
🌐 Chip & binary security testing
www.eshard.com
Come join our #CTF, AngryPangolin, for a chance to win a Binary Ninja license or a Flipper Zero.
#reverseengineering #ios #softwaresecurity

Come join our #CTF, AngryPangolin, for a chance to win a Binary Ninja license or a Flipper Zero.
#reverseengineering #ios #softwaresecurity
🔗 Register here: u.eshard.com/wcUfh
Second session: u.eshard.com/4hGSQ
#webinar #pqc #nistsecurity

🔗 Register here: u.eshard.com/wcUfh
Second session: u.eshard.com/4hGSQ
#webinar #pqc #nistsecurity
eShard contributes its expertise in side-channel and fault-injection analysis to help validate hybrid secure boot architectures.
🌐 Learn more: pq-fortress.eu

eShard contributes its expertise in side-channel and fault-injection analysis to help validate hybrid secure boot architectures.
🌐 Learn more: pq-fortress.eu
We’ll be demonstrating it again at Hardwear.io in the Netherlands this November.
👉 Contact us to order yours today: www.eshard.com

We’ll be demonstrating it again at Hardwear.io in the Netherlands this November.
👉 Contact us to order yours today: www.eshard.com
We’ve added three new hand-wound probes in a deeper cylindrical format, and a brand-new body bias injection (BBI) module.
→ Contact us to pre-order: www.eshard.com/contact

We’ve added three new hand-wound probes in a deeper cylindrical format, and a brand-new body bias injection (BBI) module.
→ Contact us to pre-order: www.eshard.com/contact
Meet HQC, the backup superhero chosen by NIST to defend our AES keys when quantum computers rise.
Learn its origin story (and check our educational Python implementation): eshard.com/posts/superh...
Meet HQC, the backup superhero chosen by NIST to defend our AES keys when quantum computers rise.
Learn its origin story (and check our educational Python implementation): eshard.com/posts/superh...
The lab covers Side-Channel Analysis, Electromagnetic Fault Injection, and voltage and clock glitching.
Read more: eshard.com/posts/esa-es... #hardware #cybersecurity

The lab covers Side-Channel Analysis, Electromagnetic Fault Injection, and voltage and clock glitching.
Read more: eshard.com/posts/esa-es... #hardware #cybersecurity

The lab covers Side-Channel Analysis, Electromagnetic Fault Injection, and voltage and clock glitching.
Read more: eshard.com/posts/esa-es... #hardware #cybersecurity



📩 Apply to the shortlist. u.eshard.com/ios-emulator...
Limited time and spots.
#ios #cybersecurity #emulation

📩 Apply to the shortlist. u.eshard.com/ios-emulator...
Limited time and spots.
#ios #cybersecurity #emulation
We break it down in our latest Expert Review. ➡️ eshard.com/posts/expert...
#pqc #postquantumcryptography #cryptography

We break it down in our latest Expert Review. ➡️ eshard.com/posts/expert...
#pqc #postquantumcryptography #cryptography
10:00 CEST (4 AM EST • 4 PM SGT) → u.eshard.com/webinar-sca-...
17:00 CEST (11 AM EST • 11 PM SGT) → u.eshard.com/webinar-sca-...
#hardware #cybersecurity

10:00 CEST (4 AM EST • 4 PM SGT) → u.eshard.com/webinar-sca-...
17:00 CEST (11 AM EST • 11 PM SGT) → u.eshard.com/webinar-sca-...
#hardware #cybersecurity
Read the guide: eshard.com/posts/window... #windows #emulation #reverseengineering

Read the guide: eshard.com/posts/window... #windows #emulation #reverseengineering
We explored these anti-VM techniques on our latest blog: eshard.com/posts/window...
And how to bypass them.
#reverseengineering #malware

We explored these anti-VM techniques on our latest blog: eshard.com/posts/window...
And how to bypass them.
#reverseengineering #malware
Bringing our Pattern Detector demo (side-channel spotting made easier) and the new ML-KEM (Kyber) starter kits.
Come say hi if you’re around. #pqc



