Building fuzzers @ Interrupt Labs |
Teaching @ Australian National University
https://adrian-herrera.com
www.interruptlabs.co.uk/articles/one...

www.interruptlabs.co.uk/articles/one...
Come and chat to us - we are recruiting across a number of roles in our VR teams!

sure-workshop.org/pa... (paper links out soon)
sure-workshop.org/pa... (paper links out soon)
Why? Because I wanted to test a Pure Go emulator I'm writing against and couldn't get unicorn2 to work on macOS 26. Plus what's going to be faster than Apple's OWN hypervisor 😎
Check it out! 🎉
github.com/blacktop/go-...
Why? Because I wanted to test a Pure Go emulator I'm writing against and couldn't get unicorn2 to work on macOS 26. Plus what's going to be faster than Apple's OWN hypervisor 😎
Check it out! 🎉
github.com/blacktop/go-...




usenix.org/conference/w...
Talks are recorded, and should be online in a few weeks.

usenix.org/conference/w...
Talks are recorded, and should be online in a few weeks.
We built a format string exploit for the TC500 smart cam. It didn’t get used, but it made for a fun case study.
blog.infosectcbr.com.au/2025/08/01/e...

We built a format string exploit for the TC500 smart cam. It didn’t get used, but it made for a fun case study.
blog.infosectcbr.com.au/2025/08/01/e...
It explores the heap to find interesting objects and corrupts them in a deterministic way using V8's memory corruption API. Happy fuzzing!

It explores the heap to find interesting objects and corrupts them in a deterministic way using V8's memory corruption API. Happy fuzzing!
Talk by Kees Cook about the relevance of various Linux kernel vulnerability classes and the mitigations that address them.
Video: www.youtube.com/watch?v=c_Nx...
Slides: static.sched.com/hosted_files...
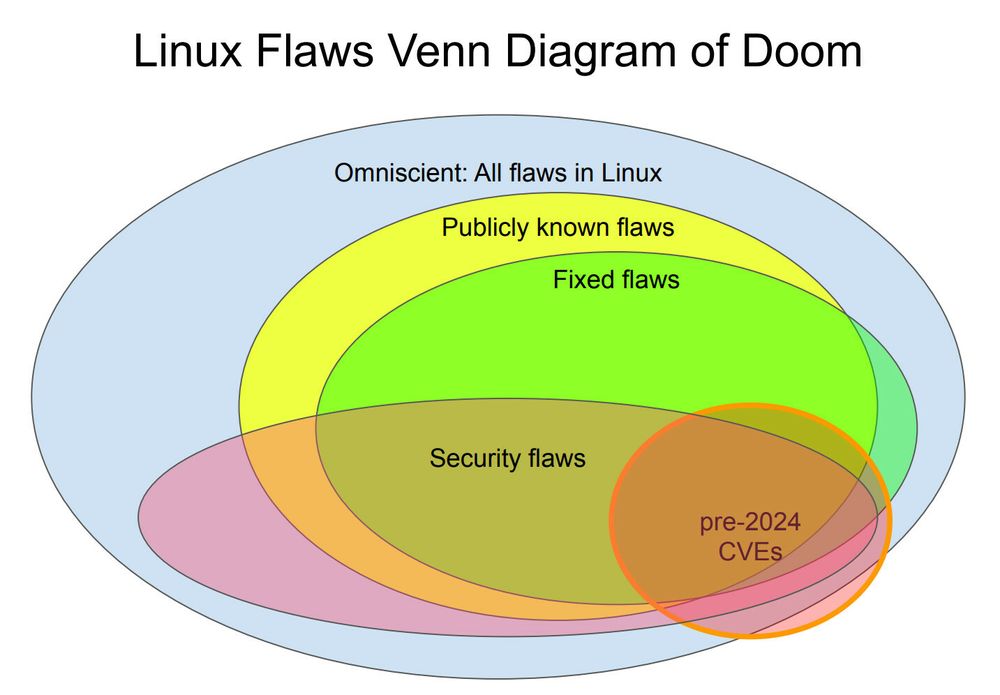
Talk by Kees Cook about the relevance of various Linux kernel vulnerability classes and the mitigations that address them.
Video: www.youtube.com/watch?v=c_Nx...
Slides: static.sched.com/hosted_files...
https://qriousec.github.io/post/cve-2023-52927/
https://qriousec.github.io/post/cve-2023-52927/
Code: github.com/sandialabs/c...
Talk (via @krismicinski.bsky.social): youtu.be/3ec9VfMUVa8?...
Code: github.com/sandialabs/c...
Talk (via @krismicinski.bsky.social): youtu.be/3ec9VfMUVa8?...
1/n
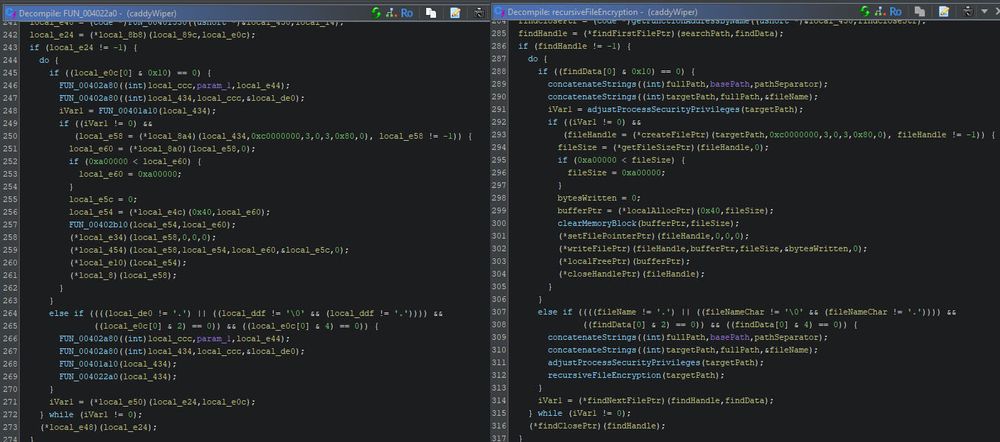
1/n
Sounds impossible-but it's actually really simple. In fact, our measure of "correctness" called incoherence can be estimated (PAC guarantees).
arxiv.org/abs/2507.00057

