severity depends on how your apps handle requests, so calculate your environmental score carefully.
buff.ly/QHRV8ht
🧵1/5
Severity depends on how your apps handle requests, so calculate your environmental score carefully.
buff.ly/QHRV8ht
🧵1/5
Ready for a new Branded Vulnerability™? #TARmageddon (CVE-2025-62518) affects the #Rust ecosystem's may forks of `async-tar`; it's a parsing bug for the .tar file format that allows all kinds of shenanigans: at worst even #RCE (Remote Code Execution).
#CyberSecurity #SupplyChainSecurity #SCA
#CyberSecurity #SupplyChainSecurity #SCA

October 23, 2025 at 8:00 PM
Ready for a new Branded Vulnerability™? #TARmageddon (CVE-2025-62518) affects the #Rust ecosystem's may forks of `async-tar`; it's a parsing bug for the .tar file format that allows all kinds of shenanigans: at worst even #RCE (Remote Code Execution).
#CyberSecurity #SupplyChainSecurity #SCA
#CyberSecurity #SupplyChainSecurity #SCA
🚨 Adobe Commerce / #Magento just dropped the “most severe ever” flaw: #CVE-2025-54236.
Improper input validation → attackers can hijack other users’ sessions. For an #eCommerce platform, this means fraud + reputation damage.
Details: buff.ly/j3UDLHE 🧵1/4
Improper input validation → attackers can hijack other users’ sessions. For an #eCommerce platform, this means fraud + reputation damage.
Details: buff.ly/j3UDLHE 🧵1/4

September 11, 2025 at 5:22 PM
🚨 Adobe Commerce / #Magento just dropped the “most severe ever” flaw: #CVE-2025-54236.
Improper input validation → attackers can hijack other users’ sessions. For an #eCommerce platform, this means fraud + reputation damage.
Details: buff.ly/j3UDLHE 🧵1/4
Improper input validation → attackers can hijack other users’ sessions. For an #eCommerce platform, this means fraud + reputation damage.
Details: buff.ly/j3UDLHE 🧵1/4
Heads up: Edgeless Systems’ #Contrast (v1.9.0–1.12.1) has a vuln regression leaking #secrets to logs (vault creds, encryption keys, workload secrets).
🔗 buff.ly/MQXOrcZ
#AppSec #Kubernetes #CloudSecurity 🧵1/3
🔗 buff.ly/MQXOrcZ
#AppSec #Kubernetes #CloudSecurity 🧵1/3

September 4, 2025 at 2:42 PM
Heads up: Edgeless Systems’ #Contrast (v1.9.0–1.12.1) has a vuln regression leaking #secrets to logs (vault creds, encryption keys, workload secrets).
🔗 buff.ly/MQXOrcZ
#AppSec #Kubernetes #CloudSecurity 🧵1/3
🔗 buff.ly/MQXOrcZ
#AppSec #Kubernetes #CloudSecurity 🧵1/3
Someone didn't validate/sanitize incoming user-supplied payment IDs, leading to the flaw. #SQLi #AppSec #SQLinjection
If you use the Cozmoslabs WordPress Paid Membership Subscriptions plugin, update to 2.15.2 or newer. 🧵 2/2
If you use the Cozmoslabs WordPress Paid Membership Subscriptions plugin, update to 2.15.2 or newer. 🧵 2/2

September 2, 2025 at 9:08 PM
Someone didn't validate/sanitize incoming user-supplied payment IDs, leading to the flaw. #SQLi #AppSec #SQLinjection
If you use the Cozmoslabs WordPress Paid Membership Subscriptions plugin, update to 2.15.2 or newer. 🧵 2/2
If you use the Cozmoslabs WordPress Paid Membership Subscriptions plugin, update to 2.15.2 or newer. 🧵 2/2
🐞 Pay close attention to Kubernetes CVE-2025-5187.
It’s rated Medium (CVSS 6.7), but it allows node users to delete their own nodes without permission — a handy privilege escalation for attackers to cover tracks or damage integrity. buff.ly/3a9hIcB
#Kubernetes #CVE #AppSec #CloudSecurity
🧵 1/2
It’s rated Medium (CVSS 6.7), but it allows node users to delete their own nodes without permission — a handy privilege escalation for attackers to cover tracks or damage integrity. buff.ly/3a9hIcB
#Kubernetes #CVE #AppSec #CloudSecurity
🧵 1/2