Bringing our Pattern Detector demo (side-channel spotting made easier) and the new ML-KEM (Kyber) starter kits.
Come say hi if you’re around. #pqc
Play for a chance to win a Binary Ninja license or a Flipper Zero.
#CTF #FlipperZero #windows #reverseengineering

Play for a chance to win a Binary Ninja license or a Flipper Zero.
#CTF #FlipperZero #windows #reverseengineering
Our blog post shows how to create a Windows 11 VM and run it in esReverse for full system emulation. → eshard.com/posts/window...
#windows11 #ReverseEngineering #emulation #cybersecurity

Our blog post shows how to create a Windows 11 VM and run it in esReverse for full system emulation. → eshard.com/posts/window...
#windows11 #ReverseEngineering #emulation #cybersecurity
Part 1 • From black screens to first UI
eshard.com/posts/emulat...
Part 2 • From setup to apps and network
eshard.com/posts/emulat...
#ios #iphone #emulator #mobilesec #devsecops
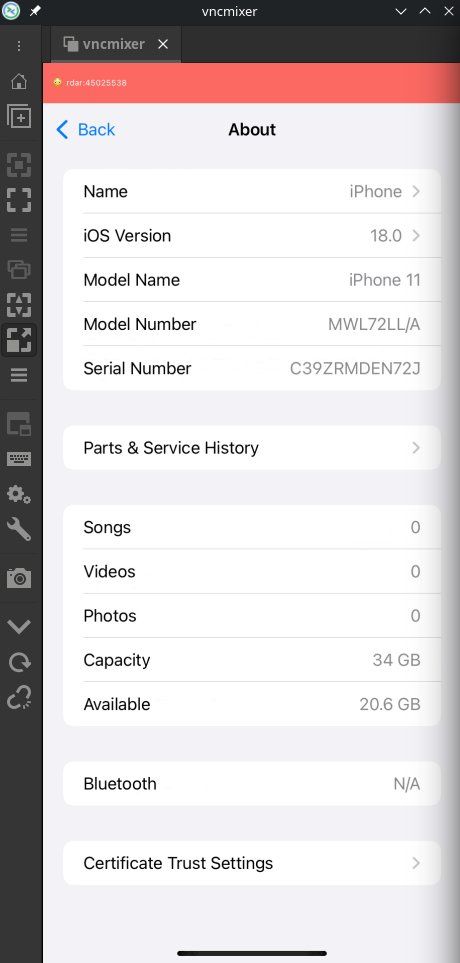
Part 1 • From black screens to first UI
eshard.com/posts/emulat...
Part 2 • From setup to apps and network
eshard.com/posts/emulat...
#ios #iphone #emulator #mobilesec #devsecops
A compact, hands-on lab that guides you through a full side-channel attack on an unprotected ML-KEM (Kyber) MCU implementation. eshard.com/contact
#postquantum #pqc #sidechannel

A compact, hands-on lab that guides you through a full side-channel attack on an unprotected ML-KEM (Kyber) MCU implementation. eshard.com/contact
#postquantum #pqc #sidechannel
On July 10, we're live to show how SCA and FI techniques break schemes like ML-KEM, and how to protect your implementations.
Register:
🔵 11am CEST: pqshield.zoom.us/webinar/regi...
🔵 6pm CEST: pqshield.zoom.us/webinar/regi...

On July 10, we're live to show how SCA and FI techniques break schemes like ML-KEM, and how to protect your implementations.
Register:
🔵 11am CEST: pqshield.zoom.us/webinar/regi...
🔵 6pm CEST: pqshield.zoom.us/webinar/regi...
Register now:
🔵 11am CEST: pqshield.zoom.us/webinar/regi...
🔵 6pm CEST: pqshield.zoom.us/webinar/regi...
#cryptography #cybersecurity #postquantumcryptography #pqc

Register now:
🔵 11am CEST: pqshield.zoom.us/webinar/regi...
🔵 6pm CEST: pqshield.zoom.us/webinar/regi...
#cryptography #cybersecurity #postquantumcryptography #pqc

#hardwaresecurity #cybersecurity

#hardwaresecurity #cybersecurity
We break down the differences in our blog: eshard.com/posts/differ...
#windows #cybersecurity

We break down the differences in our blog: eshard.com/posts/differ...
#windows #cybersecurity