Sounds impossible-but it's actually really simple. In fact, our measure of "correctness" called incoherence can be estimated (PAC guarantees).
arxiv.org/abs/2507.00057
https://starlabs.sg/blog/2025/06-solo-a-pixel-6-pro-story-when-one-bug-is-all-you-need/

https://starlabs.sg/blog/2025/06-solo-a-pixel-6-pro-story-when-one-bug-is-all-you-need/
The "Havoc Paradox" is about the relationship between byte-level fuzzer mutations and their effect on the inputs produced by generators for structured strings (e.g. XML/SQL). Can disruptive mutations be controlled? Should they be? Find out.
📄 dl.acm.org/doi/pdf/10.1...

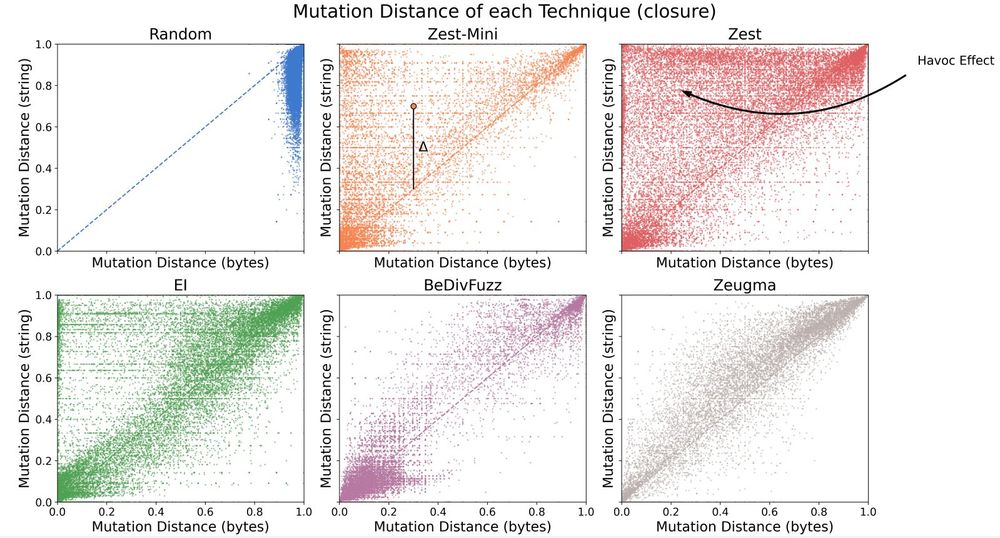
The "Havoc Paradox" is about the relationship between byte-level fuzzer mutations and their effect on the inputs produced by generators for structured strings (e.g. XML/SQL). Can disruptive mutations be controlled? Should they be? Find out.
📄 dl.acm.org/doi/pdf/10.1...
creation of DWARF files. Additionally, I present two plugins designed to export
program information from Ghidra and BinaryNinja into a DWARF file.
lief.re/blog/2025-05...
(Bonus: DWARF file detailing my reverse engineering work on DroidGuard)

creation of DWARF files. Additionally, I present two plugins designed to export
program information from Ghidra and BinaryNinja into a DWARF file.
lief.re/blog/2025-05...
(Bonus: DWARF file detailing my reverse engineering work on DroidGuard)