September 1, 2025 at 2:12 AM
🐞 Pay close attention to Kubernetes CVE-2025-5187.
It’s rated Medium (CVSS 6.7), but it allows node users to delete their own nodes without permission — a handy privilege escalation for attackers to cover tracks or damage integrity. buff.ly/3a9hIcB
#Kubernetes #CVE #AppSec #CloudSecurity
🧵 1/2
It’s rated Medium (CVSS 6.7), but it allows node users to delete their own nodes without permission — a handy privilege escalation for attackers to cover tracks or damage integrity. buff.ly/3a9hIcB
#Kubernetes #CVE #AppSec #CloudSecurity
🧵 1/2
#LastWeekInAppSec for 19. August 2025: Code injection in AI Agent dev tool, path traversal in `go-getter`, model code injection protection bypass in TensorFlow Keras, and unsafe ImageMagick use in Rails Active storage buff.ly/clVmcTi 🧵 1/5

August 19, 2025 at 2:42 PM
#LastWeekInAppSec for 19. August 2025: Code injection in AI Agent dev tool, path traversal in `go-getter`, model code injection protection bypass in TensorFlow Keras, and unsafe ImageMagick use in Rails Active storage buff.ly/clVmcTi 🧵 1/5
Time for another #LastWeekInAppSec for 12. Aug 2025: ChatGPT-5 system prompt leaked, CISA supports CVE, and AppSec Village completes buff.ly/gsnpATQ

August 12, 2025 at 2:42 PM
Time for another #LastWeekInAppSec for 12. Aug 2025: ChatGPT-5 system prompt leaked, CISA supports CVE, and AppSec Village completes buff.ly/gsnpATQ
We're very excited to be at #DEFCON again this year, with an event and a talk in the #AppSecVillage and shenanigans throughout the weekend. If you see one of us, come say "swordfish"




August 1, 2025 at 3:32 PM
We're very excited to be at #DEFCON again this year, with an event and a talk in the #AppSecVillage and shenanigans throughout the weekend. If you see one of us, come say "swordfish"
Want to see a free, #OpenSource, developer-friendly tool for preventing secrets leaks? Checkmarx Zero's Tal Folkman will be on-site BlackHat #Arsenal (#BHUSA) to demo Too Many Secrets (2MS), available from buff.ly/Yng76l5
Mark your calendar! 2pm (local time) on 6th August, at Arsenal Station 5
Mark your calendar! 2pm (local time) on 6th August, at Arsenal Station 5

July 31, 2025 at 2:13 PM
Want to see a free, #OpenSource, developer-friendly tool for preventing secrets leaks? Checkmarx Zero's Tal Folkman will be on-site BlackHat #Arsenal (#BHUSA) to demo Too Many Secrets (2MS), available from buff.ly/Yng76l5
Mark your calendar! 2pm (local time) on 6th August, at Arsenal Station 5
Mark your calendar! 2pm (local time) on 6th August, at Arsenal Station 5
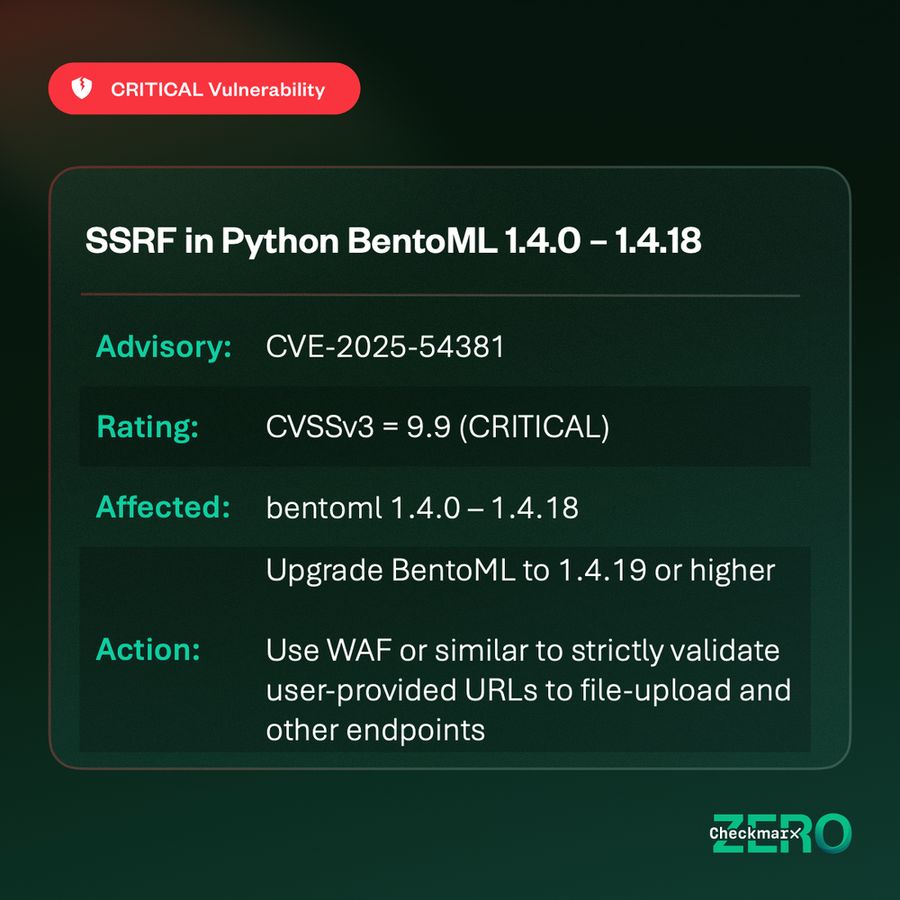
#CVE-2025-54381 → #BentoML versions 1.4.0 to 1.4.18 are vulnerable to an unauthenticated Server-Side Request Forgery (#SSRF) due to improper validation of user-provided URLs in file upload handlers. CVSSv3 base 9.9, EPSS prediction 6.02% buff.ly/0zoOTvB (🧵 1/3)
July 30, 2025 at 3:53 PM
#CVE-2025-54381 → #BentoML versions 1.4.0 to 1.4.18 are vulnerable to an unauthenticated Server-Side Request Forgery (#SSRF) due to improper validation of user-provided URLs in file upload handlers. CVSSv3 base 9.9, EPSS prediction 6.02% buff.ly/0zoOTvB (🧵 1/3)
Replit AI's whole recent incident with going rogue and causing problems with deleting databases, making up users, and other frustrating and potentially harmful activities is a good reminder that AI is very far from ready to make decisions on its own.

July 30, 2025 at 2:42 PM
Replit AI's whole recent incident with going rogue and causing problems with deleting databases, making up users, and other frustrating and potentially harmful activities is a good reminder that AI is very far from ready to make decisions on its own.
🚨 This week in #AppSec: Major Bluetooth stack vulnerabilities affecting millions of devices, NVIDIA container escape flaw, and Grafana XSS requiring only anonymous access. buff.ly/sxy6OAC
Three critical security stories you need to know about 👇
#CyberSecurity #InfoSec #VulnerabilityManagement
Three critical security stories you need to know about 👇
#CyberSecurity #InfoSec #VulnerabilityManagement

July 22, 2025 at 2:42 PM
🚨 This week in #AppSec: Major Bluetooth stack vulnerabilities affecting millions of devices, NVIDIA container escape flaw, and Grafana XSS requiring only anonymous access. buff.ly/sxy6OAC
Three critical security stories you need to know about 👇
#CyberSecurity #InfoSec #VulnerabilityManagement
Three critical security stories you need to know about 👇
#CyberSecurity #InfoSec #VulnerabilityManagement
#LastWeekInAppSec
⎈ The Kubernetes package manager Helm has a high-severity Code Injection vulnerability CVE-2025-53547.
🚂 The Conductor open-source microservices workflow orchestrator is vulnerable to a Remote Code Execution #RCE (CVE-2025-26074)
More details: buff.ly/BXWkoeF
⎈ The Kubernetes package manager Helm has a high-severity Code Injection vulnerability CVE-2025-53547.
🚂 The Conductor open-source microservices workflow orchestrator is vulnerable to a Remote Code Execution #RCE (CVE-2025-26074)
More details: buff.ly/BXWkoeF