Bin2Wrong creates binaries by mutating source, compiler, optimizations, and format—revealing 48 new bugs in 7 decompilers! 💪
Bin2Wrong creates binaries by mutating source, compiler, optimizations, and format—revealing 48 new bugs in 7 decompilers! 💪
What's new:
- New APIs for working with IDBs, segments, and more
- Rust 2024 support
- New homepage: idalib.rs
H/T to our contributors @yeggor.bsky.social & @raptor.infosec.exchange.ap.brid.gy
github.com/binarly-io/i...
What's new:
- New APIs for working with IDBs, segments, and more
- Rust 2024 support
- New homepage: idalib.rs
H/T to our contributors @yeggor.bsky.social & @raptor.infosec.exchange.ap.brid.gy
github.com/binarly-io/i...
sam4k.com/page-table-k...

sam4k.com/page-table-k...
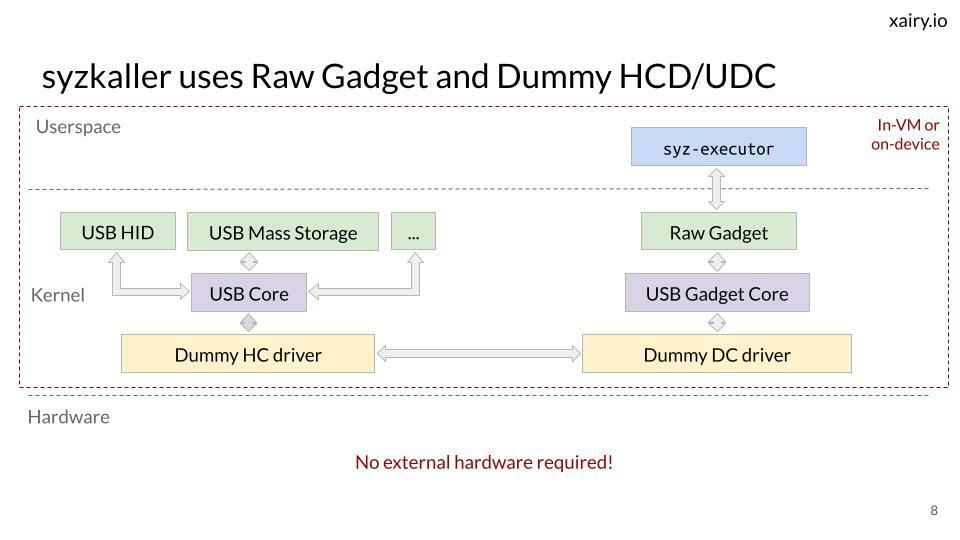
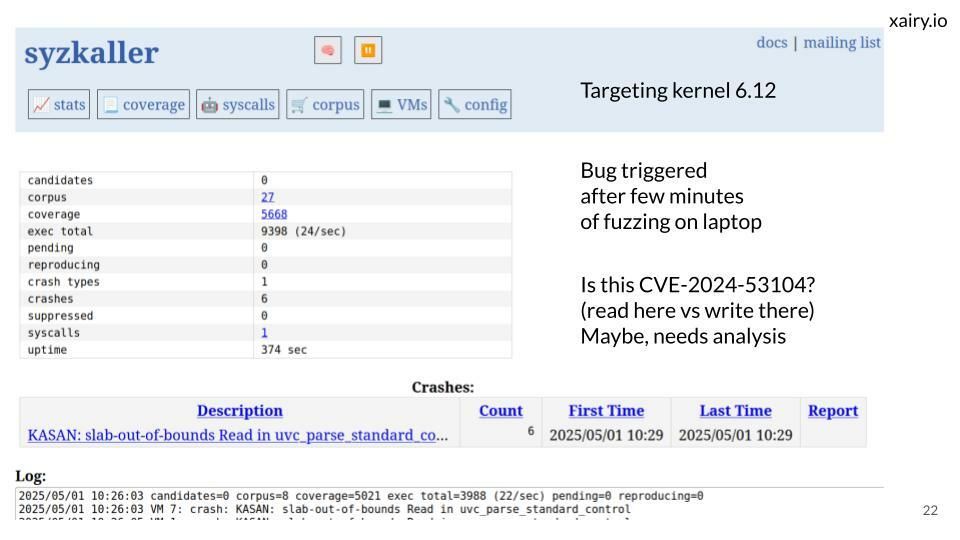
Includes a demonstration of how to rediscover CVE-2024-53104, an out-of-bounds bug in the USB Video Class driver.
Slides: docs.google.com/presentation...

Includes a demonstration of how to rediscover CVE-2024-53104, an out-of-bounds bug in the USB Video Class driver.
Slides: docs.google.com/presentation...
blacktop.github.io/ipsw/docs/gu...
blacktop.github.io/ipsw/docs/gu...