July 16, 2025 at 2:42 PM
#LastWeekInAppSec
⎈ The Kubernetes package manager Helm has a high-severity Code Injection vulnerability CVE-2025-53547.
🚂 The Conductor open-source microservices workflow orchestrator is vulnerable to a Remote Code Execution #RCE (CVE-2025-26074)
More details: buff.ly/BXWkoeF
⎈ The Kubernetes package manager Helm has a high-severity Code Injection vulnerability CVE-2025-53547.
🚂 The Conductor open-source microservices workflow orchestrator is vulnerable to a Remote Code Execution #RCE (CVE-2025-26074)
More details: buff.ly/BXWkoeF
Guess what? Like any tech, #MCP isn't immune to flaws.
#CVE-2025-6514 affects NPM's mcp-remote MCP client library versions 0.5.0-0 through 0.1.15, allowing OS command injection via URL authentication – and yes, that means possible #RCE.
Be careful who you connect to!
buff.ly/CMj1UNv
#CVE-2025-6514 affects NPM's mcp-remote MCP client library versions 0.5.0-0 through 0.1.15, allowing OS command injection via URL authentication – and yes, that means possible #RCE.
Be careful who you connect to!
buff.ly/CMj1UNv

July 15, 2025 at 2:42 PM
Guess what? Like any tech, #MCP isn't immune to flaws.
#CVE-2025-6514 affects NPM's mcp-remote MCP client library versions 0.5.0-0 through 0.1.15, allowing OS command injection via URL authentication – and yes, that means possible #RCE.
Be careful who you connect to!
buff.ly/CMj1UNv
#CVE-2025-6514 affects NPM's mcp-remote MCP client library versions 0.5.0-0 through 0.1.15, allowing OS command injection via URL authentication – and yes, that means possible #RCE.
Be careful who you connect to!
buff.ly/CMj1UNv
🚨#CVE-2025-4981 CRITICAL (CVSS=9.9): #Mattermost versions up to 10.5.5, 9.11.15, 10.8.0, 10.7.2, and 10.6.5 are vulnerable to arbitrary file write via path traversal. Authenticated users can exploit this for #RCE by uploading malicious archives. Update to the latest patched versions!
buff.ly/Cz5CPgH
buff.ly/Cz5CPgH

June 25, 2025 at 2:57 PM
🚨#CVE-2025-4981 CRITICAL (CVSS=9.9): #Mattermost versions up to 10.5.5, 9.11.15, 10.8.0, 10.7.2, and 10.6.5 are vulnerable to arbitrary file write via path traversal. Authenticated users can exploit this for #RCE by uploading malicious archives. Update to the latest patched versions!
buff.ly/Cz5CPgH
buff.ly/Cz5CPgH
🚨#CVE-2025-1793: vector store integrations in #AI library llama_index prior to 0.12.28 are vulnerable to SQLi. Attackers can read / write data on affected vector stores by using SQL, potentially leading to unauthorized access to the data of other users. Fixed in llama_index v0.12.28.

June 5, 2025 at 9:08 PM
🚨#CVE-2025-1793: vector store integrations in #AI library llama_index prior to 0.12.28 are vulnerable to SQLi. Attackers can read / write data on affected vector stores by using SQL, potentially leading to unauthorized access to the data of other users. Fixed in llama_index v0.12.28.
🚨#CVE-2025-41232: #SpringSecurity versions 6.4.0 through 6.4.5 Authorization bypass related to private method annotations using Aspects. Look for @EnableMethodSecurity(mode=ASPECTJ) and method-level security annotations on private methods. Fixed in Spring Security 6.4.6.
buff.ly/kIm4Wrd
buff.ly/kIm4Wrd

May 22, 2025 at 1:22 PM
🚨#CVE-2025-41232: #SpringSecurity versions 6.4.0 through 6.4.5 Authorization bypass related to private method annotations using Aspects. Look for @EnableMethodSecurity(mode=ASPECTJ) and method-level security annotations on private methods. Fixed in Spring Security 6.4.6.
buff.ly/kIm4Wrd
buff.ly/kIm4Wrd
Critical #CVE-2025-30215 in #NATSio Server—common for #IoT and distributed cloud-native platforms. Exploit of #vulnerable API leads to product outages, sensitive data leaks, and reputation damage. Update to 2.10.27 / 2.11.1 immediately! See github.com/nats-io/nats... for detail.

April 17, 2025 at 8:55 PM
Critical #CVE-2025-30215 in #NATSio Server—common for #IoT and distributed cloud-native platforms. Exploit of #vulnerable API leads to product outages, sensitive data leaks, and reputation damage. Update to 2.10.27 / 2.11.1 immediately! See github.com/nats-io/nats... for detail.


